Doctor Web’s January 2019 virus activity review
February 1, 2019
2018 may have been a rollercoaster in terms of info security and privacy, but at the end of the year, we finally witnessed a long-awaited break. Cybercriminals decreased their activity during the holidays; but despite that, our statistics show a few peculiar and disturbing trends for January.
In the middle of the month, cryptocurrency holders were attacked by a monitoring tool that was disguised as a downloader Trojan. Later this month we registered a 28% increase in devices infected with the Trojan.Winlock.14244. Beyond that, our email traffic statistics show a 50% higher rate of distribution of malicious documents exploiting Microsoft Office vulnerabilities.
Principal trends in January
- Increased number of devices infected by OS blockers
- More frequent use of Microsoft Office exploits
- Spike of adware activity
Threat of the month
In January Doctor Web’s researchers discovered a Trojan in a cryptocurrency monitoring tool. This malware downloaded other Trojans on a victim’s PC and used them to steal private data, including passwords from cryptocurrency wallets.
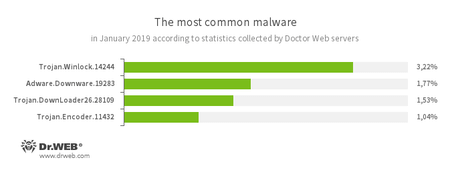
According to Doctor Web’s statistics servers
Growing threats of the month:
- Trojan.Winlock.14244
- Ransomware Trojan. Blocks or limits user’s access to the Windows operating system, and its functionalities. In order to unlock the system, a user must transfer money to the cybercriminals.
- Adware.Downware.19283
- The sort of adware that is usually distributed as an installer for pirated software. Upon installation, it changes a browser’s settings and may install other software without asking for the user’s permission.
- Trojan.DownLoader26.28109
- Downloads and runs malicious software without the user’s permission.
- Trojan.Encoder.11432
- Infamous ransomware also known as WannaCry. Blocks access to users’ data by encrypting it and demanding payment for decrypting the data.
Decreased amount of threats from:
- Trojan.Starter.7394
- Trojan designed for launching other malicious software on a victim’s device.
- Trojan.MulDrop8.60634
- Installs malware in a system. All the components necessary for installation are usually stored inside the MulDrop itself.
- Trojan.Zadved.1313
- Adware. Alters search results and redirects users to advertising websites.
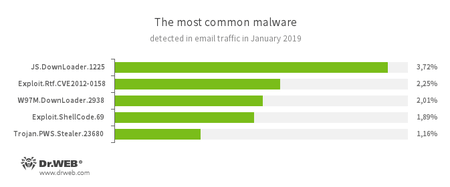
Statistics for malware discovered in email traffic
Increased number of threats from:
- JS.DownLoader.1225
- A variety of malicious code written in JavaScript and designed to download and install other malware on a computer.
- Exploit.Rtf.CVE2012-0158
- Modified Microsoft Office document. Exploits CVE2012-0158 vulnerability in order to run malicious code.
- W97M.DownLoader.2938
- A family of downloader Trojans that exploit vulnerabilities in office applications and can download other malicious programs to a compromised machine.
- Exploit.ShellCode.69
- Another malicious Microsoft Office Word document. This one uses vulnerability called CVE-2017-11882.
- Trojan.PWS.Stealer.23680
- A family of Trojans designed to steal passwords and other confidential information stored on an infected computer.
Increased activity of following threats:
- Trojan.Nanocore.23
- This dangerous malware is from a remote access Trojan family(RAT). It has infected 4 times more devices than in the previous month. Nanocore allows complete remote control of an infected device, including control over the camera and microphone.
- JS.Miner.28
- Malicious JavaScript code. Its purpose is to mine Monero cryptocurrency in a browser without asking for a user’s permission. Often used as an alternative to the CoinHive miner.
Decreased the number of threats from:
- Trojan.Fbng.8
- The Trojan also known as FormBook. It’s designed to steal private data, but can also receive commands from the developer’s server.
- Trojan.Encoder.26375
- A malicious program from the encryption ransomware family. This Trojans encrypts files and demands a ransom for data decryption.
- JS.Miner.11
- This name belongs to a group of malicious JavaScript code. Its purpose is to mine Monero cryptocurrency in a browser without asking for a user’s permission. Uses CoinHive miner.
Trojan.SpyBot.699 multi-module banking Trojan was less active during December, but continued to spread in January. It was created to help cybercriminals download and launch various applications on an infected device, as well as execute different commands. The Trojan is intended to steal money from bank accounts.
Encryption ransomware
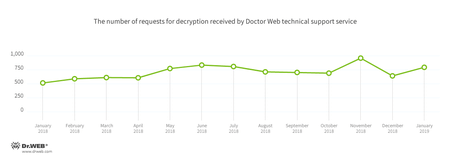
In January, Doctor Web’s technical support was most often contacted by victims of the following encryption ransomware:
- Trojan.Encoder.858 — 26.32% of requests;
- Trojan.Encoder.11464 — 12.63% of requests;
- Trojan.Encoder.11539 — 7.72% of requests;
- Trojan.Encoder.25574 — 1.58% of requests;
- Trojan.Encoder.567 — 5.96% of requests;
- Trojan.Encoder.5342 — 0.88% requests;
Dr.Web Security Space for Windows protects against encryption ransomware
Dangerous websites
During January 2019, 293,012 URLs of non-recommended websites were added to the Dr.Web database.
| December 2018 | January 2019 | Dynamics |
|---|---|---|
| + 257 197 | + 293 012 | +13.93% |
Malicious and unwanted programs for mobile devices
Throughout January InfoSec researchers continued discovering malware apps hidden in the Google Play Store. Among them — downloaders from the Android.DownLoader family that were deploying Android banking malware on victim devices. Another threat worth mentioning is adware. In particular, Android.HiddenAds.361.origin and Android.HiddenAds.356.origin. When launched they disappear from the desktop and begin to show ads. In the end of the month cybersecurity researchers uncovered a few new trojan-clickers( Android.Click), capable of loading any website on a developer’s command. To top it all off, new spyware was caught stealing private information from users - Trojan named Android.Spy.525.origin.
Among the most notable January events related to mobile malware we can report the following:
- The detection of new Android Trojans on Google Play;
- Distribution of a dangerous spyware.
Find out more about malicious and unwanted programs for mobile devices in our special overview.