Doctor Web’s January 2023 review of virus activity on mobile devices
March 2, 2023
Compared to the previous month, banking and ransom trojan activity also increased. The former were detected 2.63% more often, and the latter 20.71%. At the same time, a minor decrease in spyware activity was observed.
During the course of the month, Doctor Web's virus laboratory uncovered many new threats on the Google Play catalog. These included fraudulent apps and trojan software that subscribed users to paid services.
PRINCIPAL TRENDS IN JANUARY
- An increase in adware trojan activity
- An increase in banking trojan and ransom malware activity
- A decrease in spyware activity
- The emergence of new threats on Google Play
According to statistics collected by Dr.Web for Android
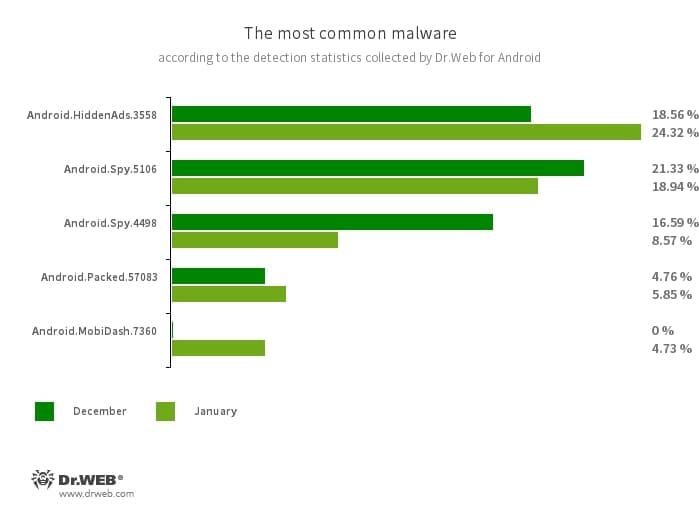
- Android.HiddenAds.3558
- A trojan designed to display intrusive ads. Trojans of this family are often distributed as popular and harmless applications. In some cases, other malware can install them in the system directory. When these infect Android devices, they typically conceal their presence from the user. For example, they “hide” their icons from the home screen menu.
- Android.Spy.5106
- Android.Spy.4498
- The detection name for different variants of the trojan that represents modified versions of unofficial WhatsApp messenger mods. This malicious program can steal the contents of notifications and offer users other apps from unknown sources for installation. And when such a modified messenger is used, it can also display dialog boxes with remotely configurable content.
- Android.Packed.57083
- The detection name for malicious applications protected with an ApkProtector software packer. Among them are banking trojans, spyware, and other malicious software.
- Android.MobiDash.7360
- A trojan that displays obnoxious ads. It is a special software module that developers incorporate into applications.
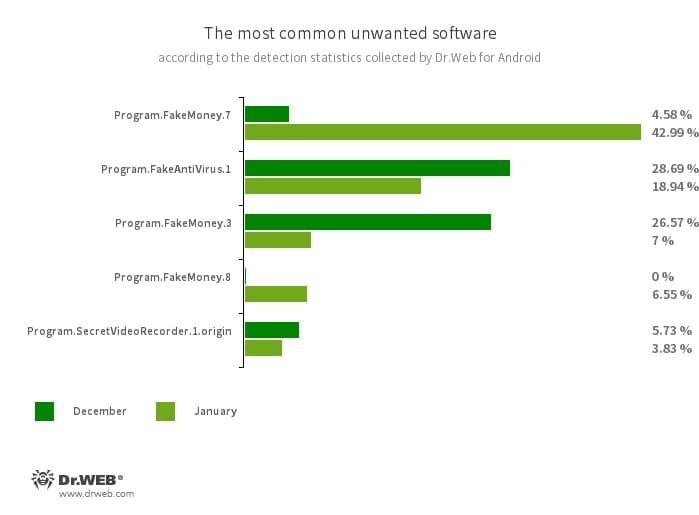
- Program.FakeMoney.7
- Program.FakeMoney.3
- Program.FakeMoney.8
- The detection name for Android applications that allegedly allow users to earn money by watching video clips and ads. These apps make it look as if rewards are accruing for completed tasks. To withdraw their “earnings”, users allegedly have to collect a certain sum. But even if they succeed, in reality they cannot get any real payments.
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of nonexistent threats, mislead them, and demand that they purchase the software’s full version.
- Program.SecretVideoRecorder.1.origin
- The detection name for various modifications of an application that is designed to record videos and take photos in the background using built-in Android device cameras. It can operate covertly by allowing notifications about ongoing recordings to be disabled. It also allows an app’s icon and name to be replaced with fake ones. This functionality makes this software potentially dangerous.
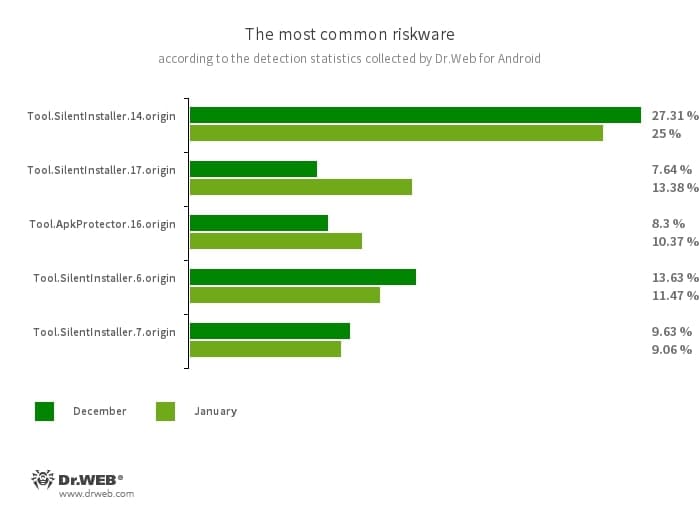
- Tool.SilentInstaller.14.origin
- Tool.SilentInstaller.17.origin
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.7.origin
- Riskware platforms that allow applications to launch APK files without installing them. They create a virtual runtime environment that does not affect the main operating system.
