Doctor Web’s December 2020 virus activity review
December 31, 2020
Our December analysis of Dr.Web’s statistics revealed a 11.49% decrease in the total number of threats compared to the previous month. The number of unique threats also dropped by 24.51%. Adware and malware browser extensions still made up the majority of detected threats. Email traffic was dominated by various malware that includes the Trojan.SpyBot.699 banking trojan, an obfuscated stealer written in VB.NET and malicious programs exploiting vulnerabilities in Microsoft Office utilities.
The number of requests to decrypt files affected by trojan encoders decreased by 31.54% compared to November. Trojan.Encoder.26996 was the most active, accounting for 37.14% of all incidents.
Principal trends in December
- A decline in malware spreading activity
- Adware remain among the most active threats
- A decline in the number of unique threats in email traffic
According to Doctor Web’s statistics service
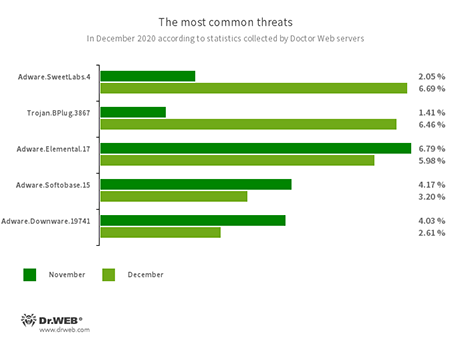
The most common threats in December:
- Adware.SweetLabs.4
- An alternative app store and add-on for Windows GUI from the creators of Adware.Opencandy.
- Trojan.BPlug.3867
- A malicious browser extension designed to perform web injections into viewed webpages and block third-party advertisements.
- Adware.Elemental.17
- Adware that spreads through file sharing services as a result of link spoofing. Instead of normal files, victims receive applications that display advertisements and install unwanted software.
- Adware.Softobase.15
- Installation adware that spreads outdated software and changes the browser settings.
- Adware.Downware.19741
- Adware that often serves as an intermediary installer of pirate software.
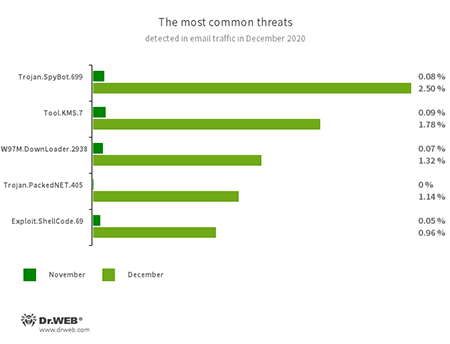
Statistics for malware discovered in email traffic
- Trojan.SpyBot.699
- A multi-module banking trojan that allows cybercriminals to download and launch various applications on an infected device and run arbitrary code.
- Tool.KMS.7
- Hacking tools used to activate illegal copies of Microsoft software.
- W97M.DownLoader.2938
- A family of downloader trojans that exploits vulnerabilities in Microsoft Office documents and can download other malicious programs to a compromised computer.
- Trojan.PackedNET.405
- An obfuscated version of a stealer written in VB.NET. It can be used as a keylogger and is designed to steal confidential data.
- Exploit.ShellCode.69
- A malicious Microsoft Office Word document that exploits the CVE-2017-11882 vulnerability.
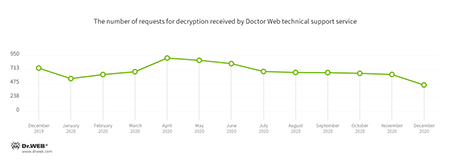
Encryption ransomware
In December, Doctor Web’s virus laboratory registered 28.41% fewer requests to decode files encoded by trojan ransomware than in November.
- Trojan.Encoder.26996 — 37.14%
- Trojan.Encoder.567 — 20.00%
- Trojan.Encoder.29750 — 3.17%
- Trojan.Encoder.11549 — 1.27%
- Trojan.Encoder.30356 — 1.27%
Dr.Web Security Space for Windows protects against encryption ransomware
Dangerous websites
In December 2020, Doctor Web added 105,840 URLs to the Dr. Web database of non-recommended websites.
| November 2020 | December 2020 | Dynamics |
|---|---|---|
| + 154,606 | + 105,840 | - 31.54% |
Malicious and unwanted programs for mobile devices
In December, Dr.Web’s statistics for Android devices confirmed an almost 25.34% decrease in the total number of threats on protected devices compared with November. Users most often encountered adware trojans, as well as malicious applications that download other software and execute arbitrary code.
Another threat, Android.Joker.477, was detected in the Google Play catalog. It was hidden within an application with an image collection. It was capable of running arbitrary code and subscribing Android users to paid services.
Also in December, various banking trojans attacked users of Android devices.
The following December events related to mobile malware are the most noteworthy:
- A decline in malware activity on protected devices
- The detection of new malicious program on Google Play
Find out more about malicious and unwanted programs for mobile devices in our special overview.