February 2018 mobile malware review from Doctor Web
February 28, 2018
In February, Doctor Web security researchers detected a miner Trojan that infects different Android devices with the debugging mode enabled. Additionally, in the past month, a Trojan Android.BankBot.336.origin posed a threat to users. This Trojan steals confidential information and money from bank accounts.
PRINCIPAL TRENDS IN FEBRUARY
- Distribution of a miner Trojan that infects some Android devices
- Distribution of a new banking Trojan
Mobile threat of the month
In February, a Trojan Android.CoinMine.15 became widespread. Cybercriminals used the Trojan to mine the Monero cryptocurrency. This malware is designed as a worm and can infect Android smartphones, tablets, TVs, routers, and media players connected to the network. The infection is possible only when the devices have the Android Device Bridge debugging mode enabled (ADB). In cases of successful infection, one of the Trojan’s components tries to detect the next device and install the Trojan’s copy on it.
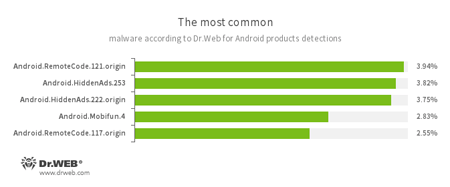
According to statistics collected by Dr.Web for Android
- Android.RemoteCode.121.origin
- Android.RemoteCode.117.origin
- Trojans that download and launch various program modules, including malicious ones.
- Android.HiddenAds.253
- Android.HiddenAds.222.origin
- Adware Trojans spread under the guise of benign software by other malicious programs that, in some instances, covertly install the Trojans in the system directory.
- Android.Mobifun.4
- A Trojan that downloads other malware applications.
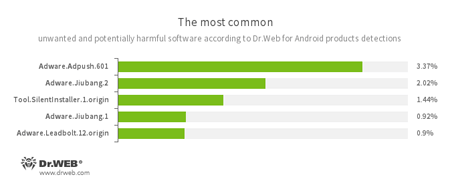
- Adware.Adpush.601
- Adware.Jiubang.2
- Adware.Jiubang.1
- Adware.Leadbolt.12.origin
- Unwanted program modules incorporated into Android applications and designed to display obnoxious ads on mobile devices.
- Tool.SilentInstaller.1.origin
- Riskware designed to silently launch application without the users’s intervention.
Banking Trojan
Over the past month, a Trojan Android.BankBot.336.origin was detected on Google Play. Cybercriminals distributed it as a universal application designed to work with various Internet banking systems. This malicious program steals logins and passwords from user accounts, as well as information about bank cards. After these actions, the Trojan covertly transfers funds from user bank accounts to cybercriminals.
Virus makers continue to refine their malicious programs for Android and distribute them via known and innovative methods. That said, various Trojans can still be found on Google Play. To protect smartphones, tablets, and other devices from such threats we recommend that you install Dr.Web anti-virus products for Android.
Your Android needs protection
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 135 million downloads on Google Play alone
- Free for users of Dr.Web home products