Doctor Web’s October 2017 virus activity review
October 27, 2017
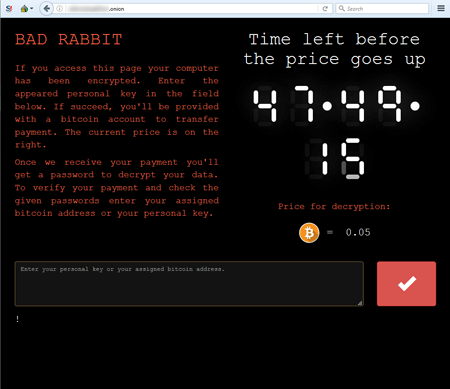
October 2017 will be remembered not only by information security specialists, but also by all Internet users, for the emergence of a new encryption worm named Trojan.BadRabbit. This Trojan started spreading on October 24; the attack mostly involved computers in Russia and Ukraine.
In October, Doctor Web virus analysts examined a backdoor written in Python. This malicious program steals information from popular browsers, logs keystrokes, downloads and saves various files on the infected computers, and performs a number of other malicious functions.
In addition, the specialists investigated a new version of a Linux Trojan that is capable of infecting different “smart” devices.
Principal trends in October
- The new encryption worm BadRabbit
- The emergence of a new backdoor written in Python
- The new Linux Trojan for IoT
Threat of the month
Like its predecessors, Trojan.BadRabbit is a worm capable of independently spreading without any user involvement. It consists of multiple components: a dropper, an encoder-decoder, and the encryption worm itself. A portion of this worm’s code was borrowed from Trojan.Encoder.12544, also known as NotPetya. Once launched, the encoder checks for the availability of the file C:\Windows\cscc.dat, and if this file is present, the Trojan shuts itself down (thus, creating the file cscc.dat in the C:\Windows folder can avert the malicious consequences of the Trojan’s launch).
According to some researchers, the source of Trojan.BadRabbit was a number of compromised websites whose HTML code was injected with a malicious JavaScript. The encoder encrypts files with the following extensions: .3ds, .7z, .accdb, .ai, .asm, .asp, .aspx, .avhd, .back, .bak, .bmp, .brw, .c, .cab, .cc, .cer, .cfg, .conf, .cpp, .crt, .cs, .ctl, .cxx, .dbf, .der, .dib, .disk, .djvu, .doc, .docx, .dwg, .eml, .fdb, .gz, .h, .hdd, .hpp, .hxx, .iso, .java, .jfif, .jpe, .jpeg, .jpg, .js, .kdbx, .key, .mail, .mdb, .msg, .nrg, .odc, .odf, .odg, .odi, .odm, .odp, .ods, .odt, .ora, .ost, .ova, .ovf, .p12, .p7b, .p7c, .pdf, .pem, .pfx, .php, .pmf, .png, .ppt, .pptx, .ps1, .pst, .pvi, .py, .pyc, .pyw, .qcow, .qcow2, .rar, .rb, .rtf, .scm, .sln, .sql, .tar, .tib, .tif, .tiff, .vb, .vbox, .vbs, .vcb, .vdi, .vfd, .vhd, .vhdx, .vmc, .vmdk, .vmsd, .vmtm, .vmx, .vsdx, .vsv, .work, .xls, .xlsx, .xml, .xvd, .zip. As a result of the Trojan's operation, the infected computer displays a demand for a ransom in Bitcoin, and a cybercriminal-operated website in TOR states that the victim has 48 hours to pay. When the time expires, the ransom is increased.
Currently, Trojan.BadRabbit is still being examined. However, Dr.Web Anti-virus successfully detects and removes this malicious program. In addition, an analysis of the Trojan has shown that it checks for the presence of the Dr.Web and McAfee anti-viruses in a system. If Trojan.BadRabbit detects our product, it skips the encryption stage in user mode but attempts to run full encryption after a system restart. This function of the malicious program is blocked by Dr.Web Anti-virus. Thus, users of Dr.Web Anti-virus 9.1 and later and Dr.Web Katana are not exposed to the actions of this encryption Trojan provided that they have not disabled the preventive protection component or changed its settings.
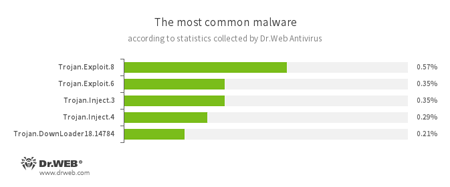
According to Dr.Web Anti-virus statistics
- Trojan.Exploit
- Heuristic detection for exploits that use various vulnerabilities to compromise legitimate applications.
- Trojan.Inject
- A family of malicious programs that inject malicious code into the processes of other programs.
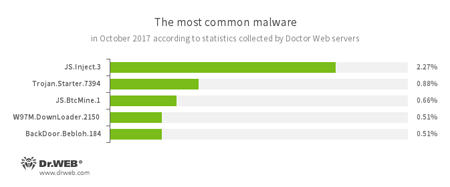
According to Doctor Web’s statistics servers
- JS.Inject.3
- A family of malicious JavaScripts. They inject malicious script into the HTML code of webpages.
- Trojan.Starter.7394
- A Trojan whose main purpose is to launch in an infected system an executable file possessing a specific set of malicious functions.
- JS.BtcMine.1
- A JavaScript designed to stealthily mine cryptocurrencies (mining).
- W97M.DownLoader
- A family of downloader Trojans that exploit vulnerabilities in office applications. Designed for downloading other malware to a compromised computer.
