May 2018 mobile malware review from Doctor Web
May 31, 2018
In May 2018 Doctor Web specialists found several Google Play applications containing the Trojan Android.Click.248.origin. It loaded fraudulent websites on which users subscribed to expensive mobile services. Also detected on Google Play was the malicious program Android.FakeApp, which was being distributed under the guise of a popular software program. It followed links as instructed by cybercriminals and inflated the traffic counters of websites it visited. Among the other threats found in the official Android application catalog were Trojans from the Android.HiddenAds family. These are designed to display advertisements. Also in the last month, security researchers found the Trojans Android.Spy.456.origin and Android.Spy.457.origin, which are used by cybercriminals for cyberespionage. In late May, the signature of the new commercial spyware program Program.OneSpy was added to the Dr.Web virus database.
PRINCIPAL TRENDS IN MAY
- The detection of yet more Trojans on Google Play
- The detection of a new version of Android spyware
Mobile threat of the month
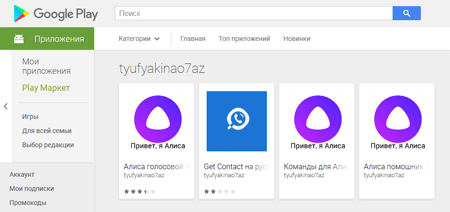
In the last month, Doctor Web specialists detected the Trojan Android.Click.248.origin on Google Play; it was being distributed by cybercriminals under the guise of such popular programs as Skype and Alisa (the Yandex voice assistant, which is not actually available as a separate application).
The Trojan loaded fraudulent websites where users would subscribe to paid services. You can read about similar malicious applications in an article published by Doctor Web in April.
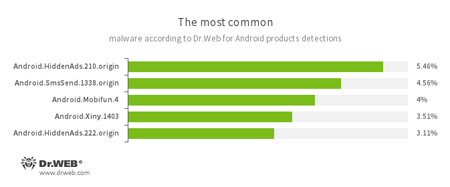
According to statistics collected by Dr.Web for Android
- Android.HiddenAds.210.origin
- Android.HiddenAds.222.origin
- Trojans designed to display unwanted ads on mobile devices. They are distributed under the guise of popular apps by other malicious programs, which sometimes covertly install them in the system directory.
- Android.SmsSend.1338.origin
- A malicious program that sends SMS messages to paid numbers.
- Android.Mobifun.4
- A Trojan designed to download other Android applications.
- Android.Xiny.1403
- A Trojan designed to covertly download and install other malicious applications.
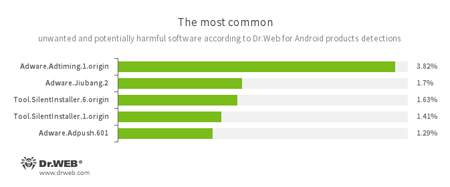
- Adware.Adtiming.1.origin
- Adware.Jiubang.2
- Adware.Adpush.601
- Unwanted program modules incorporated into Android applications and designed to display obnoxious ads on mobile devices.
- Tool.SilentInstaller.1.origin
- Tool.SilentInstaller.6.origin
- Riskware designed to silently launch applications without the user’s action.
Threats on Google Play
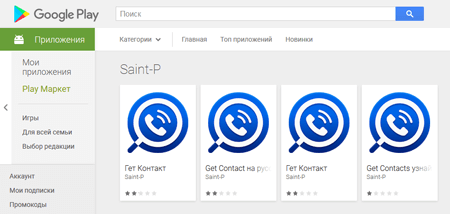
In May Doctor Web specialists found on Google Play Android.FakeApp, which was being spread under the guise of popular applications. When commanded by cybercriminals, Android.FakeApp would follow the links they specified and load websites, thus inflating their traffic stats.
The Trojan's unique features are as follows:
- Created with the help of the AppsGeyser service, which makes it possible to build simple Android programs in several easy steps;
- Distributed under the guise of popular applications;
- Contained no useful features;
- Revealed the 7 developers on whose behalf the Trojan was distributed on Google Play.
Examples of fake applications found on Google Play:
Also in May, the official Android software catalog was found to be infected with more representatives of the Android.HiddenAds Trojan family, e.g., Android.HiddenAds.267.origin and Android.HiddenAds.277.origin. These malicious programs were being distributed under the guise of benign and popular applications. The Trojan’s main function is to display advertisements.
Cyberespionage
In the month just ending, security researchers also found several new Android Trojans that cybercriminals were using for cyberespionage. One of them was spread via Google Play and was dubbed Android.Spy.456.origin. The malicious program stole photos, SMS messages and contacts from the contact list of infected devices and loaded them to a cybercriminal-owned remote server. Another mobile spyware Trojan detected in May was added to the Dr.Web virus database as Android.Spy.457.origin. It stole images and videos stored in the memory of Android smartphones and tablets, stole SMS messages, tracked mobile device location coordinates, and could also listen to the surroundings and record phone calls.
In late May Doctor Web specialists detected a new version of the commercial spyware program Onespy, which was dubbed Program.Onespy.3.origin. This application can intercept SMS messages and phone calls; track the location of an infected device; listen to the surroundings; steal photos, videos, documents and other files; and track correspondence in popular messengers, such as Skype, Viber, WhatsApp, Line, Facebook and others. It can also perform other malicious actions.
Despite Google’s efforts, cybercriminals are still managing to spread Android Trojans via Google Play. In addition, malicious and potentially dangerous programs for mobile devices also lie in wait for users outside the official application catalog. Doctor Web recommends that device owners install Dr.Web for Android to protect their smartphones and tablets.
Your Android needs protection
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 135 million downloads on Google Play alone
- Free for users of Dr.Web home products