Doctor Web’s Q2 2024 virus activity review
July 1, 2024
Users whose files were affected by encoder trojans most commonly encountered Trojan.Encoder.3953, Trojan.Encoder.35534, and Trojan.Encoder.26996.
Regarding Android mobile devices, the most commonly detected threats were Android.HiddenAds adware trojans, Android.FakeApp malicious programs, and Android.Spy spyware trojans. At the same time, our virus analysts discovered more threats on Google Play.
Principal trends in Q2 2024
- Adware trojans and unwanted adware programs were highly active
- Malicious scripts and all sorts of phishing documents predominated in malicious email traffic
- Android.HiddenAds adware trojans again were the most commonly detected threats for Android devices
According to Doctor Web’s statistics service
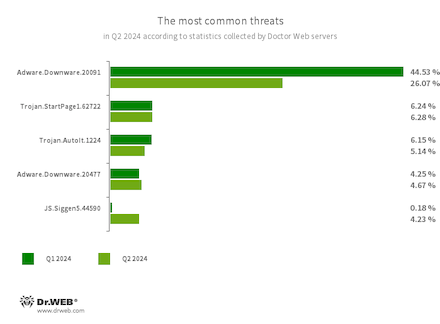
The most common threats in Q2 2024:
- Adware.Downware.20091
- Adware.Downware.20477
- Adware that often serves as an intermediary installer of pirated software.
- Trojan.StartPage1.62722
- A malicious program that can modify the home page in the browser settings.
- Trojan.AutoIt.1224
- The detection name for a packed version of the Trojan.AutoIt.289 malicious app, written in the AutoIt scripting language. This trojan is distributed as part of a group of several malicious applications, including a miner, a backdoor, and a self-propagating module. Trojan.AutoIt.289 performs various malicious actions that make it difficult for the main payload to be detected.
- JS.Siggen5.44590
- Malicious code added to the es5-ext-main public JavaScript library. It shows a specific message if the package is installed on a server with a time zone of Russian cities.
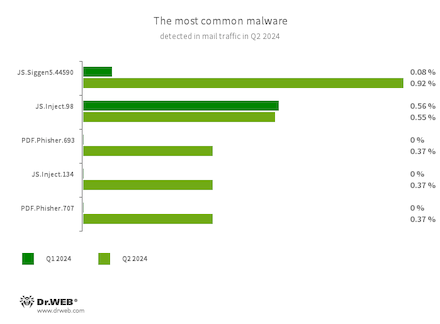
Statistics for malware discovered in email traffic
- JS.Siggen5.44590
- Malicious code added to the es5-ext-main public JavaScript library. It shows a specific message if the package is installed on a server with a time zone of Russian cities.
- JS.Inject
- A family of malicious JavaScripts that inject a malicious script into the HTML code of webpages.
- PDF.Phisher.707
- PDF.Phisher.693
- PDF documents used in phishing newsletters.
