Doctor Web’s April 2023 virus activity review
June 14, 2023
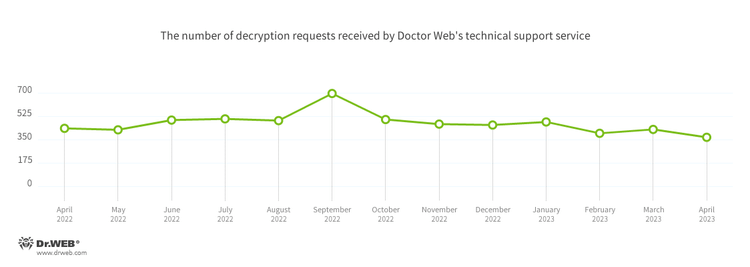
The number of user requests to decrypt files affected by encoder trojans decreased by 13.75%, compared to the previous month. Victims of encoder trojans were once again most frequently targeted by Trojan.Encoder.26996, Trojan.Encoder.3953, and Trojan.Encoder.35534 ransomware.
Over the course of April, a large number of threats were discovered on Google Play. Among them were trojans from the Android.FakeApp family, which are used in fraudulent schemes, and a malicious app from the Android.Joker family that subscribed victims to paid services.
Principal trends in April
- A decrease in the total number of detected threats
- A decrease in the number of user requests to decrypt files affected by encoder trojans
- More malicious applications found on Google Play
According to Doctor Web’s statistics service
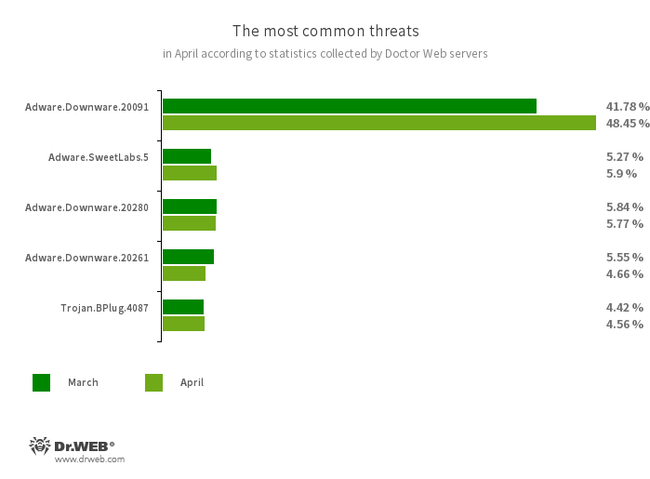
The most common threats of the month:
- Adware.Downware.20091
- Adware.Downware.20280
- Adware.Downware.20261
- Adware that often serves as an intermediary installer of pirated software.
- Adware.SweetLabs.5
- An alternative app store and an add-on for Windows GUI (graphical user interface) from the creators of “OpenCandy” adware.
- Trojan.BPlug.4087
- The detection name for a malicious component of the WinSafe browser extension. This component represents a JavaScript file that displays intrusive ads in browsers.
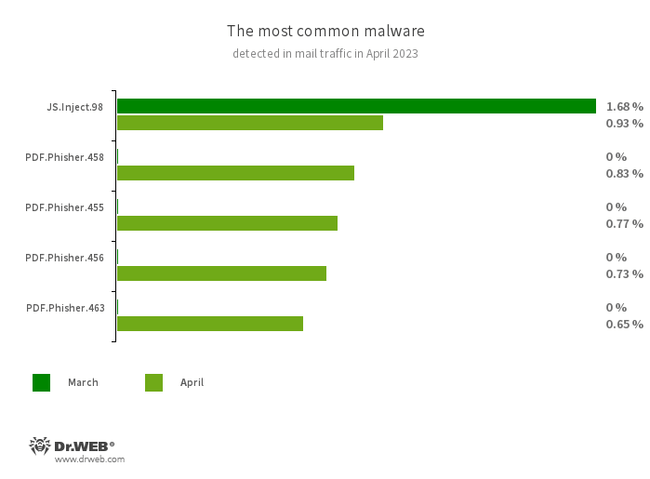
Statistics for malware discovered in email traffic
- JS.Inject
- A family of malicious JavaScripts that inject a malicious script into the HTML code of webpages.
