Doctor Web’s July 2018 virus activity review
July 31, 2018
In early July, Doctor Web virus analysts have analyzed a new Trojan-Miner that used an unusual spreading pattern. Also, during this month, spammers were active with fraudulent sites advertising. Besides, in July Dr.Web virus databases have replenished with new malware entries, oriented to the Android mobile platform.
Principal trends in July
- The detection of dangerous Trojan-Miner
- Fraudulent mailings distribution
- Emergence of new malware for Android
Threat of the month
Our security specialists have already faced the spread of malware through the application update mechanism. This is how Trojan.Encoder.12544 (Petya, Petya.A, ExPetya and WannaCry-2), and the backdoor BackDoor.Dande, have reached users. In July, the Doctor Web technical support was contacted by a user on whose computer the application for crypto-currency mining was constantly appearing despite being removed by the antivirus every time. The investigation made by analysts testified that the culprit was a certain Computer room, a program for the automation of computer clubs and Internet cafes.
The update mechanism for this program was automatically downloading and installing the Trojan-Miner Trojan.BtcMine.2869. On July 9, Doctor Web specialists have found 2700 computers infected with this Trojan. More detailed information about this incident is stated in the article published on our website.
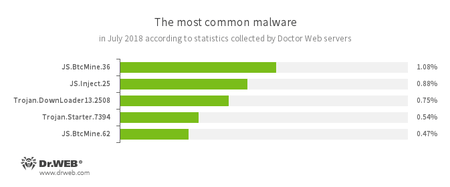
According to Doctor Web’s statistics servers
- JS.BtcMine.7
- A family of JavaScript scenarios designed to stealthily mine cryptocurrencies (mining).
- JS.Inject
- A family of malicious JavaScripts that injects a malicious script into the HTML code of webpages.
- Trojan.DownLoader
- A family of malicious programs designed to download other malware to the compromised computer.
- Trojan.Starter.7394
- A Trojan family representative which main purpose is to launch in an infected system with an executable file possessing a specific set of malicious functions.
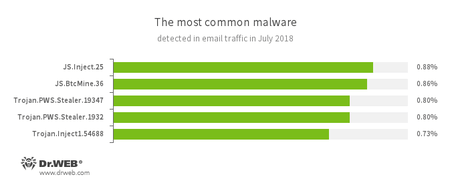
Statistics concerning malicious programs discovered in email traffic
- JS.Inject
- A family of malicious JavaScripts that injects a malicious script into the HTML code of webpages.
- JS.BtcMine.7
- A family of JavaScript scenarios designed to stealthily mine cryptocurrencies (mining).
- Trojan.PWS.Stealer
- A family of Trojans designed to steal passwords and other confidential information stored on an infected computer.
- Trojan.Inject
- A family of Trojans that inject malicious code into the processes of other programs.
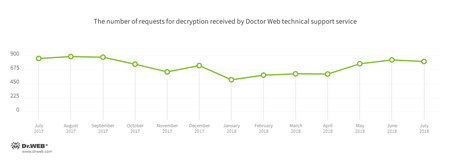
Encryption ransomware
In July, the most often cases involving the following ransomware modifications were registered by Doctor Web’s technical support service:
- Trojan.Encoder.858 — 17.69% requests;
- Trojan.Encoder.25574 — 11.38% requests;
- Trojan.Encoder.11464 — 8.06% requests;
- Trojan.Encoder.567 — 5.08% of requests;
- Trojan.Encoder.5342— 3.85% requests;
- Trojan.Encoder.24249 — 3.33%requests.
Dr.Web Security Space for Windows protects against encryption ransomware
Dangerous websites
In July, Doctor Web specialists have detected several mass mailings which contained the advertisement of various fraudulent resources. Particularly, spammers sent messages allegedly on behalf of the Yandex company with a proposal to confirm the binding of the mail address to the account on the passport.yandex.ru portal. At the same time, the link on which scammers offered recipients to go to, did indeed lead to the Yandex portal. Meanwhile, another link, allegedly announcing the receipt of a certain prize, led a potential victim to the site of network scammers requiring to pay a small cash contribution for the gift they promised.
In a number of other fraudulent messages, there were links to pages of public services like Google Docs where attackers placed a web page with a picture mimicking reCAPCHA, the standard panel of automatic protection against robots. Clicking on this picture redirected users to various phishing sites.
Doctor Web analysts detected the addresses of fraudulent Internet resources and added all of them to the Dr.Web Parental Control and Office Control’s databases of non-recommended websites.
During March 2018, Doctor Web added 624,474 URLs into the Dr.Web database of non-recommended sites.
| june 2018 | july 2018 | Dynamics |
|---|---|---|
| + 395 477 | + 512 763 | +29.6% |
Malicious and unwanted programs for mobile devices
In the parting month in the Google Play catalogue several dangerous malicious programs have been detected. One of the was the Trojan Android.Banker.2746, which showed a fake window for entering personal data when launching banking applications. The othe Trojan, named Android.DownLoader.753.origin, has been downloading Android-bankers from the server of cybercriminals in order to avoid detection of the main malicious program on Google Play. Among the Trojans distributed in July were other bankers as well. One of them – Android.BankBot.279.origin. It was downloaded on users mobile devices when visiting fraudulent sites. Also, in July in Dr.Web anti-virus base the entry to detect malicious application-backdoorAndroid.Backdoor.554.origin was added. In addition, in the parting month, Doctor Web specialists discovered and investigated several new programs designed for cyber espionage. They received the names Program.Shadspy.1.origin and Program.AppSpy.1.origin.
Among the most notable July events related to mobile malware:
- the detection of Trojans on Google Play;
- the distribution of a banking Trojans for Android;
- the distribution of Android backdoor, which has been used by cybercriminals to infest the computers running on Windows;
- the detecting of new commercial programs-spies.
Find out more about malicious and unwanted programs for mobile devices in our special overview.