Doctor Web’s February 2021 review of virus activity on mobile devices
March 17, 2021
In February, malicious and unwanted programs displaying ads and trojans executing arbitrary code and downloading various apps without users’ awareness were detected most often by Dr.Web anti-virus products for Android.
Throughout the last month, Doctor Web’s malware analysts uncovered more threats on Google Play. Numerous fraudulent applications from the Android.FakeApp family, multifunctional Android.Joker trojans, Android.HiddenAds adware trojans and other dangerous programs were among them.
PRINCIPAL TRENDS IN FEBRUARY
- New malware discovered on Google Play
- Malicious Android apps are actively used in various scam schemes
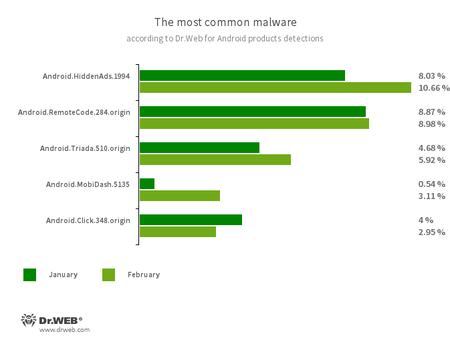
According to statistics collected by Dr.Web for Android
- Android.HiddenAds.1994
- A trojan designed to display obnoxious ads, distributed as popular applications. In some cases, it can be installed in the system directory by other malware.
- Android.RemoteCode.284.origin
- A malicious application that downloads and executes arbitrary code. Depending on its modification, it can load various websites, open web links, click on advertising banners, subscribe users to premium services and perform other actions.
- Android.Triada.510.origin
- A multifunctional trojan performing various malicious actions. This malware belongs to the trojan family that infects other app processes. Some modifications of this family were found in the firmware of Android devices, which attackers implanted during manufacturing. Some of them can also exploit various vulnerabilities to gain access to protected system files and folders.
- Android.Click.348.origin
- A malicious application that loads websites, clicks on banner ads, and follows links. It can be distributed as harmless programs without arousing suspicion among users.
- Android.MobiDash.5135
- A trojan that displays obnoxious ads. It represents a special software module that is incorporated into the applications by the developers.
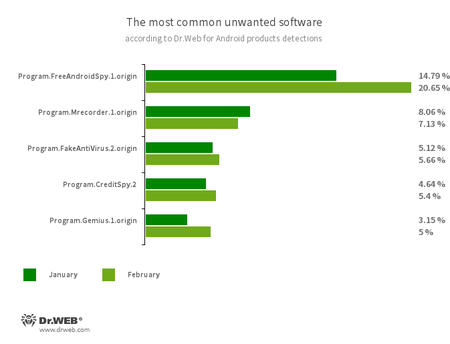
- Program.FreeAndroidSpy.1.origin
- Program.Mrecorder.1.origin
- Software that monitors Android user activity and may serve as a tool for cyber espionage. These apps can track device locations, collect information from SMS and social media messages, copy documents, photo and video, spy on phone calls, etc.
- Program.FakeAntiVirus.2.origin
- The detection name for adware programs that imitate anti-virus software. These apps inform users of non-existing threats, mislead them and demand they purchase the full version of the software.
- Program.CreditSpy.2
- The detection name for programs designed to assign credit ratings to users based on their personal data. These applications upload SMS, contact information from phonebooks, call history and other information to the remote server.
- Program.Gemius.1.origin
- An application that collects information about Android devices and how their owners are using them. With technical data, it also collects confidential information, such as device location, browser bookmarks, web history, and typed URLs.
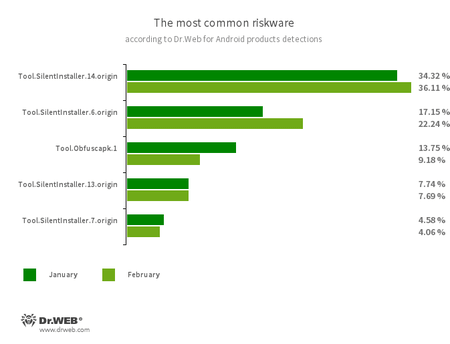
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.7.origin
- Tool.SilentInstaller.13.origin
- Tool.SilentInstaller.14.origin
- Riskware platforms that allow applications to launch APK files without installation. They create a virtual runtime environment that does not affect the main operating system.
- Tool.Obfuscapk.1
- The detection name for applications protected by the Obfuscapk obfuscation tool. This tool is used to automatically modify and scramble Android apps’ source code to make reverse engineering more difficult. Cybercriminals use the tool to protect malicious applications from being detected by anti-virus programs.
