Doctor Web’s February 2022 review of virus activity on mobile devices
March 31, 2022
All sorts of fake apps from the Android.FakeApp family that cybercriminals use in various scam schemes were among the threads discovered on Google Play. Our specialists also uncovered several multifunctional trojans from the Android.Triada family, and another malicious app from the Android.Subscription family. The latter subscribes victims to paid mobile services.
PRINCIPAL TRENDS IN JANUARY
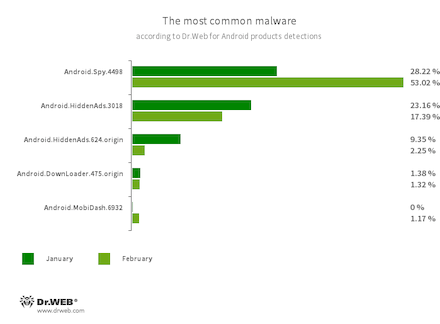
- The Android.Spy.4498 trojan remains the leader among the threats detected on protected Android devices
- Adware trojans is still an active threat
- The appearance of new threats on Google Play
According to statistics collected by Dr.Web for Android
- Android.Spy.4498
- A trojan that steals the contents of other apps’ notifications. It can also download apps and offer users to install them, and can also display various dialog boxes.
- Android.HiddenAds.3018
- Android.HiddenAds.624.origin
- Trojans designed to display obnoxious ads. Trojans of this family are often distributed as popular and harmless applications. In some cases, other malware can install them in the system directory. When these trojans infect Android devices, they typically conceal their presence from the user. For example, they “hide” their icons from the home screen menu.
- Android.MobiDash.6932
- A trojan that displays obnoxious ads. It is a special software module that the developers incorporate into applications.
- Android.DownLoader.475.origin
- Trojan that downloads other malware and unwanted software. It can be hidden inside seemingly harmless apps found on Google Play or malicious websites.
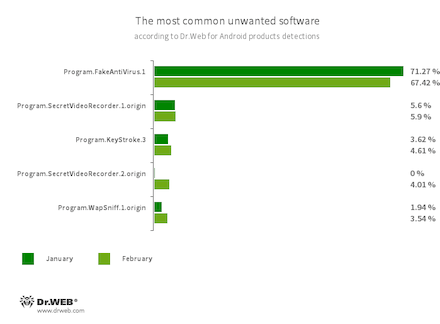
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of non-existing threats, mislead them, and demand they purchase the software’s full version.
- Program.SecretVideoRecorder.1.origin
- Program.SecretVideoRecorder.2.origin
- The detection name for various modifications of an application designed to record videos and take photos in the background using Android devices’ built-in cameras. It can operate covertly, allowing disabling notifications about ongoing recordings. It also allows replacing the app’s icon and name with fake ones. This functionality makes this software potentially dangerous.
- Program.KeyStroke.3
- An Android application capable of intercepting keystrokes. Some modifications of this software can also track incoming SMS, control call history, and record phone calls.
- Program.WapSniff.1.origin
- An Android program designed to intercept WhatsApp messages.
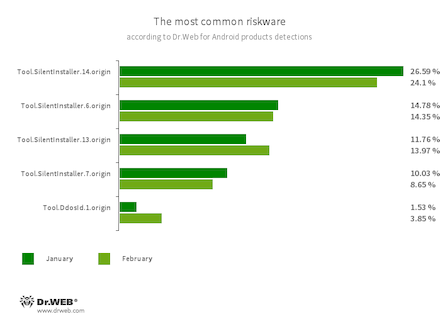
- Tool.SilentInstaller.14.origin
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.13.origin
- Tool.SilentInstaller.7.origin
- Riskware platforms that allow applications to launch APK files without installation. They create a virtual runtime environment that does not affect the main operating system.
- Tool.DdosId.1.origin
- An Android app designed for stability and stress-testing of networks, web servers, and websites. It is not malicious itself, but can be used to perform DoS (Denial-of-Service) attacks. That is why Dr.Web detects it as a potentially dangerous tool.
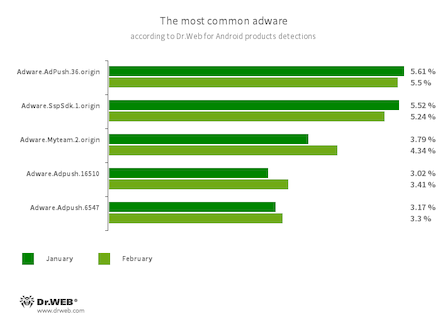
Program modules incorporated into Android applications. These are designed to display obnoxious ads on Android devices. Depending on their family and modifications, they can display full-screen ads and block other apps’ windows, show various notifications, create shortcuts, and load websites.
- Adware.AdPush.36.origin
- Adware.SspSdk.1.origin
- Adware.Myteam.2.origin
- Adware.Adpush.16510
- Adware.Adpush.6547
Threats on Google Play
Throughout February, Doctor Web’s specialists discovered more fake apps on Google Play. Malicious actors use these in various fraudulent schemes. Some of them, like the Android.FakeApp.895 (“Выплаты Gaz”), Android.FakeApp.896 (“Gasprom Инвестиции”), and Android.FakeApp.897 (“Gaz Investr”), spread under the guise of software that could be used to invest into oil and natural gas projects. Another trojan, Android.FakeApp.781, hid in the app called “Вернуть налог на карту”. This app could allegedly help users to receive monetary compensations, like tax refunds. All these trojans loaded fraudulent websites through which scammers tried to steal personal information and money from potential victims.
In addition, Android.Triada.5186, Android.Triada.5241, and Android.Triada.5242 multifunctional trojans have been found in apps and games like “Flying Knife Master-Throw Hit”, “Powerful Multi Space-2Accounts”, “Space Flight Battle”, and “Idle Soldier-Battle Royale.io”.
Our malware analysts have also uncovered an Android.Subscription.7 trojan app. It loaded affiliate programs’ websites to subscribe victims to paid mobile services. It was spread as an image editing software called “Funky Photo”.
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products