- Tool.ApkProtector.16.origin
- The detection name for Android apps protected by the ApkProtector software packer. This packer is not malicious in itself, but cybercriminals can use it when creating malware and unwanted applications to make it more difficult for anti-virus software to detect them.
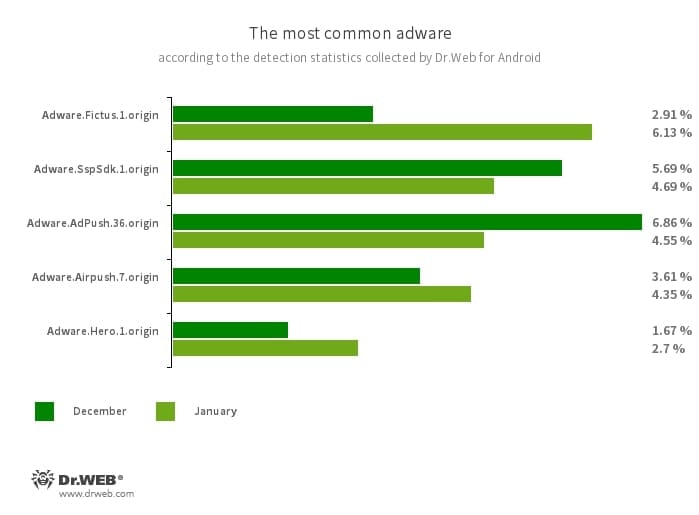
- Adware.Fictus.1.origin
- An adware module which malicious actors embed into the cloned versions of popular Android games and applications. Its incorporation is performed through a specialized net2share packer. Copies of software created this way are then distributed through various software catalogs. When installed on Android devices, such apps and games display obnoxious ads.
- Adware.SspSdk.1.origin
- A specialized advertizing software module which can be embedded into Android apps. It displays ads when host applications are not being used and their windows are closed. As a result, users have a hard time identifying the source of such intrusive behavior on their devices.
- Adware.AdPush.36.origin
- A member of a family of adware modules that can be built into Android apps. It displays notifications containing ads that mislead users. For example, such notifications can look like messages from the operating system. In addition, modules of this family collect a variety of confidential data and are able to download other apps and initiate the process of their installation.
- Adware.Airpush.7.origin
- A member of adware modules that can be built into Android apps and display various ads. Depending on the modules’ version and modification, these can be notifications containing ads, pop-up windows or banners. Malicious actors often use these modules to distribute malware by offering their potential victims diverse software for installation. Moreover, such modules collect personal information and send it to a remote server.
- Adware.Hero.1.origin
- The detection name for one of the components of advertizing applications that display unwanted ads in the form of push notifications, as well as on-screen banners. Such modules are also able to install and uninstall applications if the necessary system permissions are available.
Threats on Google Play
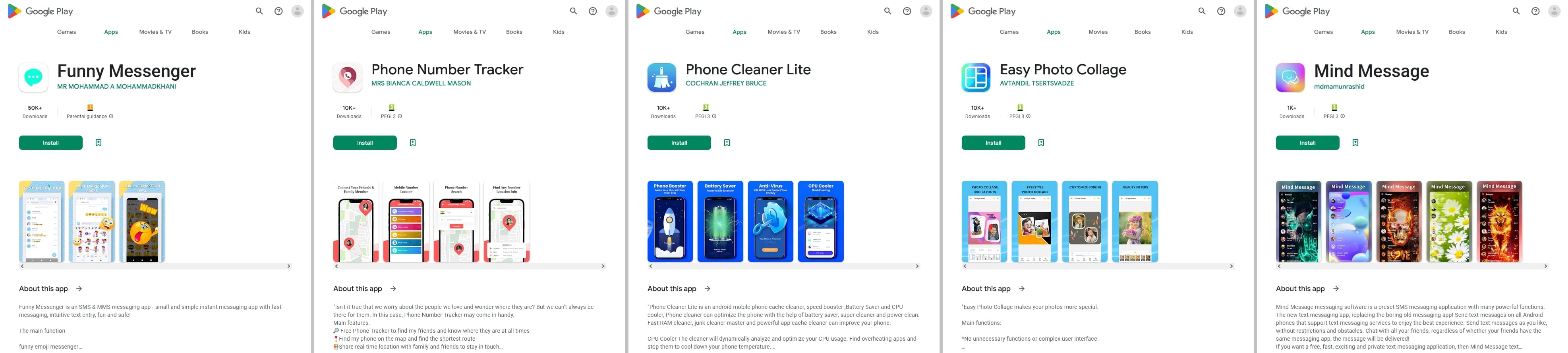
In January 2023, Doctor Web’s virus laboratory uncovered many new threats on the Google Play catalog. Among them were multi-component trojan applications from the Android.Joker and Android.Harly families. They are similar in functionality and subscribe victims to paid services. The former download additional modules from the Internet, while the latter typically already have encrypted modules in their file resources. For example, Android.Joker.1991 was distributed under the guise of an application called “Phone Number Tracker”, which allegedly could allow the location of other mobile subscribers to be tracked using information on their mobile phone numbers. Dubbed Android.Joker.1998, another malware was hiding in the “Phone Cleaner Lite” system-optimization tool. The Android.Joker.1999 and Android.Joker.2008 trojans were being passed off by cybercriminals as SMS messengers called “Funny Messenger” and “Mind Message”. And when users installed image-editing software called “Easy Photo Collage”, they were actually dealing with the Android.Joker.2000 trojan.
