May 2017 mobile malware review from Doctor Web
May 31, 2017
Doctor Web presents its May 2017 overview of malware for mobile devices. In the past month, several new Trojans for Android were detected on Google Play. One of them downloaded applications from the Web and stole confidential information. Another downloaded and launched additional program modules and displayed annoying advertisements. Also in May, cybercriminals distributed a banking Trojan that stole money from user accounts.
Principal Trends in May
- The detection of Trojans on Google Play
- The distribution of a banking Trojan for Android
Mobile threat of the month
In early May, Android.RemoteCode.28 was detected on Google Play. It was embedded in an audio player. It downloaded other applications from the Internet and shared with the command and control server information about the infected device and data on the installed software.
Features of Android.RemoteCode.28:
- The main malicious functionality of the Trojan lies within its additional encrypted module;
- Android.RemoteCode.28 starts its malicious activity only 8 hours after its launch;
- The Trojan checks whether an emulator and debugging tools are present and shuts down if it detects them.
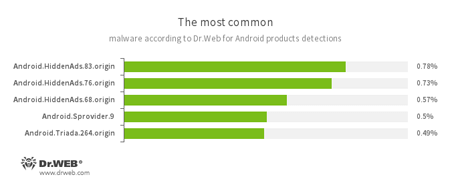
According to statistics collected by Dr.Web for Android
- Android.HiddenAds.83.origin
- Android.HiddenAds.76.origin
- Android.HiddenAds.68.origin
- Trojans designed to display unwanted ads on mobile devices. They are distributed under the guise of popular apps by other malicious programs that, in some instances, covertly install them in the system directory.
- Android.Sprovider.9
- A Trojan for Android that is designed to display advertisements in the status bar and download and install other applications including malicious ones.
- Android.Triada.264.origin
- A multi-component Trojan that performs different malicious functions.
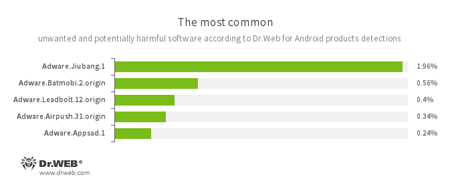
- Adware.Jiubang.1
- Adware.Batmobi.2.origin
- Adware.Leadbolt.12.origin
- Adware.Airpush.31.origin
- Adware.Appsad.1
- Unwanted program modules that are incorporated into Android applications and are designed to display annoying ads on mobile devices.
Trojan on Google Play
In mid-May, applications with the Trojan Android.Spy.308.origin embedded in them were detected on Google Play. In particular, they were being distributed by the developer Sumifi Dev. This is not the first time a malicious program has infiltrated the official software catalog for Android. Doctor Web described one such incident in July 2016. After detecting Android.Spy.308.origin, the developer updated the infected applications and deleted the Trojan component. They now pose no threat.
Android.Spy.308.origin displays annoying advertisements and stealthily downloads and runs additional program modules. In addition, the Trojan steals confidential information and sends it to the command and control server.
Banking Trojans
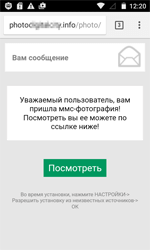
In May, cybercriminals employed MMS messages to distribute banking Trojans such as Android.BankBot.186.origin. Users received SMS messages containing a link leading to a scam webpage. From there, a malicious APK file was downloaded to mobile devices.
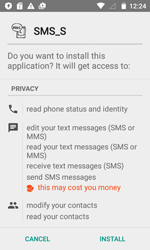
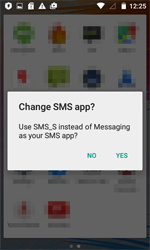
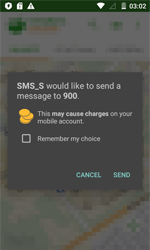
Android.BankBot.186.origin prompts the user to grant it administrative privileges in order to hinder its removal from the system. It also tries to take the place of the standard application for handling SMS. This is required in order to bypass the security system of new Android versions and to be able to send and intercept messages. After that, the Trojan checks bank account balances and covertly transfers money to cybercriminals.
Malicious programs for mobile Android devices still pose a threat. The Trojans can be spread via malicious websites as well as via the official application catalog Google Play. Doctor Web recommends that owners of smartphones and tablets install Dr.Web for Android to protect them from dangerous and unwanted software.