Doctor Web’s May 2021 review of virus activity on mobile devices
June 22, 2021
According to detection statistics collected by Dr.Web anti-virus products for Android, in May, adware trojans and malware capable of downloading other applications and executing arbitrary code were among the most common threats found on the protected devices.
Over the course of the month, Doctor Web’s specialists uncovered many new threats on Google Play. Trojans subscribing users to premium mobile services and malicious apps loading fraudulent sites were among them.
PRINCIPAL TRENDS IN MAY
- Adware trojans and malware capable of downloading and executing arbitrary code remain among most common threats for Android users
- The discovery of new trojans on Google Play
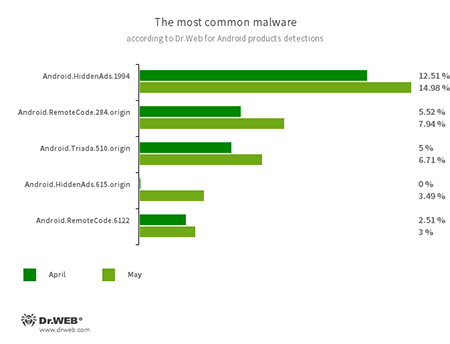
According to statistics collected by Dr.Web for Android
- Android.HiddenAds.1994
- Android.HiddenAds.615.origin
- Trojans designed to display obnoxious ads. They are distributed as harmless applications and, in some cases, are installed into the system directory by other malware.
- Android.RemoteCode.284.origin
- Android.RemoteCode.6122
- Malicious applications that download and execute arbitrary code. Depending on their modification, they can load various websites, open web links, click on advertising banners, subscribe users to premium services, and perform other actions.
- Android.Triada.510.origin
- A multifunctional trojan performing various malicious actions. This malware belongs to the trojan family that infects other app processes. Some modifications of this family were found in the firmware of Android devices, which attackers implanted during manufacturing. Some of them can also exploit various vulnerabilities to gain access to protected system files and folders.
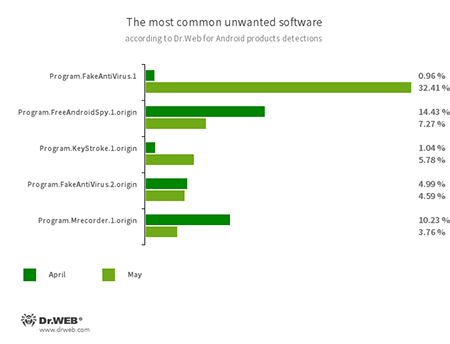
- Program.FakeAntiVirus.1
- Program.FakeAntiVirus.2.origin
- The detection name for adware programs that imitate anti-virus software. These apps inform users of non-existing threats, mislead them and demand they purchase the full version of the software.
- Program.FreeAndroidSpy.1.origin
- Program.Mrecorder.1.origin
- Software that monitors Android user activity and may serve as a tool for cyber espionage. These apps can track device locations, collect information from SMS and social media messages, copy documents, photo and video, spy on phone calls, etc.
- Program.KeyStroke.1.origin
- An application capable of intercepting keystrokes on Android devices. It also allows tracking incoming SMS, accessing calls history and recording phone calls.
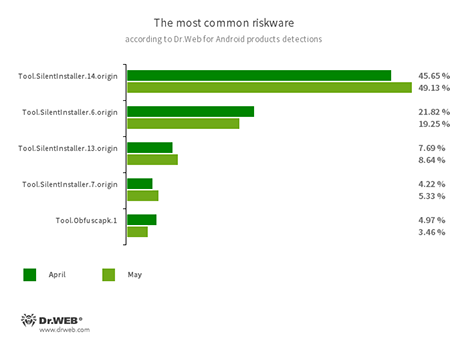
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.7.origin
- Tool.SilentInstaller.13.origin
- Tool.SilentInstaller.14.origin
- Riskware platforms that allow applications to launch APK files without installation. They create a virtual runtime environment that does not affect the main operating system.
- Tool.Obfuscapk.1
- The detection name for applications protected by the Obfuscapk obfuscation tool. This tool is used to automatically modify and scramble Android apps’ source code to make reverse engineering more difficult. Cybercriminals use the tool to protect malicious applications from being detected by anti-virus programs.
