Doctor Web’s overview of malware detected on mobile devices in September 2018
September 28, 2018
In September 2018 Doctor Web virus analysts detected numerous Trojans on Google Play. Different banking Trojans also posed a threat to mobile users this month. Also in September, cybercriminals distributed a dangerous Trojan designed for cyber spying. The same month records for detecting new versions of known commercial spyware programs were added to the Dr.Web virus databases.
PRINCIPAL TRENDS IN SEPTEMBER
- The detection of malicious programs on Google Play.
- The spread of a dangerous spyware Trojan.
- The detection of new versions of commercial programs designed for cyber spying.
Mobile threat of the month
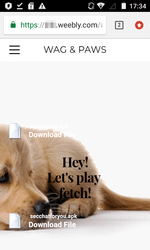
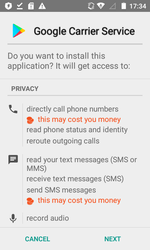
A dangerous spyware Trojan Android.Spy.460.origin posed a threat to users of mobile Android devices. The Trojan was first detected by Doctor Web virus analysts in June 2018. This malware is distributed using the fraudulent websites under the guise of system applications, for example, under the name of “Google Carrier Service”.
Android.Spy.460.origin tracks SMS correspondence and the location of the infected smartphone or tablet, wiretaps phone calls, records the surrounding environment using the built-in device microphone, steals data from the phonebook and calendar, sends web browser history and bookmarks to cybercriminals.
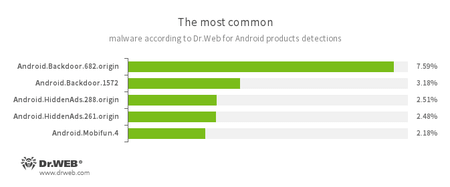
According to statistics collected by Dr.Web for Android
- Android.Backdoor.682.origin
- Android.Backdoor.1572
- The Trojans that execute cybercriminals’ commands and help them to control infected mobile devices.
- Android.HiddenAds
- The Trojans, designed to display intrusive advertising. They are distributed under the guise of popular applications by other malicious programs, which in some cases quietly, install themselves in the system catalog.
- Android.Mobifun.4
- A Trojan that downloads other malware applications.
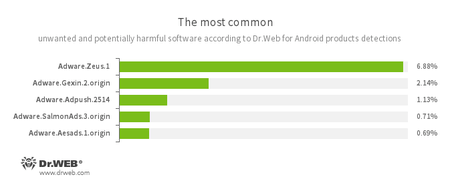
- Adware.Zeus.1
- Adware.Gexin.2.origin
- Adware.Adpush.2514
- Adware.SalmonAds.3.origin
- Adware.Aesads.1.origin
- Unwanted program modules incorporated into Android applications and designed to display obnoxious ads on mobile devices.
Threats on Google Play
The past month saw lots of malicious programs detected on Google Play. Doctor Web specialists have detected Trojans from the Android.Click family once again. Cybercriminals distributed them under the guise of official bookmaker apps. Apart from the already known Trojans (that we discussed in August) virus analysts detected 17 new modifications. In total, at least 62,000 users installed malicious applications.
Once launched, these Trojans load bookmaker websites in their windows upon the command of the C&C server and show them to users. However, the server can send a command to open another internet resource at any moment, which can pose a serous threat.
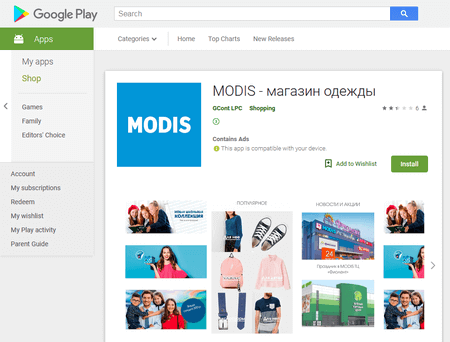
In addition, among other clicker Trojans, Android.Click.265.origin (that we have also informed about) managed to get on Google Play. Android.Click.265.origin loads websites with premium content and subscribes users to expensive services. For that, it automatically clicks the confirmation button to access the paid service in the opened windows. In September, cybercriminals distributed this malware under the guise of apps by known Russian companies, such as Sitilink (e-commerce), MODIS and O’STIN (clothing retailers).
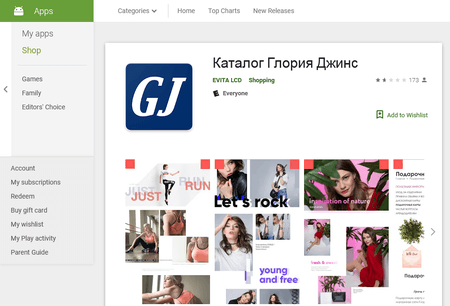
One more Trojan with a similar functionality to Android.Click.265.origin was dubbed Android.Click.223.origin. Virus writers also distributed it under the guise of a harmless program on behalf of the Russian clothing retailers, Gloria Jeans and TVOE.
In September, banking Trojans were detected on Google Play again. Android.Banker.2855 and Android.Banker.2856 were among them. They were distributed as server utilities and horoscopes. These malicious programs extract and launch a hidden banker that steals login credentials of client accounts in credit organizations.
One more banking Trojan that managed to get on Google Play was dubbed Android.Banker.283.origin. Virus writers pass it off as an official app by one of the Turkish organizations.
Spyware
In September, new versions of commercial spyware programs, such as Program.SpyToMobile.1.origin, Program.Spy.11, Program.GpsSpy.9, Program.StealthGuru.1, Program.QQPlus.4, Program.DroidWatcher.1.origin, Program.NeoSpy.1.origin, Program.MSpy.7.origin, and Program.Spymaster.2.origin were detected. They are designed to spy on users of Android mobile devices. For example, these applications allow cybercriminals to intercept SMS correspondence, track phone calls and location of smartphones and tablets, get access to the web browser history and bookmarks, and steal confidential information.
Cybercriminals constantly create new Trojans and riskware to infect users of Android smartphones and tablets. Many of these applications are still available on Google Play. Doctor Web recommends that device owners install Dr.Web for Android to protect their mobile devices.
Your Android needs protection
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 135 million downloads on Google Play alone
- Free for users of Dr.Web home products