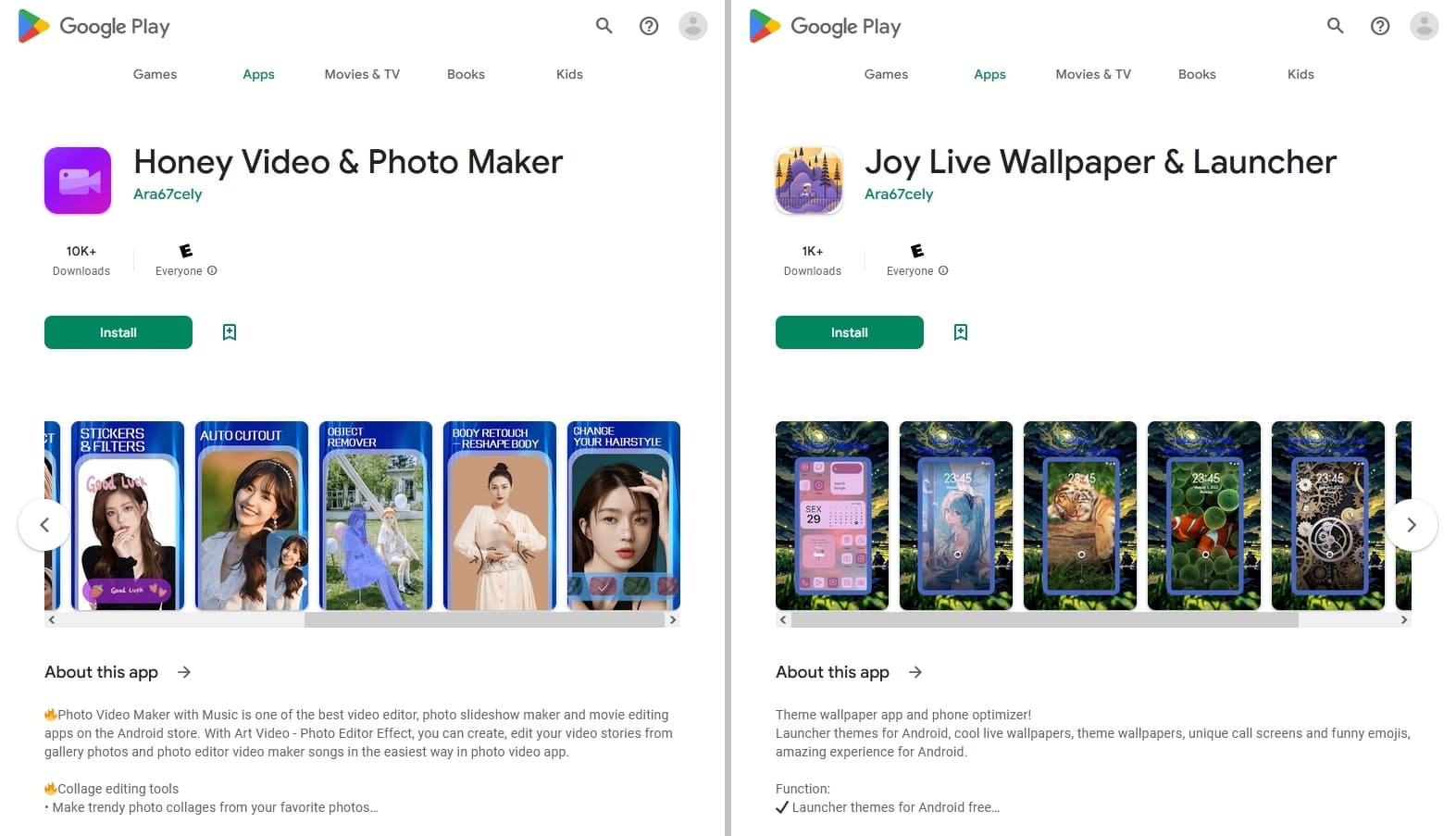
In turn, the Android.Harly.13 and Android.Harly.25 trojans were hiding in the “Honey Video & Photo Maker” video-editing software and the “Joy Live Wallpaper & Launcher” alternative launcher, respectively.
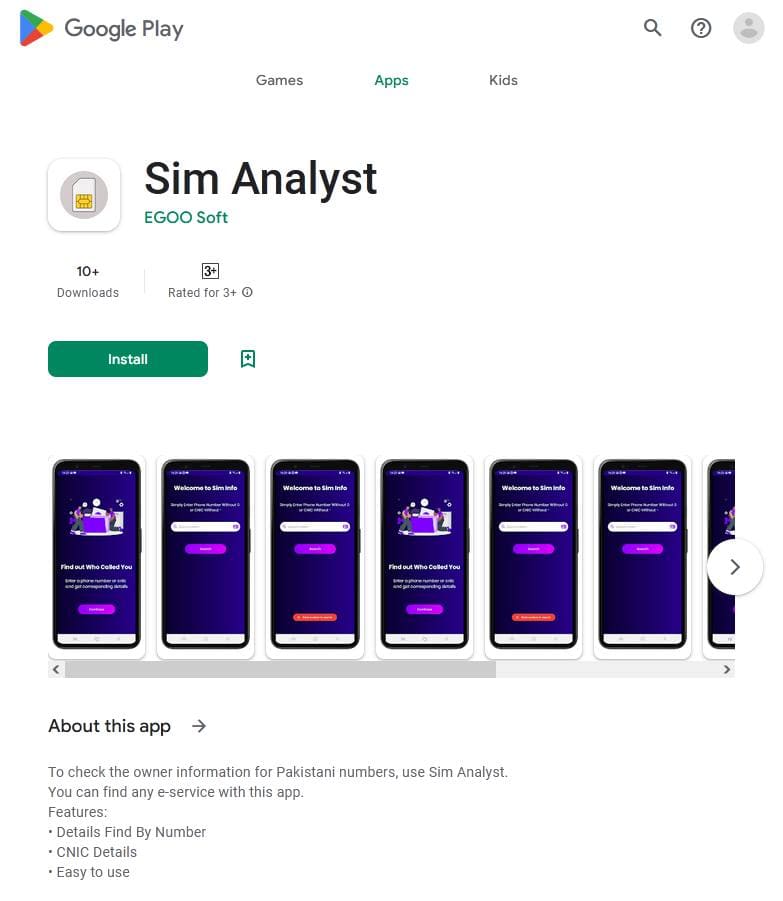
Another discovered threat was an app called “Sim Analyst”, which Pakistani users allegedly could utilize to search for information on other subscribers. In reality, under the guise of this instrument, malicious actors were distributing spyware based on a RAT tool called AhMyth Android Rat. This trojan app was added to the Dr.Web virus database as Android.Spy.1092.origin.