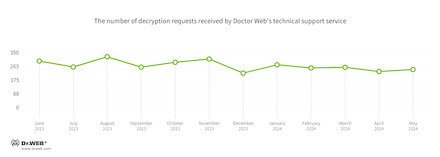
Encryption ransomware
The dynamics of the requests we received to decrypt files affected by encoder trojans:
The most common encoders of Q2 2024:
- Trojan.Encoder.3953 — 18.43%
- Trojan.Encoder.35534 — 9.22%
- Trojan.Encoder.26996 — 8.75%
- Trojan.Encoder.35067 — 2.07%
- Trojan.Encoder.37369 — 1.61%
Dangerous websites
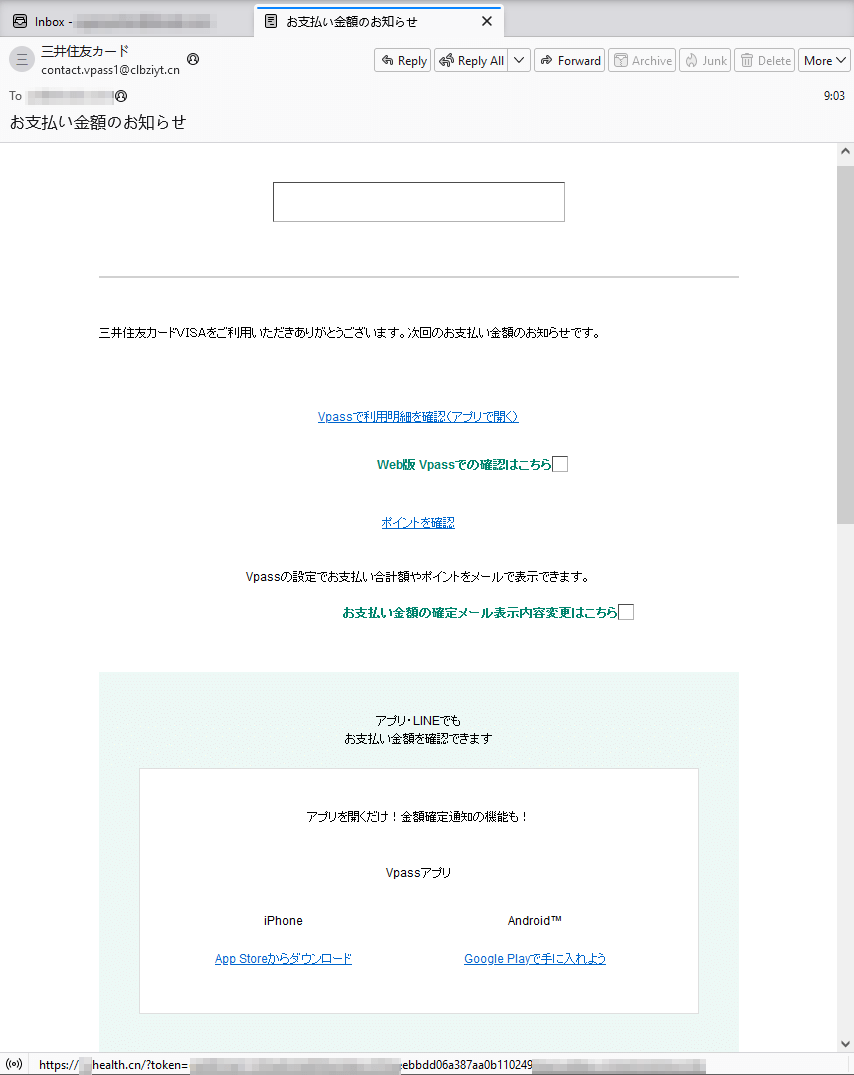
In Q2 2024, Doctor Web’s specialists detected a mass-mailing fraud campaign targeting users from Japan. Fraudsters pretending to act on behalf of one of the banks informed potential victims about a certain purchase they’d made and offered them the chance to see the details of this “payment” by clicking on the provided link. But, in reality, this link led to a phishing Internet resource.