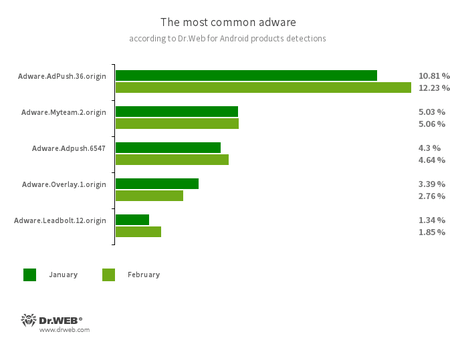
Program modules incorporated into Android applications and designed to display obnoxious ads on Android devices. Depending on their family and modifications, they can display full screen ads and block other apps’ windows, show various notifications, create shortcuts and load websites.
- Adware.Adpush.36.origin
- Adware.Adpush.6547
- Adware.Myteam.2.origin
- Adware.Overlay.1.origin
- Adware.LeadBolt.12.origin
Threats on Google Play
Throughout January, Doctor Web’s specialists observed significant activity among the malicious applications from the Android.FakeApp family. A large number of the apps were used by cyberattackers in various fraudulent schemes. One of the trojan groups was spread as software allegedly designed to provide access to discounts, promotional and bonus cards, as well as to gifts from famous stores and companies. To make it look more appealing, the malware authors used symbols and names of corresponding brands—consumer electronics manufacturers, gas stations and retailers.
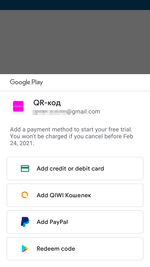
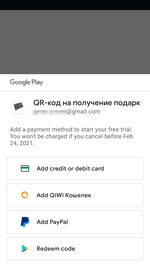
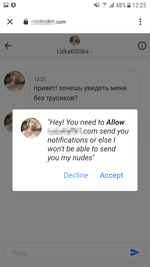
Upon their launch, these apps invited potential victims to apply for a paid subscription (starting from 449 to 1499 rubles per week) allegedly to access the complete functionality of the software and to receive promised bonuses. However, they only received useless barcodes and QR codes—the same for all trojans—with the promise of receiving notifications with new codes in the future. At the same time, only a few modifications of these programs had the functionality to work with the notifications, which alone questioned their developer’s integrity.
If users agreed to make an in-app purchase, they were given a 3-day free trial so they could confirm the subscription or cancel it. The logic of the fraudulent scheme was that Android device owners will either forget about trial period or that they even installed these apps in the first place, or due to lack of experience, they would not realize they applied for a premium service with regular charges.
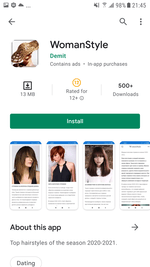
Various modifications of these trojans were added to the Dr.Web virus database as Android.FakeApp.239, Android.FakeApp.240, Android.FakeApp.246, and Android.FakeApp.247. Examples of how some of them operate are shown on the images below:
Messages and code examples they displayed after a user successfully subscribed to the premium service:
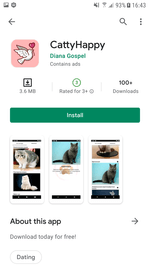
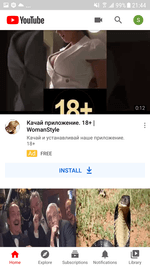
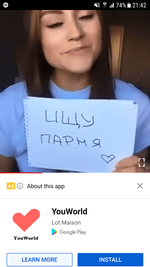
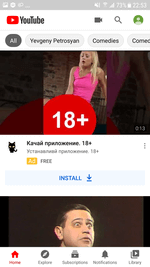
The second group of fake programs from the Android.FakeApp family included software spread by scammers as broadly themed, harmless applications including reference software and guides about fashion, animals, nature, and various horoscopes. Their real functionality didn’t match what was indicated. They only loaded different dating and even scam websites. These apps were actively promoted through the YouTube ads network when advertising video clips and banners aggressively used adults-only content with dating and meetings topics as well. Overall, Doctor Web’s specialists uncovered more than 20 of these fake applications.
Examples of these trojans distributed throughout Google Play and the ads leading to them are shown below:
The examples of websites these apps loaded:
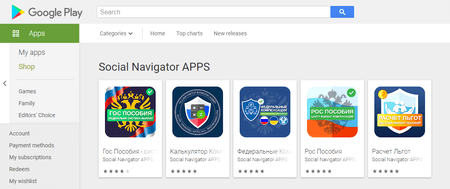
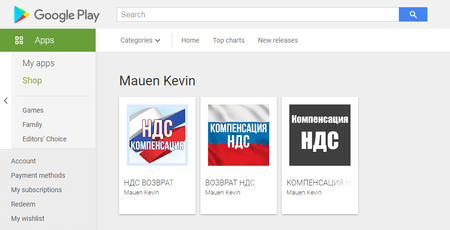
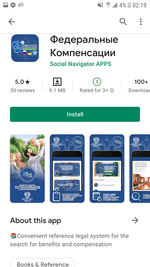
The third group of the Android.FakeApp malicious apps included other variations of fraudulent trojans, which were spread under the guise of software with information about various financial compensations, social benefits and payouts. They were none other than the modifications of the well-known Android.FakeApp.219 and Android.FakeApp.227 malware.