In its base form, the AhMyth Android Rat spyware tool has rich functionality. For example, it allows a device’s location to be tracked, photos to be taken via its built-in camera and the surroundings to be recorded via its microphone. It also can intercept SMS and obtain information on phone calls and user contacts stored in the phonebook. However, due to limitations, apps distributed via the Google Play catalog have restricted access to certain sensitive features, and so did this version of the spyware. Thus, it could track the device location, hijack the contents of notifications, and steal various media files, like photos and videos, as well as files that were transferred via messengers and stored locally on a device.
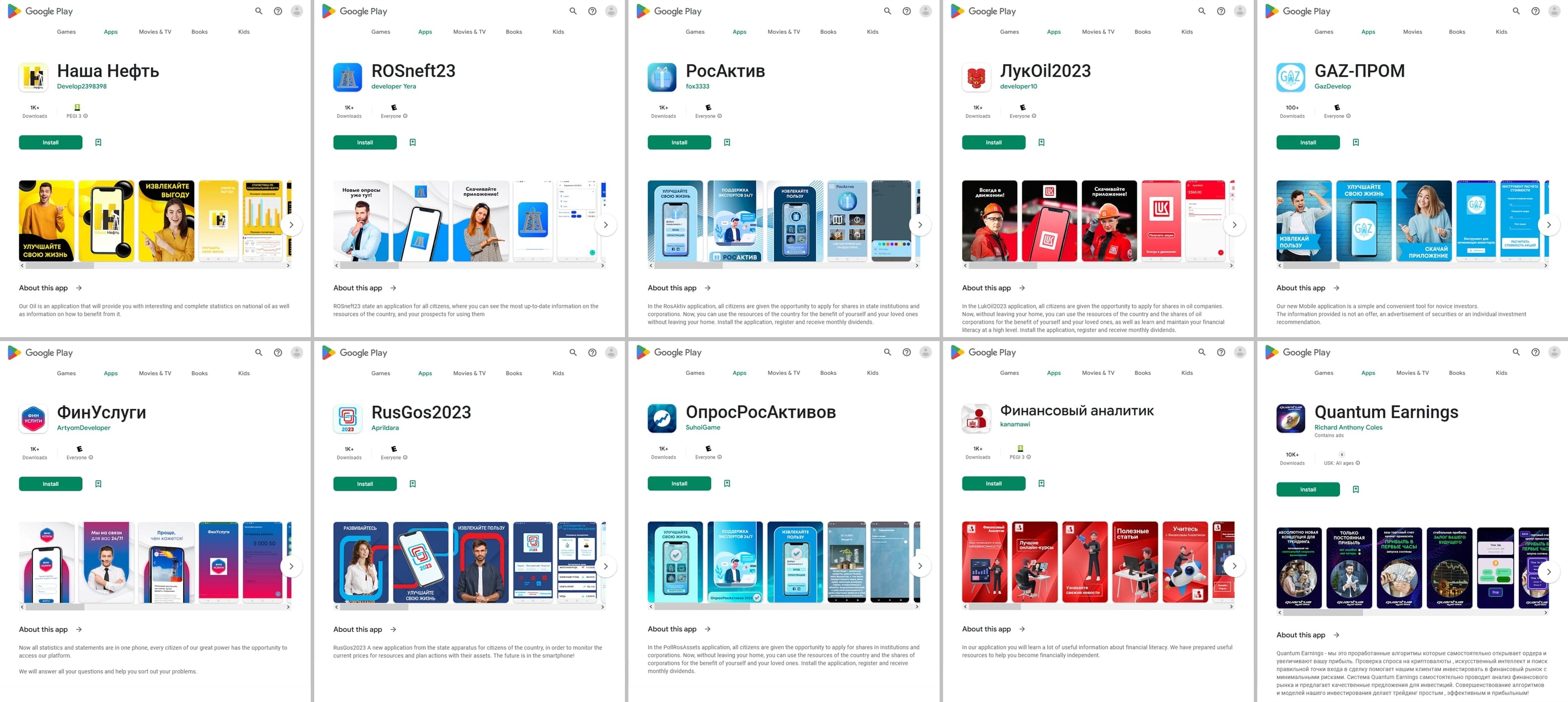
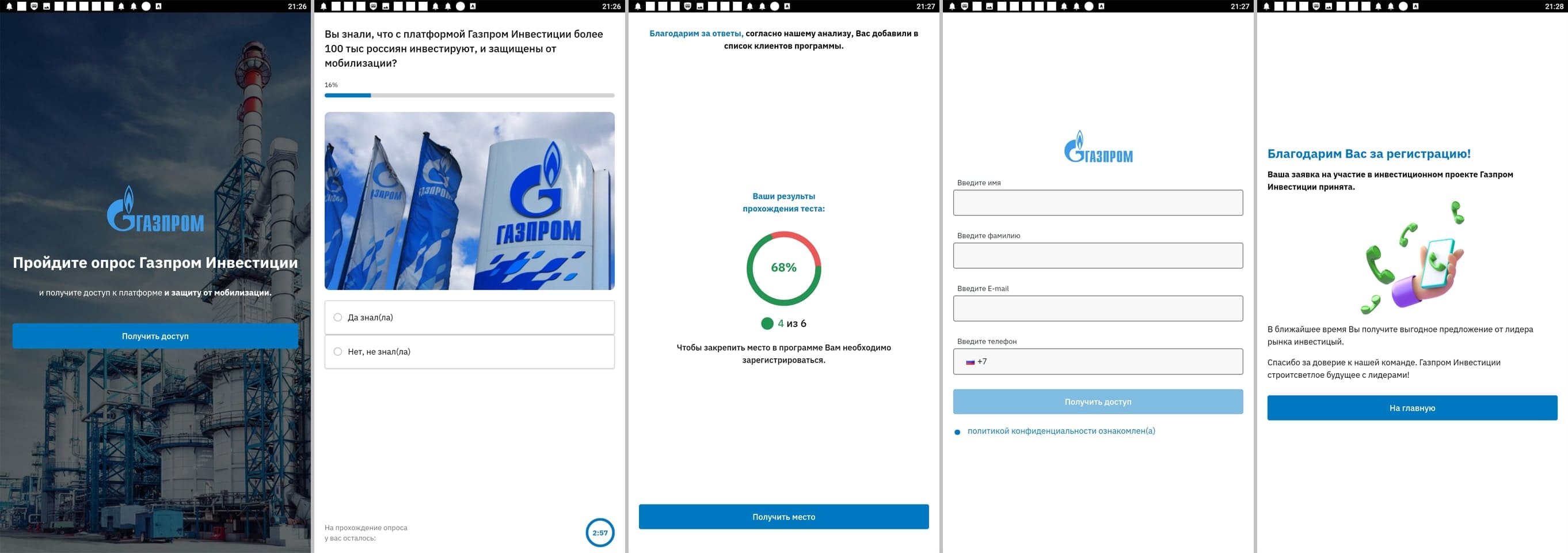
In addition, our specialists discovered over two dozen fraudulent apps from the Android.FakeApp malware family. Threat actors used those to execute various scam schemes. They were distributed under the guise of a variety of software and, upon a remote server’s command, could load different websites, including phishing ones.