- BackDoor.Bebloh.184
- A malicious program belonging to the banking Trojan family. This application poses a threat to users of e-banking services (RBS) because it allows attackers to steal confidential information by intercepting data submitted through forms in the browser window and by embedding its code into bank webpages.
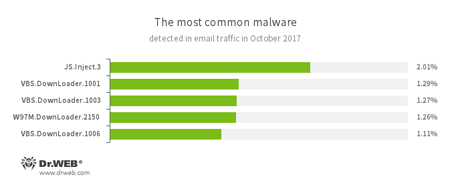
Statistics concerning malicious programs discovered in email traffic
- JS.Inject.3
- A family of malicious JavaScripts. They inject malicious script into the HTML code of webpages.
- VBS.DownLoader
- A family of malicious JavaScripts. They download and install malicious software on a computer.
- W97M.DownLoader
- A family of downloader Trojans that exploit vulnerabilities in office applications. Designed for downloading other malware to a compromised computer.
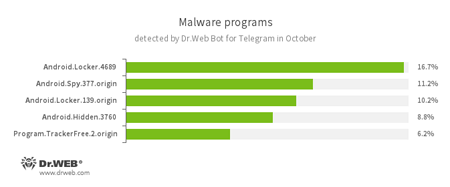
According to Dr.Web Bot for Telegram data
- Android.Locker
- A family of ransomware Trojans for Android. They can lock a device after alleging via an on-screen warning that the device owner has done something illegal. To unlock the device, the owner has to pay a ransom.
- Android.Spy.337.origin
- A Trojan for Android that steals confidential information, including user passwords.
- Android.Hidden
- Android Trojans capable of hiding their shortcuts in the list of applications on an infected device.
- Program.TrackerFree.2.origin
- Detects Mobile Tracker Free, an application for tracking children.
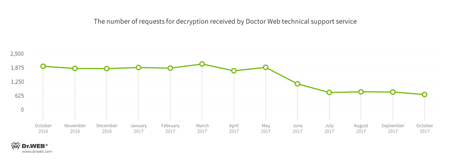
Encryption ransomware
In October, cases involving the following ransomware modifications were registered by Doctor Web’s technical support service:
- Trojan.Encoder.3953 — 17.26% of requests;
- Trojan.Encoder.858 — 16.67% of requests;
- Trojan.Encoder.13671 — 5.51% of requests;
- Trojan.Encoder.2667 — 4.02% of requests;
- Trojan.Encoder.567 — 2.38% of requests;
- Trojan.Encoder.3976 — 2.23% of requests.
Dr.Web Security Space for Windows protects against encryption ransomware
Dangerous websites
During October 2017, the URLs of 256,429 non-recommended websites were added to the Dr.Web database.
| September 2017 | October 2017 | Dynamics |
|---|---|---|
| + 298,324 | + 256,429 | -14.0% |
Linux malware
In October, Doctor Web virus analysts examined a Trojan capable of infecting “smart” Linux devices. The malicious program was dubbed Linux.IotReapper. It is yet another modification of the well-known Linux.Mirai. Instead of brute-forcing logins and passwords to hack devices, Linux.IotReapper launches exploits and checks the result of their execution. Then the Trojan waits for commands from its command and control (C&C) server. It downloads and launches various applications on an infected device. It also contains two modules: a Lua interpreter and a server operating on port 8888 that can also execute different commands. Dr.Web for Linux successfully detects Linux.IotReapper.
Other events in information security
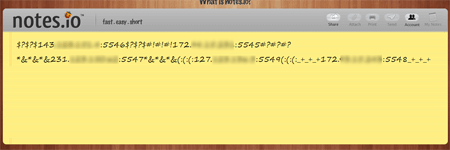
In the middle of the month, the signature of Python.BackDoor.33 was added to the Dr.Web virus databases. This Trojan is a backdoor written in Python. This malicious program can spread independently: after it has been installed on an infected device and restarted, Python.BackDoor.33 tries to infect all the device’s drives— from C to Z. Then the Trojan determines the IP address and available port of the C&C server by sending a request to several Internet servers, including pastebin.com, docs.google.com, and notes.io. The received value looks as follows:
Under certain circumstances, Python.BackDoor.33 downloads a Python script from the C&C server and launches it on the infected device. This script implements functions for stealing passwords (stealer), intercepting pressed keys (keylogger), and executing remote commands (backdoor). This script lets the Trojan execute the following actions on an infected machine:
- Steal information from such browsers as Chrome, Opera, Yandex, Amigo, Torch, and Spark;
- Perform keylogger functions and take screenshots;
- Download additional modules written in Python and execute them;
- Download files and save them on the media of the infected device;
- Obtain the contents of a specified folder;
- “Travel” across folders;
- Request system information.
More information about Python.BackDoor.33 can be found in an article published on our website.
Malicious and unwanted programs for mobile devices
In October, the mass media reported on the discovery of a dangerous ransomware Trojan that is detected as Android.Banker.184.origin by Dr.Web. This malicious program has been known to Doctor Web security researchers since August 2017. It changes the PIN code that unlocks the screen of infected Android smartphones or tablets, encrypts files, and demands a ransom to make devices operational again. In addition, in the past month, Android.SockBot.5 was detected on Google Play. It allows cybercriminals to use mobile devices as proxy servers.
The following October events related to mobile malware are the most noteworthy:
- The emergence of information related to the spread of a ransomware Trojan that changes the PIN code needed to unlock the screen of an Android device and encrypts files;
- The detection on Google Play of a ransomware Trojan that turned infected Android devices into proxy servers.
Find out more about malicious and unwanted programs for mobile devices in our special overview.