Doctor Web’s March 2020 overview of malware detected on mobile devices
April 13, 2020
In March, the number of threats discovered on Android devices increased by 21.24% compared to February. The amount of malware increased by 21.6%, unwanted apps – by 13.37%, riskware – by 32.65% and adware – by 27.64%.
Throughout the month, Doctor Web analysts discovered new threats on Google Play. The Android.Joker trojan family member showing obnoxious ads and subscribing users to premium services, as well as the dangerous multifunctional trojan Android.Circle.1 executing attackers’ commands were among them.
PRINCIPAL TRENDS IN FEBRUARY
- The growing number of the threats detected on Android devices
- The discovery of new threats on Google Play
Threat of the month
In March, Doctor Web reported on the discovery of the new dangerous trojan dubbed Android.Circle.1 spread through Google Play. It was downloaded more than 700,000 times. At the command of attackers, this malware would show advertisements and load various websites where it imitated users’ actions performing clicks on banners and links. The example of showed ads could be seen below:
Throughout the month, our specialists discovered several modifications of this trojan.
Features of Android.Circle.1:
- built in benign apps
- created using Multiple APKs mechanism, allowing developers to upload various copies of a single app on Google Play to support different device models and CPU architectures
- receives and executes BeanShell scripts
- part of its functionality is implemented through a separate native library
- some modifications of the trojan impersonate an important system component in order to stay under the radar
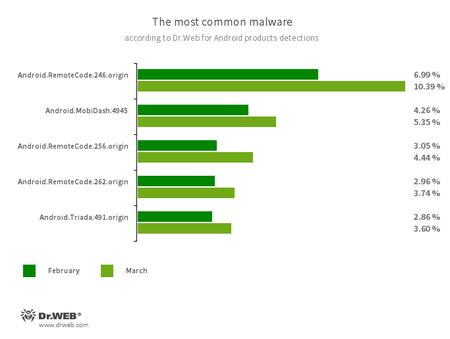
According to statistics collected by Dr.Web for Android
- Android.RemoteCode.246.origin
- Android.RemoteCode.256.origin
- Android.RemoteCode.262.origin
- Malicious applications that download and execute arbitrary code.
- Android.MobiDash.4945
- A trojan that displays obnoxious ads.
- Android.Triada.491.origin
- A trojan that executes criminal commands and helps them control infected mobile devices.
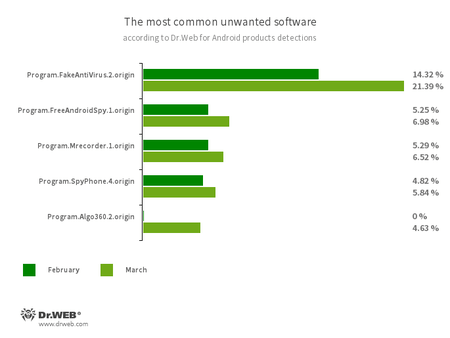
- Program.FakeAntiVirus.2.origin
- Detects adware that imitates anti-virus software.
- Program.FreeAndroidSpy.1.origin
- Program.Mrecorder.1.origin
- Program.MobileTool.2.origin
- Software that monitors Android user activity and may serve as a tool for cyber espionage.
- Program.Algo360.2.origin
- Detects a special software module that is used by financial organisations in their apps in order to provide users with loans. It represents a tool that collects users’ private information to build their credit profile. This module collects data about SMS messages, web browser bookmarks, device geolocation, calendar entries and other personal information.
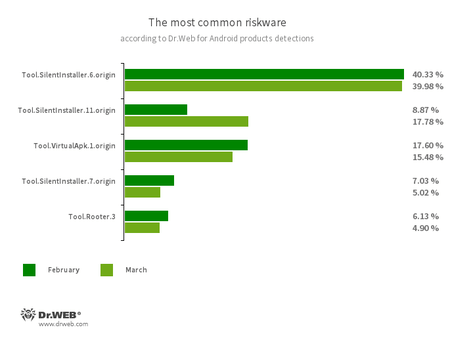
- Tool.SilentInstaller.6.origin
- Tool.SilentInstaller.7.origin
- Tool.SilentInstaller.11.origin
- Tool.VirtualApk.1.origin
- Riskware platforms that allow applications to launch APK files without installation.
- Tool.Rooter.3
- A utility designed to obtain root privileges on Android devices. It may be used by cybercriminals and malware.
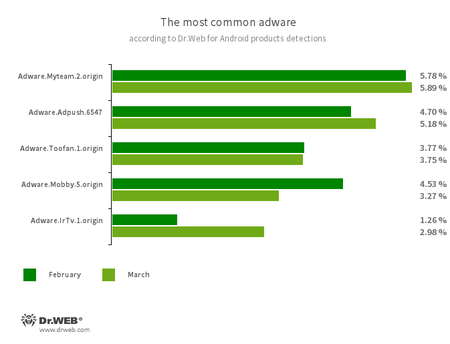
Program modules incorporated into Android applications and designed to display obnoxious ads on Android devices:
- Adware.Myteam.2.origin
- Adware.Adpush.6547
- Adware.Toofan.1.origin
- Adware.Mobby.5.origin
- Adware.IrTv.1.origin
Threats on Google Play
In March, a new modification of the Android.Joker trojan family, dubbed Android.Joker.102.origin, was found on Google Play among other threats. It was spread as an image editing software and wallpapers collections application. This malware was able to download and launch additional trojan components, execute arbitrary code and subscribe users to premium services.
To protect your Android device from malware and unwanted programs, we recommend installing Dr.Web for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products