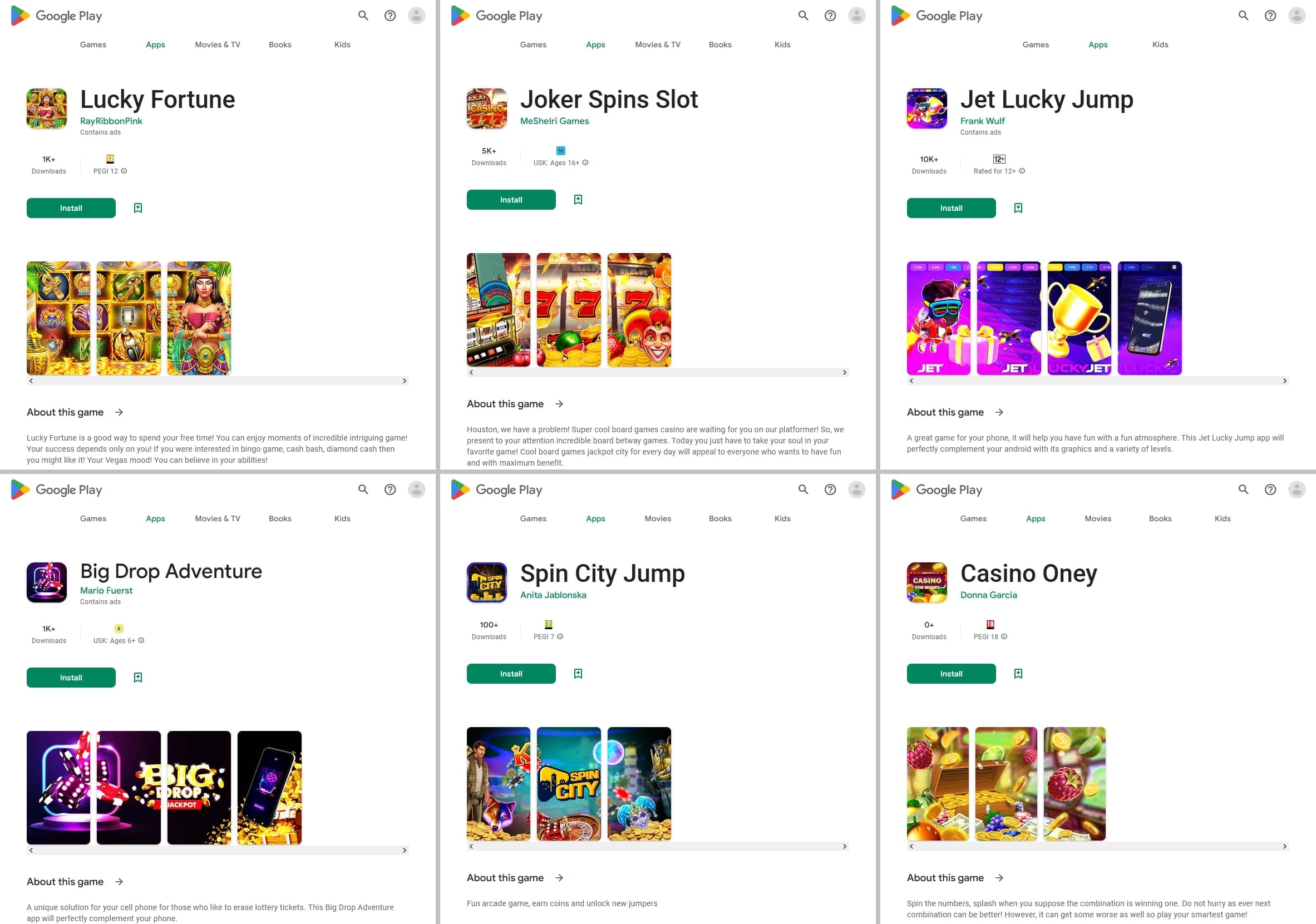
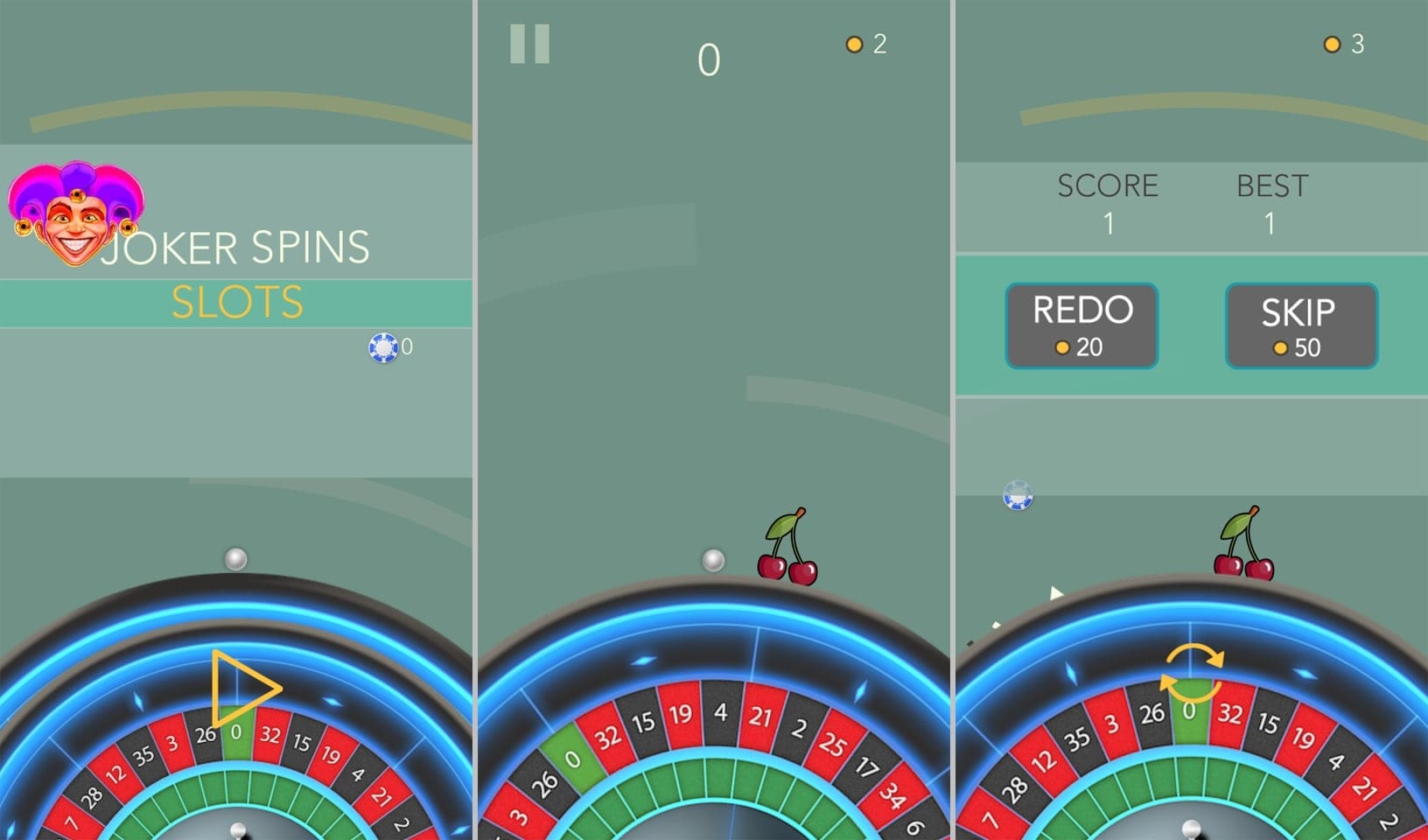
Some of them were passed off as games, as shown below:
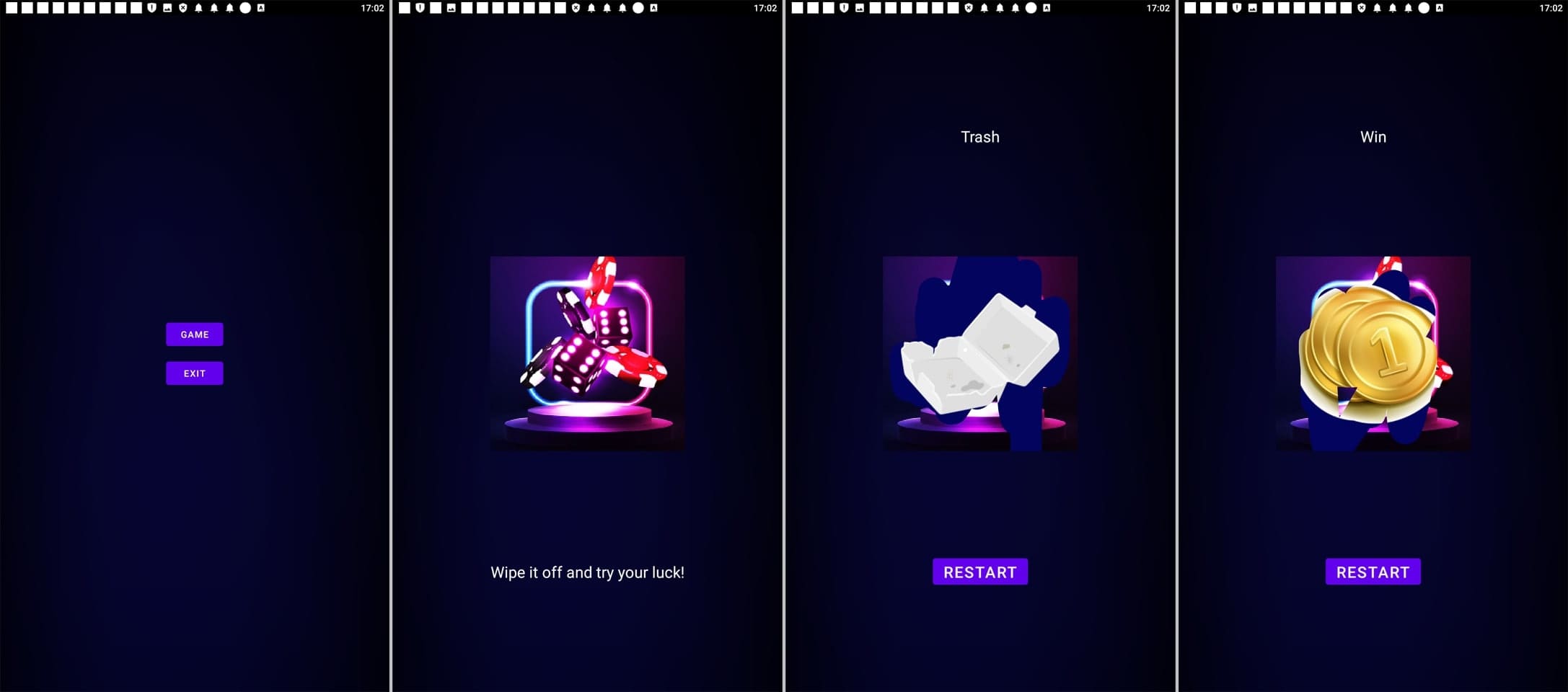
Under certain conditions, instead of the expected functionality, they could display websites of online casinos—for example, if their installation was the consequence of a user clicking a specific link from an ad.