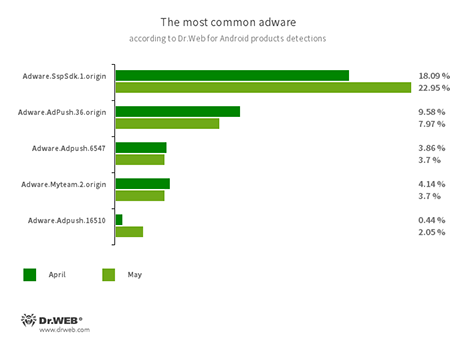
Program modules incorporated into Android applications and designed to display obnoxious ads on Android devices. Depending on their family and modifications, they can display full screen ads and block other apps’ windows, show various notifications, create shortcuts and load websites.
- Adware.SspSdk.1.origin
- Adware.Adpush.36.origin
- Adware.Adpush.6547
- Adware.Adpush.16510
- Adware.Myteam.2.origin
Threats on Google Play
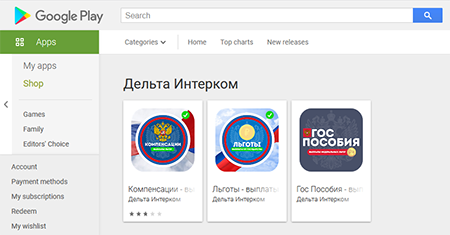
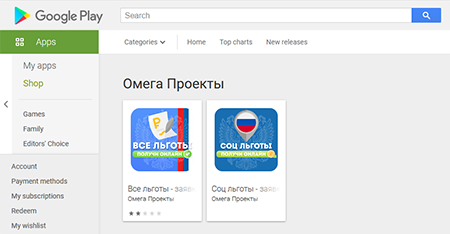
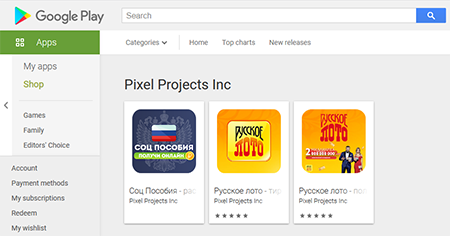
In May, Doctor Web’s specialists unveiled many new malicious apps on Google Play. Various trojans from the Android.FakeApp family were among them. The majority of these trojans were spread under the guise of software that allegedly allowed users to find information about payments, allowances and compensations from the government and apply for them. Others were distributed as official apps of the «Русское лото» (Russian Lotto) lottery, in which potential victims were offered free lottery tickets and invited to check other tickets for winnings.
None of these fake apps provided the advertised functionality that Android users were expecting to have. The trojans only loaded fraudulent sites that malicious actors used to steal money and personal information from their victims. At the same time, some of these malicious apps also displayed intrusive and annoying notifications, which also led to the scammers’ websites. These trojans were added to the Dr.Web virus base as Android.FakeApp.262, Android.FakeApp.263, Android.FakeApp.264, Android.FakeApp.265, Android.FakeApp.266, Android.FakeApp.269, Android.FakeApp.270, Android.FakeApp.271, Android.FakeApp.272, and Android.FakeApp.273.
Examples of the trojans' appearance:
Examples of notifications these trojans can display:
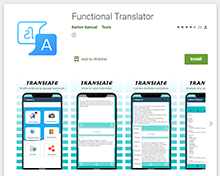
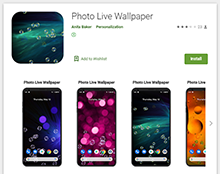
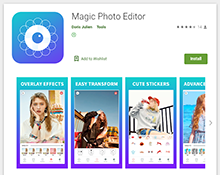
Our malware analysts also discovered new trojans from the Android.Joker family, capable of executing arbitrary code and subscribing victims to paid mobile services. These malicious programs were spread as SMS messaging apps, a translator, live wallpaper and photo editing software. They were added to the Dr.Web virus database as Android.Joker.722, Android.Joker.723, Android.Joker.729, Android.Joker.730, Android.Joker.739, Android.Joker.742, and Android.Joker.744.
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products