Similar to some of the other fake apps within the same family, they were also advertized through YouTube:
Upon their launch, the trojans loaded fraudulent sites where potential victims could allegedly find information about payouts available to them. There, users were misled and asked to provide their personal data and either pay a money “transfer” commission or a “state duty”. In reality, there were not any payouts for users. They only released their personal details and transferred their money to the scammers.
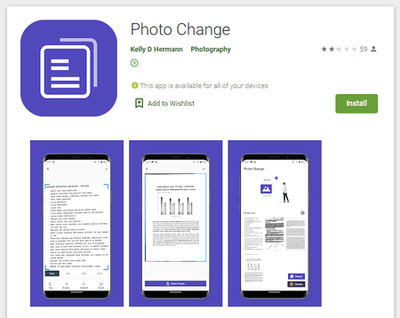
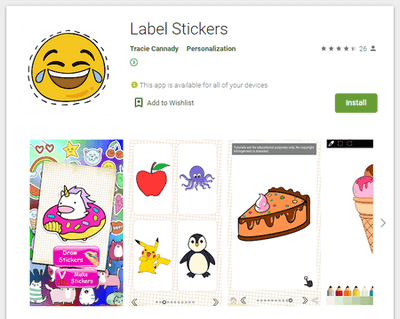
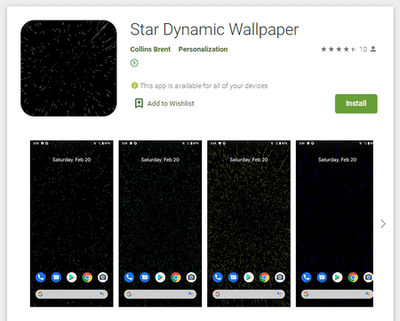
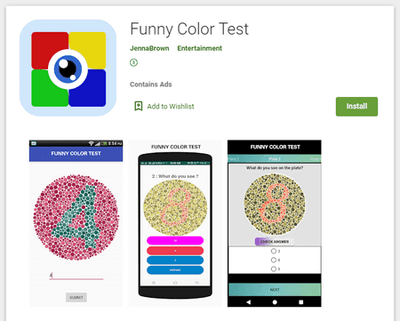
Doctor Web’s malware analysts also uncovered several new multifunctional trojans from the Android.Joker family. As other malware from this family, they were spread as harmless apps, including image editing software, a barcode scanner, software for creating PDF documents, a collection of stickers for messaging apps, animated wallpapers and others. These trojans were dubbed Android.Joker.580, Android.Joker.585, Android.Joker.586, Android.Joker.592, Android.Joker.595, Android.Joker.598, and Android.Joker.604.
Their main functionality was loading and executing an arbitrary, as well as automatically subscribing users to premium mobile services.
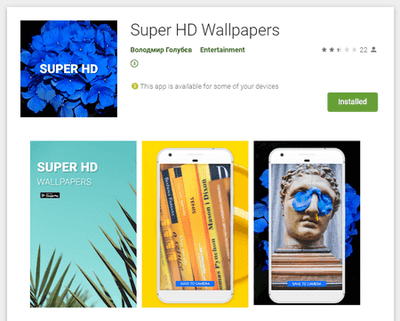
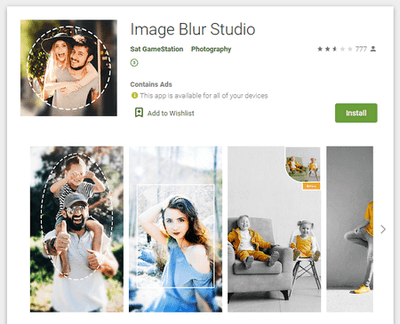
Moreover, other adware trojans from the Android.HiddenAds malware family were also discovered on Google Play. They were dubbed Android.HiddenAds.610.origin and Android.HiddenAds.2357. The first one was spread as an image collection app while the second one was spread as picture editing software.
Upon launch, the trojans concealed their icons from the list of installed apps on the main screen menu and began displaying ads. With that, Android.HiddenAds.610.origin received commands through the Firebase cloud service and was able to display notifications with ads and load various sites. They could be websites with ads, as well as dubious and fraudulent sites.
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products