Below are examples of such behavior: in some cases, users see a game, while in others, they see websites of online casinos.
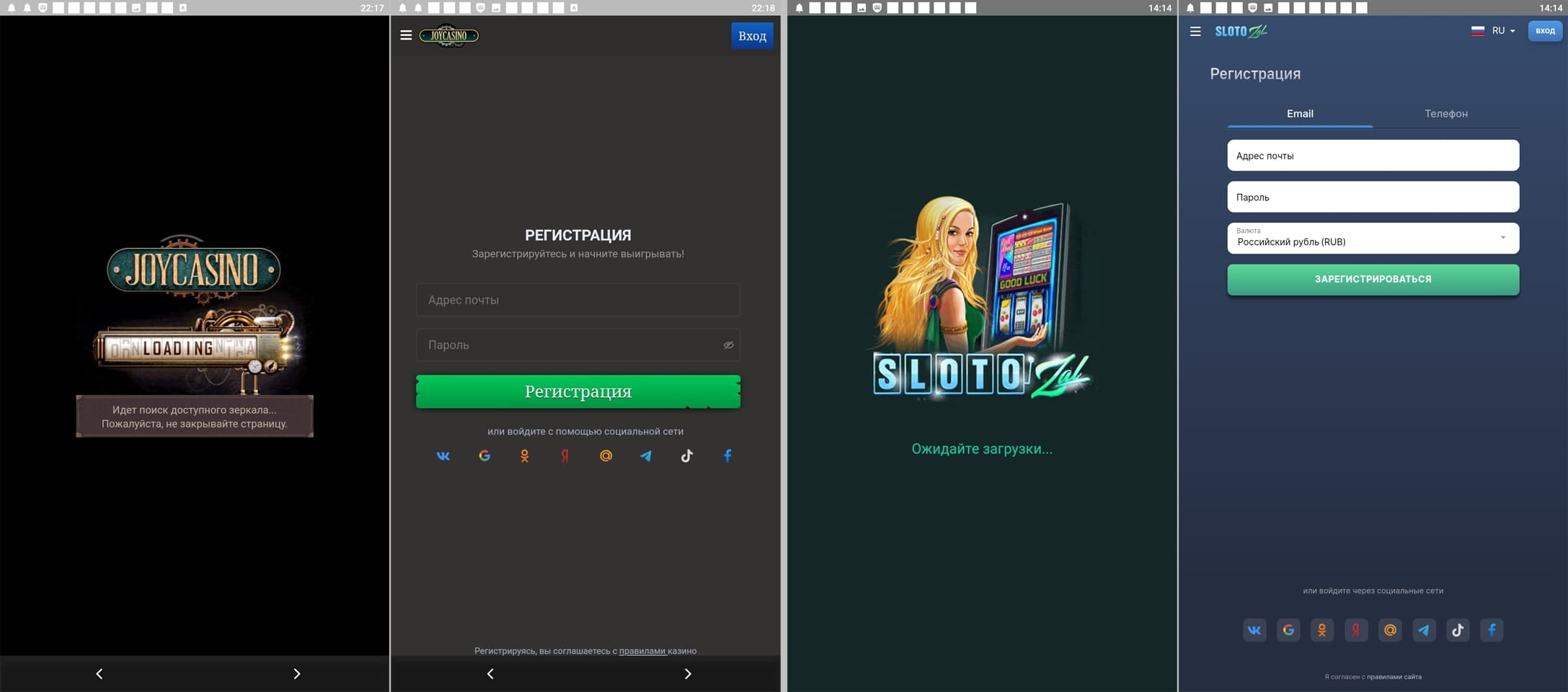
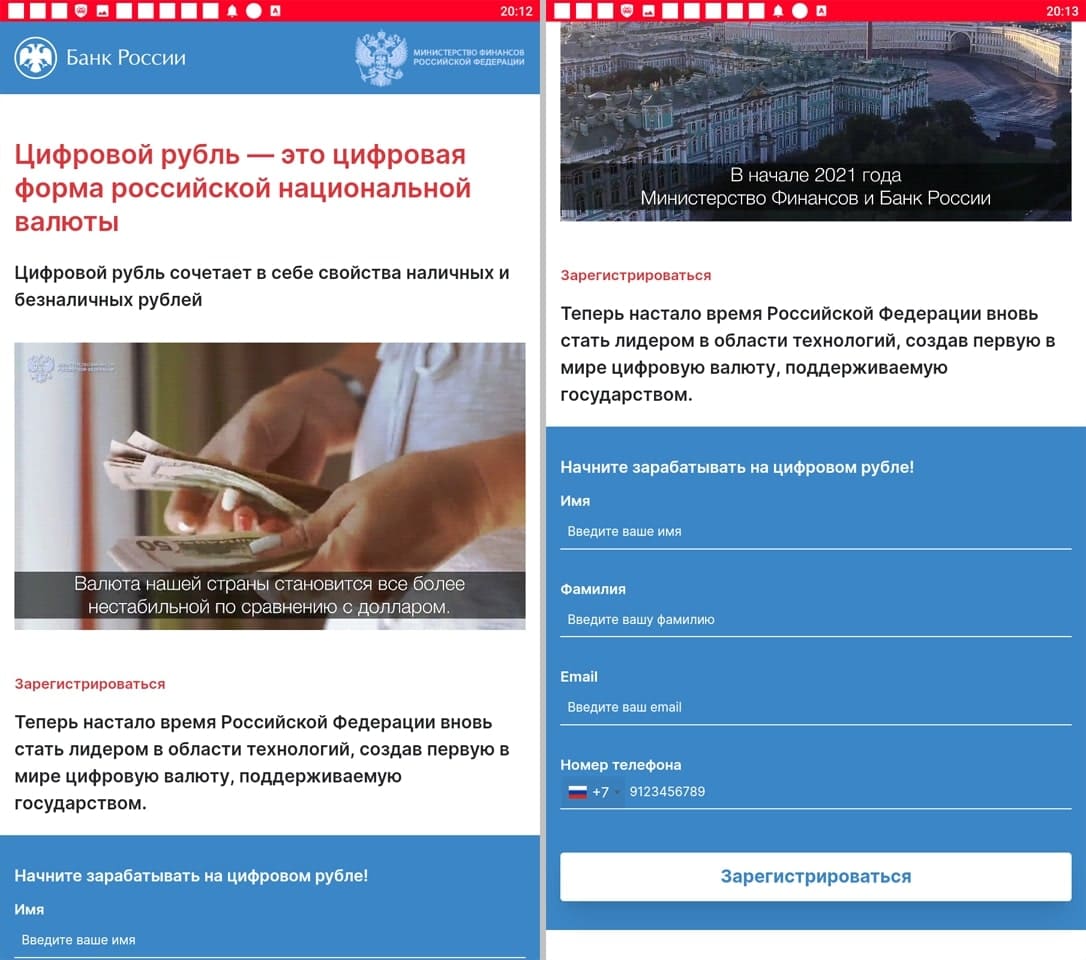
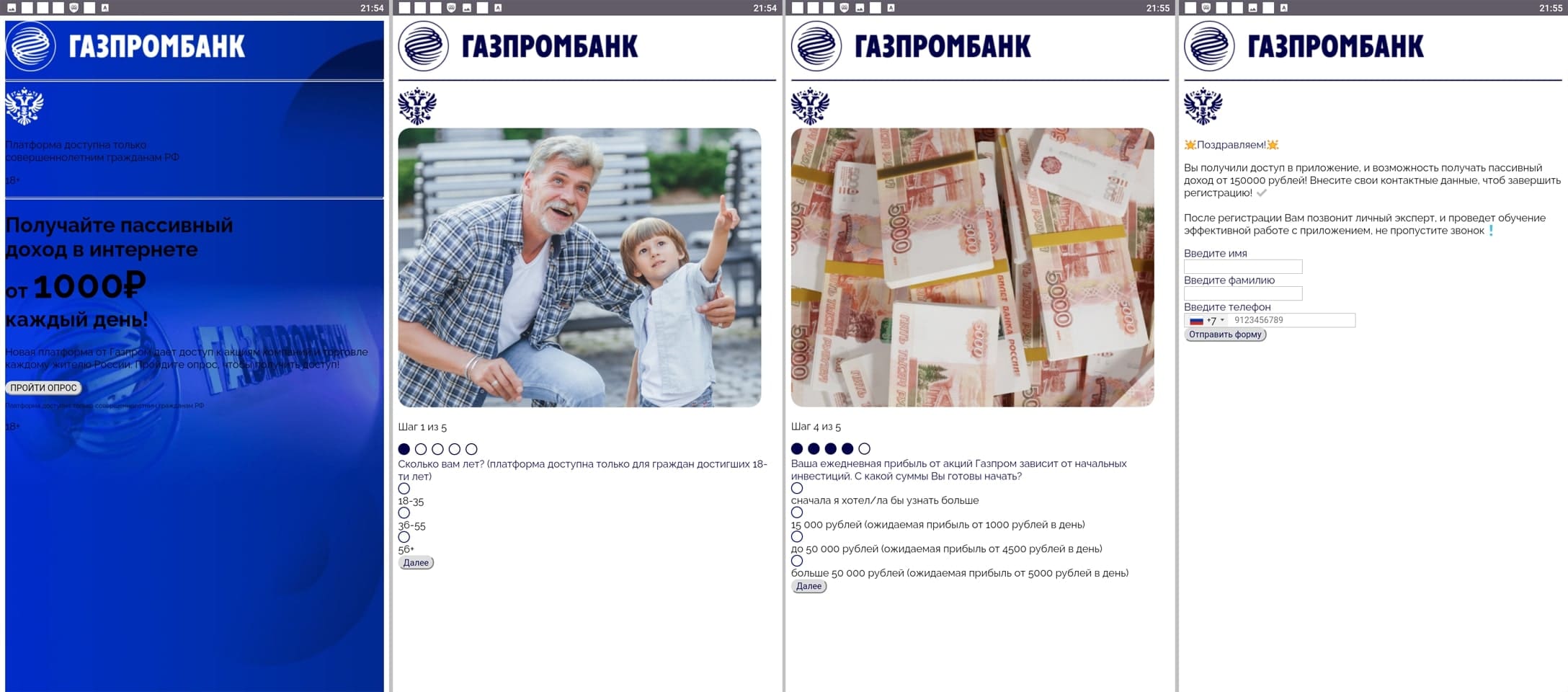
Other fake apps were distributed as financial software and self-development tools. With their help, users allegedly could keep track of their expenses and perform home bookkeeping, take part in different polls and quizzes, study, receive training and improve their financial literacy, begin investing, or receive free shares. In reality though, the main goal of these apps was to load fraudulent sites.
Below are examples of the websites they could load. Potential victims are shown misleading information, or they are offered the chance to take part in a preliminary poll. Next, they are invited to register an account by providing their personal information. At the end they are required to wait for a phone call from a so-called “specialist” or for the arrival of some “advantageous offer”.
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web anti-virus products for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products