March 2019 mobile malware review from Doctor Web
April 3, 2019
In March, Doctor Web reported a vulnerability in the mobile app, UC Browser, which can download new modules from third-party server. Cybercriminals could use this feature to infect Android smartphones and tablets. Additionally, malware analysts shared information about the Flexnet trojan that stole money from bank cards and mobile credit accounts. During March, other malicious applications were detected on Google Play.
PRINCIPAL TRENDS IN MARCH
- Detection of a vulnerability in UC Browser
- Distribution of banking trojans
- The detection of new malicious programs on Google Play
Mobile threat of the month
At the end of March, Doctor Web reported a vulnerability in the UC Browser app for Android, discovered by our malware analysts. This program downloaded additional plugins, bypassing Google Play servers and thus violating Google’s policies. Cybercriminals could interfere with the download and make the browser download and launch malicious files instead. Over 500,000,000 mobile users have been exposed to threats. See the details of this vulnerability in our virus library.
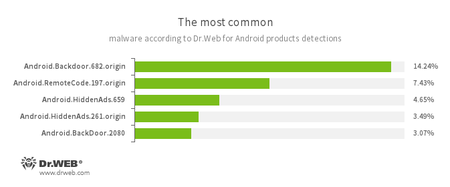
According to statistics collected by Dr.Web for Android
- Android.Backdoor.682.origin
- Android.Backdoor.2080
- Trojans that execute commands from attackers and allow them to control infected mobile devices.
- Android.RemoteCode.197.origin
- Malicious application designed to download and execute arbitrary code.
- Android.HiddenAds.659
- Android.HiddenAds.261.origin
- Trojans designed to display intrusive advertisements. They are distributed as popular applications by other malicious programs, which in some cases covertly install them in the system catalog.
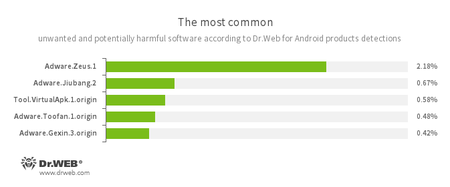
- Adware.Zeus.1
- Adware.Jiubang.2
- Adware.Toofan.1.origin
- Adware.Gexin.3.origin
- Unwanted program modules that incorporate themselves into Android applications and display obnoxious ads on mobile devices.
- Tool.VirtualApk.1.origin
- A potentially dangerous software platform that allows applications to run APK files without installing them.
Banking trojans for Android
Cybercriminals continue to distribute banking trojans based on the source code of the Android.ZBot malware. One of them is the Flexnet trojan. It steals money from bank cards and can also transfer money from victims' mobile credit accounts to pay for various services. For example, it can help cybercriminals top up the balance of gaming accounts, pay for hosting services, and pay for their own mobile plans. Read more about the Flexnet banking trojan in the news article on our website.
Threats on Google Play
In March, we found more malicious programs on Google Play, including the trojans Android.FakeApp.152 and Android.FakeApp.162, which loaded fraudulent websites. Those websites invite users to take polls for payment in return. To receive money, potential victims are required to make some kind of a verification payment; but in fact, users only transfer the funds to fraudsters and do not receive any reward.
In addition, our malware analysts identified more trojans of the Android.HiddenAds family, including Android.HiddenAds.1133, Android.HiddenAds.1134, Android.HiddenAds.1052, and Android.HiddenAds.379.origin. Our company already reported similar malware in February. These trojans are distributed under the guise of useful applications, such as photo and video editors, camera filters, flashlights, sports software, etc.
After installation and launch, they hide their icons and begin constantly overlaying ads over program windows and the operating system interface, making it difficult to work with the Android devices.
Users of Android devices are threatened by trojans not only distributed via malicious websites, but also via the official Google Play store. To protect smartphones and tablets, we recommend that you install Dr.Web for Android.
Your Android needs protection!
Use Dr.Web
- First Russian anti-virus for Android
- Over 140 million downloads—just from Google Play!
- Available free of charge for users who purchase Dr.Web home products