Doctor Web’s overview of malware detected on mobile devices in December 2018
December 28, 2018
In early December, Brazilian Android device users were threatened by a banking Trojan that spread via Google Play. Some other malicious applications were detected in the official Android app store as well. At the end of December, Doctor Web experts discovered a new version of commercial spyware that collects masses of confidential information.
PRINCIPAL TRENDS IN DECEMBER
- Distribution of new dangerous banking Trojan among Brazilian users
- Detection of a new version of potentially dangerous spyware for surveilling mobile device users
- Detection of malicious and unwanted applications on Google Play
Mobile threat of the month
In early December, virus analysts investigated the banking Trojan, Android.BankBot.495.origin, which attacked customers of Brazilian financial institutions. This malware tried to obtain access to the Android Accessibility Service and use it to independently manage banking apps, read the contents of their windows, and transfer confidential information to attackers. Moreover, Android.BankBot.495.origin laid phishing windows over applications and tricked users into providing their credentials, bank card details, and other confidential data.
Read more about this Trojan in the news article, published by Doctor Web.
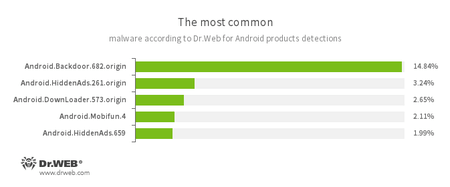
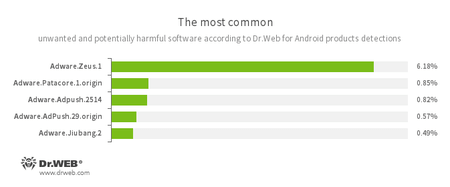
According to statistics collected by Dr.Web for Android
- Android.Backdoor.682.origin
- A Trojan that executes cybercriminals’ commands and helps them control infected mobile devices.
- Android.HiddenAds.261.origin
- Android.HiddenAds.659
- Trojans designed to display intrusive advertisements. They are distributed under the guise of popular applications by other malicious programs, which in some cases covertly install themselves in the system catalog.
- Android.DownLoader.573.origin
- A Trojan that downloads other malware applications.
- Android.Mobifun.4
- A Trojan that downloads various applications.
- Adware.Zeus.1
- Adware.Patacore.1.origin
- Adware.Adpush.2514
- Adware.AdPush.29.origin
- Adware.Jiubang.2
- Unwanted program modules that incorporate themselves into Android applications and display obnoxious ads on mobile devices.
Threats on Google Play
A lot of malicious and unwanted programs were detected on Google Play over the month. The list includes the adware Trojans Android.HiddenAds.343.origin and Android.HiddenAds.847, distributed under the guise of games and useful applications. When launched, they hid their icon from the home screen and began displaying ads.
We have also detected programs with the unwanted modules Adware.Patacore and Adware.HiddenAds. They displayed ads even when the software containing them was not running. In total, more than 5,300,000 users installed these programs.
Cybercriminals kept spreading fraudulent applications. The Dr.Web virus database has been updated to detect the Trojans Android.FakeApp.149, Android.FakeApp.151, and Android.FakeApp.152. These malicious programs launched web pages where the potential victims were asked to answer a few questions for a reward. To receive the reward payment, a user was first required to transfer a verification payment, but they never received anything in return.
Virus analysts have also discovered the Trojan Android.Proxy.4.origin, which helped virus writers redirect traffic via other users’ smartphones and tablets. Android.Proxy.4.origin was hiding in seemingly harmless games.
Cyberespionage
Among the potentially dangerous programs detected in December was a new version of the commercial spyware Program.Spyzie.1.origin, which allows you to monitor Android device users. It intercepts and reads text messages and emails; it tracks phone calls, web browser history and coordinates of infected smartphone or tablets. It also accesses message history in popular online messengers and steals other information.
Android users are targeted by various malicious and unwanted programs, distributed both online and via Google Play. Apart from that, attackers can install malware themselves if they get physical access to mobile devices. To protect smartphones and tablets, we recommend users install Dr.Web for Android.
Your Android needs protection
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 140 million downloads on Google Play alone
- Free for users of Dr.Web home products