- PDF.Phisher.455
- PDF.Phisher.456
- PDF.Phisher.458
- PDF.Phisher.463
- PDF documents used in phishing newsletters.
Encryption ransomware
In April, the number of requests to decrypt files damaged by encoder trojans decreased by 13.75%, compared to March.
The most common encoders of April:
- Trojan.Encoder.26996 — 24.31%
- Trojan.Encoder.3953 — 19.92%
- Trojan.Encoder.35534 — 4.38%
- Trojan.Encoder.35209 — 3.59%
- Trojan.Encoder.11539 — 3.19%
Dangerous websites
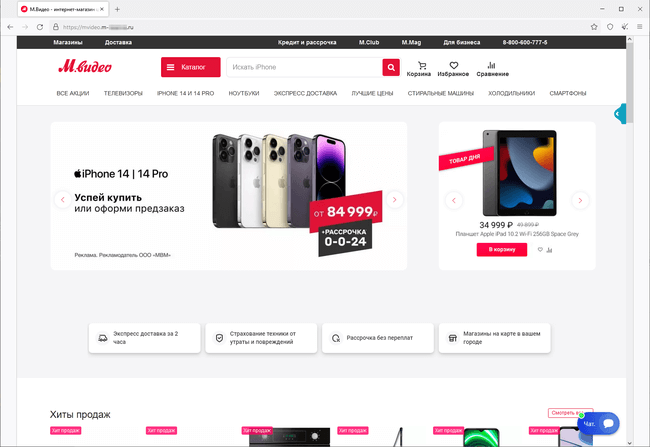
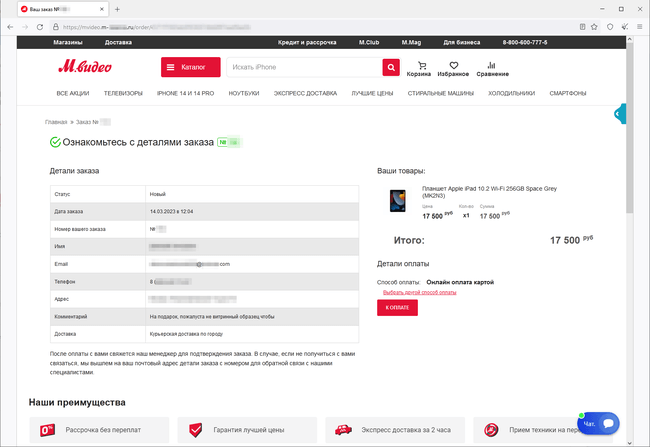
In April, Internet fraudsters kept trying to lure users to phishing websites such as fake versions of online stores. For Russian users, attackers again organized spam campaigns with emails offering fake discount coupons that were allegedly from the M.Video store.
To “purchase” products they liked, visitors to these sites had to provide personal information and bankcard data. In reality though, the victims of this scheme only exposed their personal information to the fraudsters and risked losing money by “paying” for goods that did not exist.
Below is an example of a spam email. It contains fake information about a discount-related promo code and a link to a copycat website of the store:
Examples of pages of a phishing site that simulates the look of the real online store’s website are shown below. Visitors are asked to provide personal information and “pay” for the order.
Malicious and unwanted programs for mobile devices
According to the detection statistics collected by Dr.Web for Android, in April, adware trojans were again among the most widespread Android threats. Compared to March, users were attacked by ransomware and banking trojans more often. At the same time, the activity of spyware trojans decreased.
During April, other threats were detected on Google Play. Among them were fake programs from the Android.FakeApp family, which are used in various fraudulent schemes, and a member of the Android.Joker trojan family that subscribed victims to paid services.
The following April events involving mobile malware are the most noteworthy:
- Adware-displaying trojans remain among the most common Android threats.
- An increase in the activity of banking trojans and ransomware.
- More threats are being distributed via Google Play.
Find out more about security threat landscape for mobile devices in April in our special overview.
[% END %]