Doctor Web’s overview of malware detected on mobile devices in July 2017
July 31, 2017
In July, Doctor Web security researchers have detected a preinstalled Trojan on several Android smartphone models. Cybercriminals injected this Trojan to the system library. This malicious program infiltrated application processes and could covertly download and launch additional modules. In addition, a game with an embedded loader Trojan was detected on Google Play. Also in July, virus analysts examined a dangerous banking Trojan that gained control over an infected device and stole confidential information.
PRINCIPAL TRENDS IN JULY
- Detection of the Trojan in the firmware of several Android device modules. This Trojan infiltrated application processes and covertly launched malicious modules
- The detection of the loader Trojan on Google Play
- Detection of the dangerous banking Trojan
Mobile threat of the month
In July, Doctor Web security researchers detected Android.Triada.231. Cybercriminals injected it into an Android system library. This malicious program infiltrated application processes and could covertly download and launch additional modules. The Trojan was detected on several Android device modules at once.
Features of Android.Triada.231:
- Infiltration of the system library at the source code level;
- Infiltration of processes of all executable applications and their injection with malicious modules;
- To remove the Trojan from the device, installation of an original system image is required.
More information about this Trojan can be found in the corresponding review published by Doctor Web.
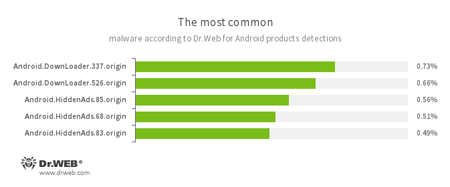
According to statistics collected by Dr.Web for Android
- Android.DownLoader.337.origin
- Android.DownLoader.526.origin
- Trojan programs designed to download other applications.
- Android.HiddenAds.85.origin
- Android.HiddenAds.68.origin
- Android.HiddenAds.83.origin
- Trojans designed to display unwanted ads on mobile devices. They are distributed under the guise of popular apps by other malicious programs that sometimes covertly install them in the system directory.
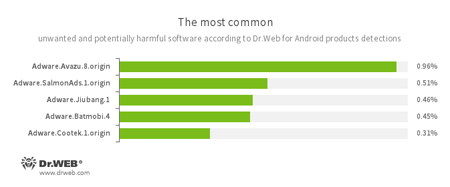
- Adware.Avazu.8.origin
- Adware.SalmonAds.1.origin
- Adware.Jiubang.1
- Adware.Batmobi.4
- Adware.Cootek.1.origin
- Unwanted program modules that are incorporated into Android applications and are designed to display annoying ads on mobile devices.
Trojan on Google Play
In July, Doctor Web specialists found Android.DownLoader.558.origin injected into a popular game called BlazBlue. This malicious program is included into the system module designed to optimize software update. Its danger is in capability to covertly download and launch unchecked application components. Additional information about Android.DownLoader.558.origin is in our news article.
Banking Trojan
During the last month, a new dangerous banking Trojan called Android.BankBot.211.origin was detected. It tried to gain access to the Android Accessibility Service. It could control infected devices and steal all data from the keyboard input, including passwords. Besides, Android.BankBot.211.origin displayed phishing input forms for confidential data over launched banking programs, payment service software and other applications. More detailed information about this Trojan’s operation could be found in the corresponding article on our website.
Cybercriminals still attack users of Android mobile devices. They constantly extend the functionality of Trojans and make efforts to distribute them in all possible ways. Doctor Web recommends that device owners install Dr.Web for Android to protect their smartphones and tablets from malicious applications.
Your Android needs protection
Use Dr.Web
- The first Russian Anti-virus for Android
- More than 100 million downloads on Google Play alone
- Free for users of Dr.Web home products