Doctor Web’s September 2020 review of virus activity for mobile devices
October 22, 2020
According to the detection statistics of Dr.Web anti-virus products for Android, September has seen 3.75% more threats on protected devices than in August. Compared to the previous month, the number of malware increased by 5.58% and riskware by 4.98%. With that, the number of adware and unwanted software decreased by 6.22% and 8.83% respectively.
During September, Doctor Web’s malware analysts found several new malicious apps on Google Play. The Android.Joker trojan family members capable of executing arbitrary code and subscribing victims to premium services were among them. Moreover, malefactors have spread the Android.Click.978 clicker trojan that displayed ads, as well as the multifunctional Android.Triada.545.origin trojan used in phishing and other types of attacks.
PRINCIPAL TRENDS IN SEPTEMBER
- An increased number of threats detected on Android mobile devices
- The spread of new threats through Google Play
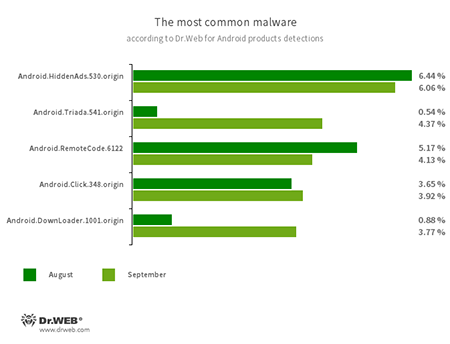
According to statistics collected by Dr.Web for Android
- Android.HiddenAds.530.origin
- A trojan designed to display obnoxious ads and distributed as popular applications. In some cases, it can be installed in the system directory by other malware.
- Android.Triada.541.origin
- A multifunctional trojan that performs various malicious actions. This malware belongs to the family of trojans that infect other apps’ processes. Some of their modifications could be found in the firmware of Android devices, implanted by attackers during the manufacturing process.
- Android.RemoteCode.6122
- Malicious application that download and execute arbitrary code. Depending on its modification, it can load various websites, open web links, click on advertisement banners, subscribe users to premium services and perform other actions.
- Android.Click.348.origin
- A trojan that automatically loads websites and clicks on links and advertisement banners. It can be spread as a harmless app so users will not consider it a threat.
- Android.DownLoader.1001.origin
- A trojan that downloads other malware and unwanted software. It can be hidden inside seemingly harmless apps found on Google Play or malicious websites.
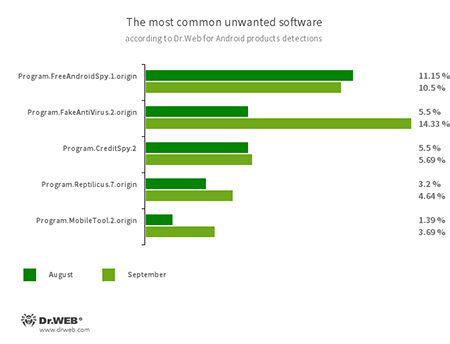
- Program.FreeAndroidSpy.1.origin
- Program.Reptilicus.7.origin
- Program.MobileTool.2.origin
- Software that monitors Android user activity and may serve as a tool for cyber espionage. These apps can track device locations, collect information from SMS and social media messages, copy documents, photo and video, spy on phone calls, etc.
- Program.FakeAntiVirus.2.origin
- Detection name for adware programs that imitate anti-virus software. These apps inform users of non-existing threats, mislead them and demand they purchase the full version of the software.
- Program.CreditSpy.2
- Detection name for programs designed to assign credit ratings to users based on their personal data. These applications upload SMS, contact information from phonebooks, call history and other information to the remote server.
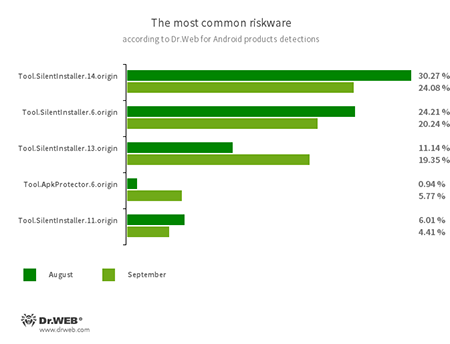
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.11.origin
- Tool.SilentInstaller.13.origin
- Tool.SilentInstaller.14.origin
- Riskware platforms that allow applications to launch APK files without installation. They create a virtual runtime environment that does not affect the main operating system.
- Tool.ApkProtector.6.origin
- Detection name for Android apps protected by the ApkProtector software packer. This packer is not malicious itself but cybercriminals can use it when creating malware and unwanted applications to make it more difficult for the anti-virus software to detect them.
