Doctor Web’s July 2021 review of virus activity on mobile devices
August 11, 2021
Our specialists also discovered a new family of Android banking trojans dubbed Android.BankBot.Coper.
Adware trojans and malware capable of executing arbitrary code and downloading other software were among the most common threats detected on protected Android devices.
PRINCIPAL TRENDS IN JULY
- The discovery of a new family of Android banking trojans
- Several threats spread on Google Play were unveiled
- Adware trojans and trojans designed to execute arbitrary code remain among the most common threats on Android devices
Mobile threat of the month
Last month, Doctor Web’s malware analysts discovered a new family of Android banking trojans dubbed Android.BankBot.Coper. Initially, these malicious applications attacked Colombian users. Later, however, our specialists uncovered modifications targeting European Android users.
These banking trojans have a modular architecture and a number of protective mechanisms allowing them to operate more successfully. Upon receiving the malware authors’ commands, the trojans are able to intercept and send SMS, control push notifications, display phishing windows, and even hijack information entered on the keyboard.
More information on this malware family can be found in this news release.
According to statistics collected by Dr.Web for Android
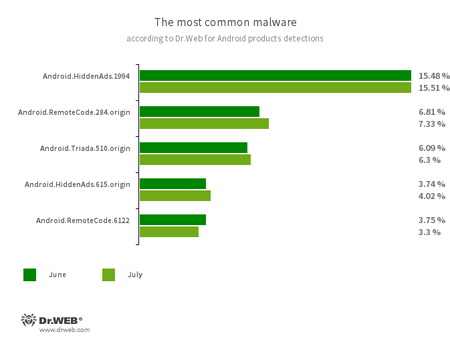
- Android.HiddenAds.1994
- Android.HiddenAds.615.origin
- Trojans designed to display obnoxious ads. They are distributed as harmless applications and, in some cases, are installed in the system directory by other malware.
- Android.RemoteCode.284.origin
- Android.RemoteCode.6122
- Malicious applications that download and execute arbitrary code. Depending on their modification, they can load various websites, open web links, click on advertising banners, subscribe users to premium services, and perform other actions.
- Android.Triada.510.origin
- A multifunctional trojan performing various malicious actions. This malware belongs to the trojan family that infects other app processes. Some modifications of this family were found in the firmware of Android devices, which attackers implanted during manufacturing. Some of them can also exploit various vulnerabilities to gain access to protected system files and folders.
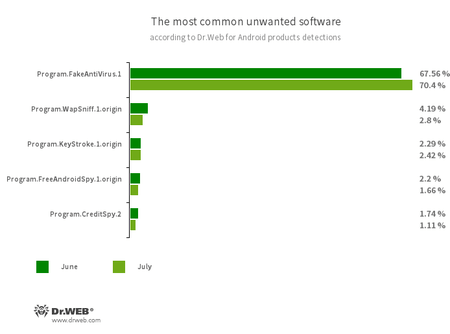
- Program.FakeAntiVirus.1
- The detection name for adware programs that imitate anti-virus software. These apps inform users of non-existing threats, mislead them, and demand they purchase the full version of the software.
- Program.WapSniff.1.origin
- An Android program designed to intercept messages from WhatsApp.
- Program.KeyStroke.1.origin
- An Android application capable of intercepting keystrokes. Some modifications of this software can also track incoming SMS, control calls history, and record phone calls.
- Program.FreeAndroidSpy.1.origin
- An application that spies on Android users and can be used for cyber espionage. It controls the location of the device, gains access to a phone book and user contact list, and can also copy multimedia files, such as photos and videos.
- Program.CreditSpy.2
- The detection name for programs designed to assign credit ratings to users based on their personal data. These applications upload SMS, contact information from phonebooks, call history, and other information to the remote server.
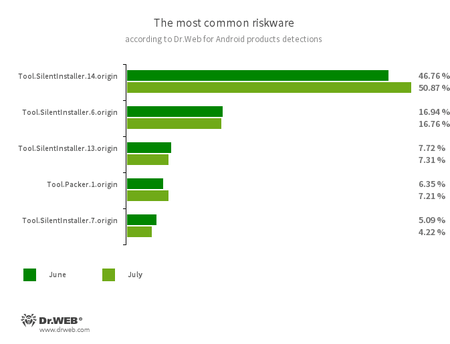
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.7.origin
- Tool.SilentInstaller.13.origin
- Tool.SilentInstaller.14.origin
- Riskware platforms that allow applications to launch APK files without installation. They create a virtual runtime environment that does not affect the main operating system.
- Tool.Packer.1.origin
- A packer tool designed to protect Android applications from their unauthorized modification and reverse engineering. This tool is not malicious by itself, but it can be used to protect both harmless and malicious software.
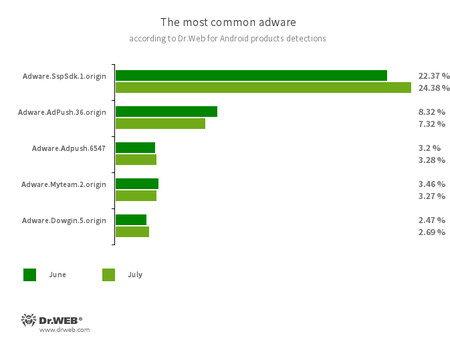
Program modules incorporated into Android applications and designed to display obnoxious ads on Android devices. Depending on their family and modifications, they can display full screen ads and block other apps’ windows, show various notifications, create shortcuts, and load websites.
- Adware.SspSdk.1.origin
- Adware.AdPush.36.origin
- Adware.Adpush.6547
- Adware.Myteam.2.origin
- Adware.Dowgin.5.origin
Threats on Google Play
In July, Doctor Web’s malware analysts uncovered other threats on Google Play. New trojans from the Android.Joker family that were added to Dr.Web virus database as Android.Joker.803, Android.Joker.837, and Android.Joker.846 were among them. They were hidden in seemingly harmless apps such as Background Changer image editor, Sweet Emoji SMS messenger, and Flashlight LED Pro flashlight software. The trojans did work as users expected, but also covertly subscribed victims to premium mobile services and were able to execute arbitrary code.
Additionally, a new modification of the Android.FakeApp.299 fraudulent app was found. It was spread among Russian-speaking users as a software helping them receive financial support such as allowances and social compensation from the government. The real functionality, however, was to load fraudulent websites that scammers used to steal confidential information and money from Android users.
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products