June 2018 mobile malware review from Doctor Web
July 3, 2018
In June 2018 Doctor Web virus analysts detected more than 30 apps containing an unwanted advertisement module Adware.Appalytic.1.origin on Google Play. It showed notifications offering to download different software and opened pages of advertised programs. In addition, Doctor Web specialists found several new representatives of the Trojan family Android.FakeApp that loaded different websites on cybercriminals’ command. Last month cybercriminals also distributed the Trojan Android.Spy.461.origin guised under an erotic game that spied on Android smartphone and tablet owners. Additionally, the Trojan Android.SmsSend.1989.origin posed a threat to Android mobile device users in June. It sent paid SMS messages to premium numbers.
PRINCIPAL TRENDS IN JUNE
- Detection of even more applications containing an unwanted embedded advertising module on Google Play
- Distribution of a dangerous spyware
Mobile threat of the month
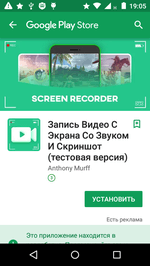
In early June Doctor Web specialists detected 37 new applications on Google Play containing an unwanted advertisement module Adware.Appalytic.1.origin. It insisted on downloading and installing different applications and games. In addition, Adware.Appalytic.1.origin could independently open advertised pages on Google Play.
The following example shows an advertised Google Play application:
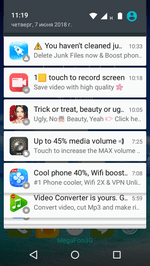
Examples of notifications that the module shows:
Features of Adware.Appalytic.1.origin:
- embedded into benign applications distributed via Google Play;
- receives commands via the Firebase cloud service;
- independently opens Google Play and loads pages of advertised apps;
- shows obnoxious messages offering to download and install different programs in the notifications panel.
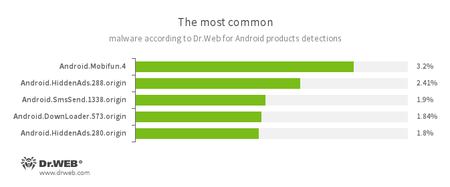
According to statistics collected by Dr.Web for Android
- Android.Mobifun.4
- A Trojan designed to download other Android applications.
- Android.HiddenAds.280.origin
- Android.HiddenAds.288.origin
- Adware Trojans spread under the guise of benign software by other malicious programs that, in some instances, covertly install the Trojans in the system directory.
- Android.SmsSend.1338.origin
- A malicious program that sends SMS messages to paid numbers.
- Android.DownLoader.573.origin
- A Trojan designed to download other malware.
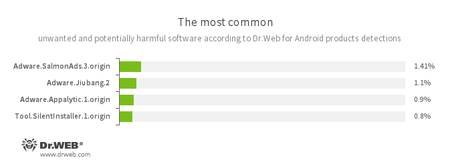
- Adware.SalmonAds.3.origin
- Adware.Jiubang.2
- Adware.Appalytic.1.origin
- Unwanted program modules incorporated into Android applications and designed to display obnoxious ads on mobile devices.
- Tool.SilentInstaller.1.origin
- Riskware designed to silently launch applications without user intervention.
Trojans on Google Play
In late June Doctor Web specialists detected several new representatives of the Trojan family Android.FakeApp. As before, these malicious programs were distributed under the guise of useful applications, in particular, as media players for listening to music from the VK social network. The Trojans added to the Dr.Web virus database as Android.FakeApp.89, Android.FakeApp.90, Android.FakeApp.91, and Android.FakeApp.92 would follow the links they specified and load websites, including fraudulent Internet resources on the cybercriminals’ command.
The following screenshots show the download pages of the Android.FakeApp Trojans detected on Google Play:
Android spyware
In June a Trojan spyware guised as an erotic game posed a threat to Android smartphone and tablet users. This malware was dubbed Android.Spy.461.origin. The Trojan stole SMS messages and contacts from the phonebook, recorded the surrounding environment using the mobile device’s microphone, received a list of files stored on the smartphone or tablet, and loaded them on the cybercriminals’ server. In addition, Android.Spy.461.origin stole data from the clipboard.
SMS Trojan
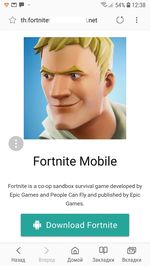
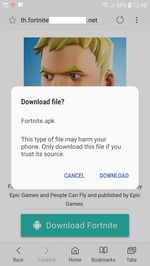
Last month cybercriminals distributed an SMS Trojan Android.SmsSend.1989.origin. It sent messages to paid numbers and subscribed users to expensive services. The malware was hidden in the app that cybercriminals passed off as the popular game Fortnite, while its official version for Android is still unavailable for users.
Cybercriminals still attack Android mobile devices and distribute malicious and unwanted applications using not only different websites, but also an official Google Play store. Doctor Web recommends users install Dr.Web for Android to protect their mobile devices.
Your Android needs protection
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 135 million downloads on Google Play alone
- Free for users of Dr.Web home products