June 2019 mobile malware review from Doctor Web
July 3, 2019
In mid June, Dr.Web virus analysts discovered the Android.FakeApp.174 malware on Google Play. It loaded websites where Android device users were signed up for spam notifications. Also this month, new trojans from the Android.HiddenAds family were found, intended to display ads, as well as the Android.DownLoader trojan downloaders, which downloaded other malicious applications. There were other Android threats as well.
PRINCIPAL TREND IN JUNE
- New malicious and unwanted applications on Google Play
Mobile threat of the month
On June 14, Doctor Web reported the Android.FakeApp.174 trojan that loaded questionable websites. Android device users were tricked into subscribing to notifications. If they agreed, the victims started receiving dozens of spam messages that could be mistaken for notifications from previously installed programs or the operating system.
Clicking such a message would open one of the advertised websites in the browser. Many of them were fraudulent.
Features of Android.FakeApp.174:
- it is distributed via Google Play under the guise of official software by well-known brands;
- notifications from websites, loaded by the trojan, did not stop when the trojan was removed.
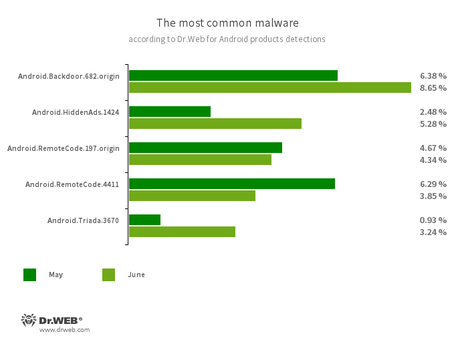
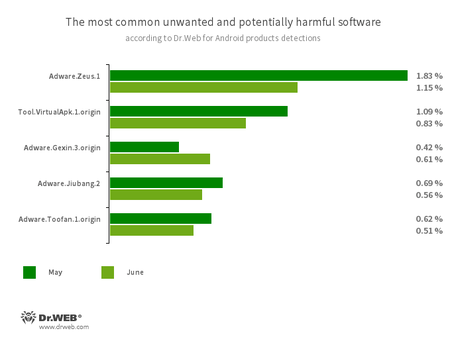
According to statistics collected by Dr.Web for Android
- Android.Backdoor.682.origin
- A trojan that executes cybercriminals’ commands and helps them control infected mobile devices.
- Android.HiddenAds.1424
- A trojan designed to display obnoxious ads. It is distributed under the guise of popular applications.
- Android.RemoteCode.197.origin
- Android.RemoteCode.4411
- Malicious applications designed to download and execute arbitrary code.
- Android.Triada.3670
- A multi-functional trojan that performs different malicious actions.
Program modules that incorporate themselves into Android applications and display obnoxious ads on mobile devices:
- Adware.Zeus.1
- Adware.Jiubang.2
- Adware.AdPush.33.origin
- Adware.Toofan.1.origin
A riskware platform that allows applications to launch APK files without installing them:
- Tool.VirtualApk.1.origin
A new threat:
- Adware.Patacore.253
- A representative of a family of unwanted modules that display banner advertisments on Android devices.
Threats on Google Play
Along with Android.FakeApp.174, other malicious and unwanted programs were found on Google Play, including trojans of the same family, dubbed Android.FakeApp.151 and Android.FakeApp.173. They were distributed under the guise of programs that allowed users to earn money for participating in online polls. When launched, the malware loaded fraudulent websites where potential victims were asked to answer a few questions. To receive a “reward”, they were required to pay a certain tax or commission, but they ultimately never received any money.
Virus analysts have also discovered a number of new Android.HiddenAds trojans. The attackers disguised them as useful applications, such as various games and utilities. Overall, they were installed by more than 3,380,000 users.
After installation and launch, the malware hid its icons and began displaying ads.
Another trojan found on Google Play was named Android.DownLoader.3200. It was built into the software for LETSCOM Smart Bracelet and installed by over 50,000 users.
The first versions of this application were safe; but later, in versions 1.1.0 and 1.1.4, it was updated with trojan functionality. Android.DownLoader.3200 downloaded other trojans to mobile devices.
Another downloader was named Android.DownLoader.681.origin. Like Android.DownLoader.3200, it was distributed as a safe program, an audio player in this case. Android.DownLoader.681.origin downloaded malicious applications and tried to install them.
At the end of June, the Dr.Web virus database was updated to detect the Adware.OneOceans.2.origin unwanted program module, intended to display ads. It was built into the Toy Blast: Cube Smash game, downloaded by over 100,000 users.
To protect your Android device from malware and unwanted programs, we recommend you install Dr.Web for Android.

Your Android needs protection.
Use Dr.Web
- The first Russian anti-virus for Android
- Over 140 million downloads—just from Google Play
- Available free of charge for users of Dr.Web home products