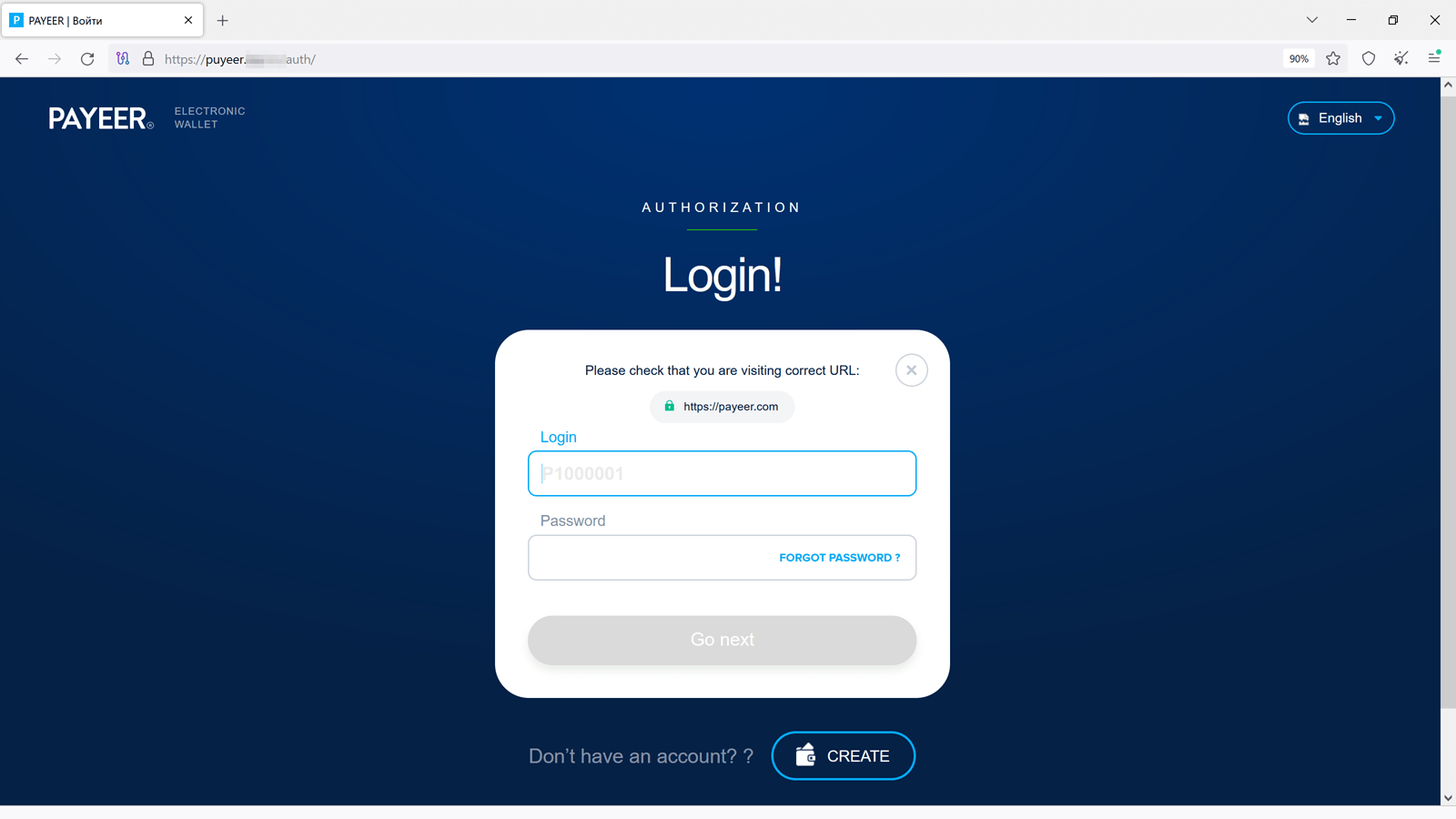
Among the fraudulent websites found in Q2 2024, our Internet analysts also noticed phishing resources that imitated the appearance of genuine e-wallet sites, such as Payeer. With their help, threat actors tried to steal users’ authentication data.