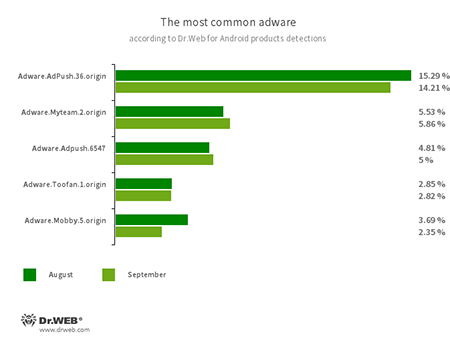
Program modules incorporated into Android applications and designed to display obnoxious ads on Android devices. Depending on their family and modifications, they can display full screen ads and block other apps’ windows, show various notifications, create shortcuts and load websites.
- Adware.Adpush.36.origin
- Adware.Adpush.6547
- Adware.Myteam.2.origin
- Adware.Toofan.1.origin
- Adware.Mobby.5.origin
Threats on Google Play
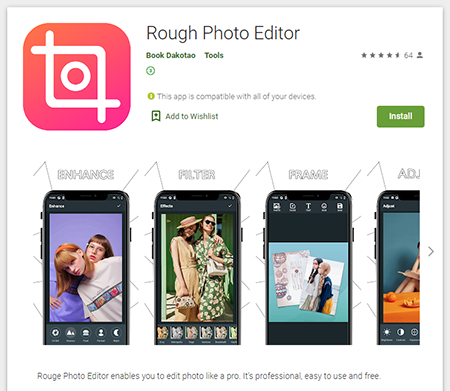
In September, several new modifications of the Android.Joker trojan family were found on Google Play. One of them, dubbed Android.Joker.341 was spread as picture editing software. Similar to other trojans of this family, it downloaded and executed arbitrary code and could subscribe users to paid services, collecting the confirmation codes from incoming notifications.
Upon launching, depending on the CPU architecture used on the infected device, the trojan loads one of the native libraries hidden inside its apk file into the memory. Dr.Web anti-virus detects them as Android.Joker.339 and Android.Joker.340.
In turn, the loaded library extracts the malicious Android.Joker.177.origin module from its body, which then downloads the Android.Joker.192.origin module from the remote server. Android.Joker.192.origin acquires access to the notification contents and downloads another module, Android.Joker.107.origin. This module contains the primary malicious functionality.
Later on, malware analysts discovered a similar trojan spread as an image collection app. It was added to the virus base as Android.Joker.344.
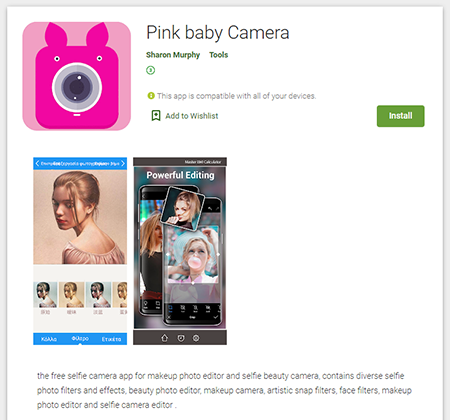
Another threat was the multifunctional Android.Triada.545.origin trojan from the dangerous Android.Triada malware family. It was hidden inside the camera application.
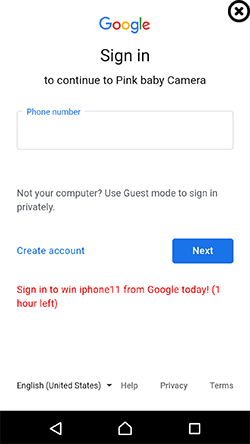
Part of the Android.Triada.545.origin functionality is phishing. Upon launching, the trojan displays a fake Google services authorization window. In this window, victims are required to enter their confidential information to sign into the account ― allegedly, to continue using the app. To make users even more confused, this window has a fake promotional text about the possibility to win a new phone after logging into the account. However, this is all just a trick and the provided information is sent to the cybercrooks.
On top of that, Android.Triada.545.origin is also able to download and execute arbitrary code, as well as intercept incoming notifications and steal the information, such as PIN codes.
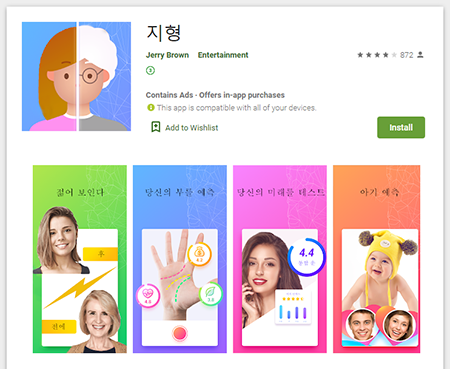
One more Android threat discovered on Google Play in September, was the Android.Click.978 clicker trojan spread as a fortune telling app. Upon launch, it hid its icon from the application list of the main screen menu and started to display ads. These ads were displayed even after the malicious software was closed. The trojan also loaded websites and automatically clicked the links and banners located on them.
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products