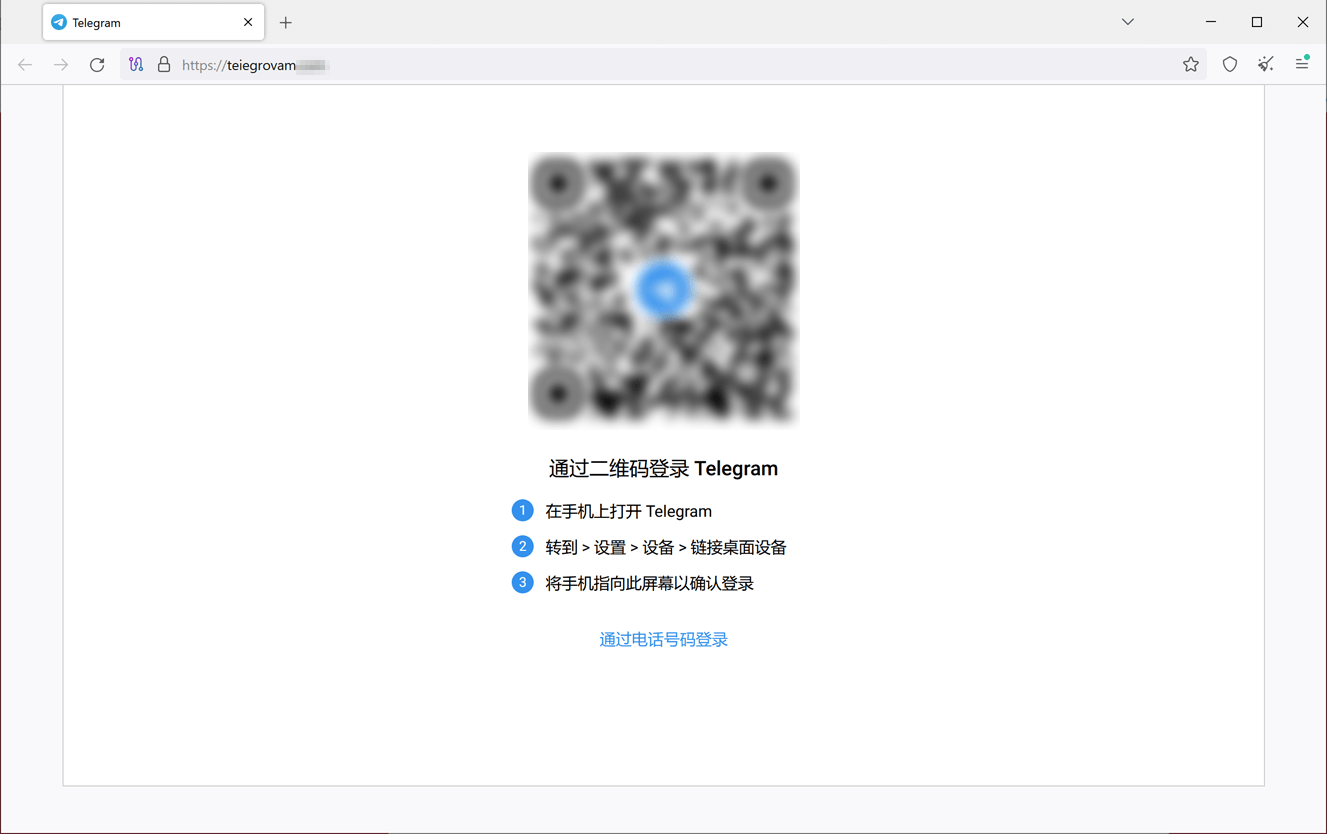
Moreover, cybercriminals are not abandoning their attempts to gain access to people’s accounts from various messengers. For this, they utilize fake login forms. Below is an example of one such phishing site where potential victims are asked to log in to Telegram via a QR code or a phone number. If a potential victim agrees, their login data will end up in the attackers’ hands.
At the same time, our specialists continue to detect fraudulent sites that target Russian-speaking users. Among these, sites that offer potential victims supposedly free lottery tickets are still common. On such sites, potential victims are told that they can get a lottery ticket as a “gift” that ultimately ends up being a “winner”. To “receive” the prize, victims must provide their bank card details or pay some commission or custom to have the non-existent prize “transferred” to their bank account.
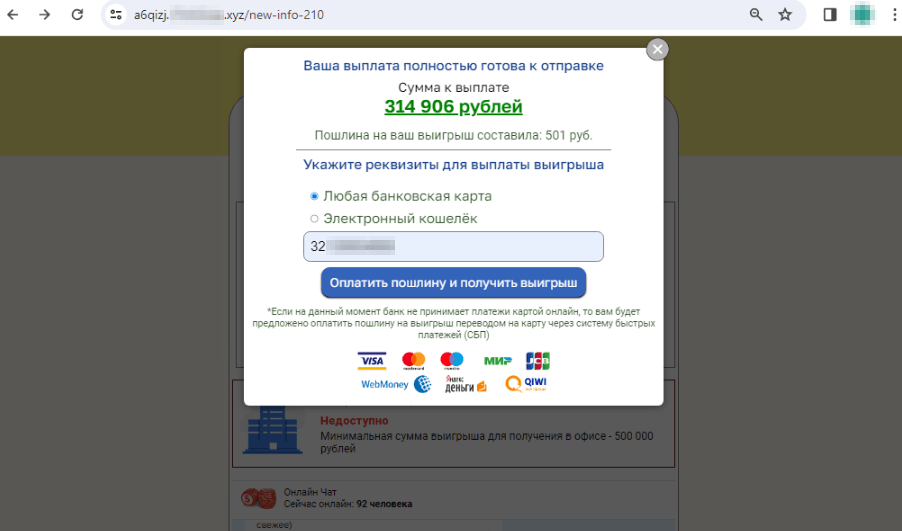
An example of one such scam website is shown below. First, it simulates “free” lottery ticket registration and then allegedly shows an online broadcast of the draw:
The user “wins” 314.906 rubles, but to “receive” their winnings, they must provide bank card details and pay a “fee” of 501 rubles to have the money “transferred”:
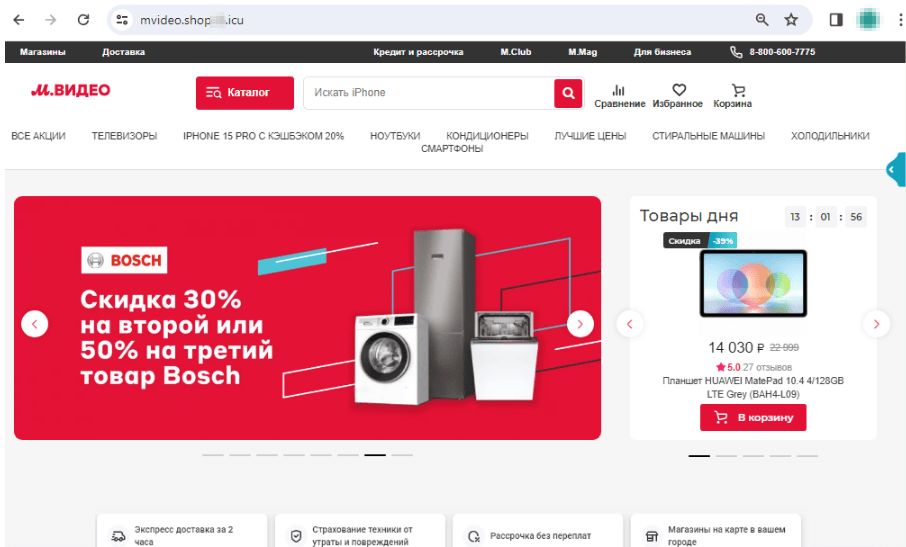
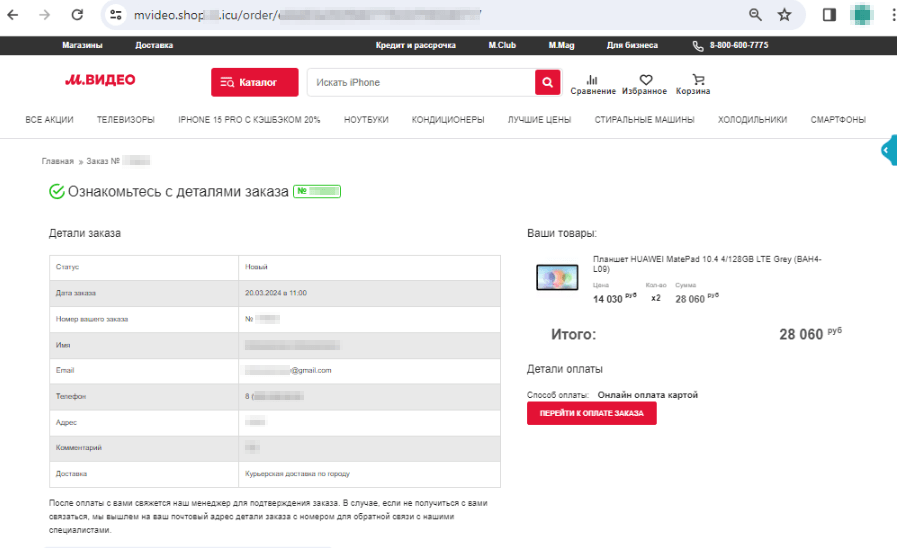
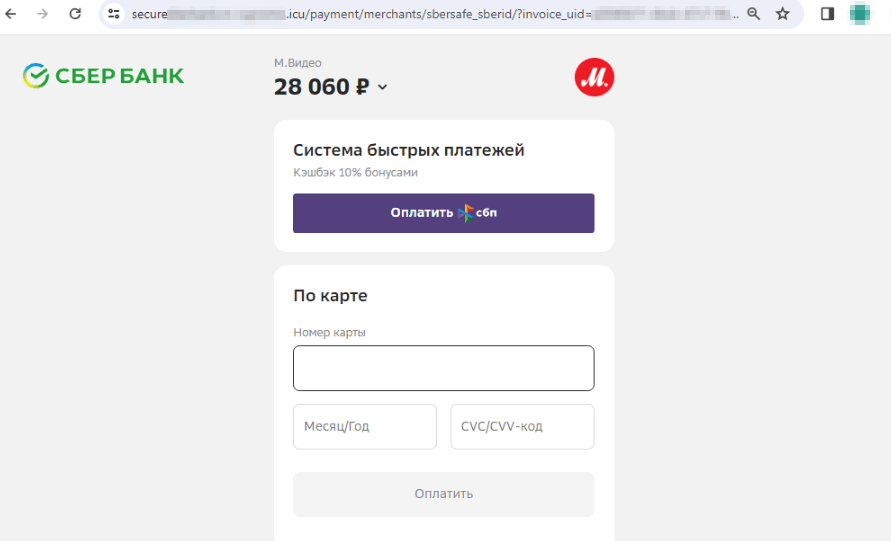
Copycat websites of online stores are still another popular scheme among scammers. These include fake sites of electronics and home appliances stores. Cybercriminals lure potential victims with “discounts”, “coupons”, and all sorts of “promotions”, offering them popular goods for sale at lower prices. When placing an “order” on such sites, users are usually asked to pay via an online bank or a bank card. However, our specialists noticed that fraudsters have also begun including the Faster Payments System (“Система быстрых платежей”, “СБП”, or “SBP”) as an alternative payment method.
The screenshots below show an example of one such fake website that imitates an electronics retailer’s real web resource:
The potential victim places an order for a “product” that is supposedly being offered at a discount:
The Faster Payments System is offered to the user as one of the payment methods for this “order”:
Malicious and unwanted programs for mobile devices
According to detection statistics collected by Dr.Web for Android, in Q2 2024, Android.HiddenAds adware trojans were most commonly detected on protected devices. They were followed by Android.FakeApp malicious applications. The third most common programs were spyware trojans from the Android.Spy family.
At the same time, all sorts of threats were again found on Google Play. Among them were more Android.FakeApp trojans, an unwanted Program.FakeMoney.11 app, and also the Android.Harly.87 trojan, which subscribed users to paid services.
The following Q2 2024 events involving mobile malware are the most noteworthy:
- Android.HiddenAds adware trojans remained the most active threat,
- More threats were detected on Google Play.
To find out more about the security-threat landscape for mobile devices in Q2 2024, read our special overview.