May 2017 virus activity review from Doctor Web
May 31, 2017
The most notable event of May 2017 was the mass distribution of the malicious program WannaCry, which is detected by Dr.Web Anti-virus as Trojan.Encoder.11432. This worm was distributed independently, infecting network nodes via an SMB protocol vulnerability. It then encrypted the files on the computers of its victims and demanded a ransom for their decryption. Moreover, in May, Doctor Web specialists examined a complicated multi-component Linux Trojan written in Lua. A new backdoor for macOS was also detected.
Principal Trends in May
- The distribution of the dangerous encryption ransomware WannaCry
- The detection of a new backdoor for macOS
- The appearance of a multi-component Trojan for Linux
Threat of the month
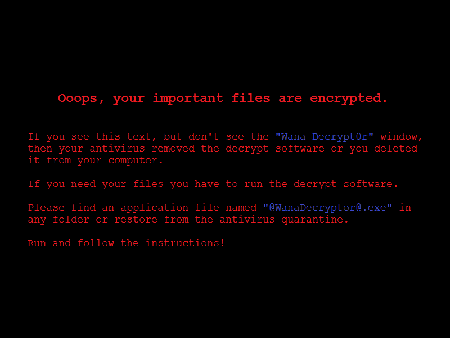
The malicious program widely known as WannaCry was covered by many media outlets. This dangerous application is a network worm that infects computers running Microsoft Windows. It started being spread around 10 a.m. on May 12, 2017. The worm contains an encryption Trojan as its payload. Dr.Web Anti-virus detects all the worm’s components as Trojan.Encoder.11432.
Once launched, the worm registers itself as a system service and starts querying network nodes in the local network and on the Internet that have random IP addresses. If a connection is successfully established, the worm attempts to infect these computers. If it manages to infect them, the worm launches an encryption Trojan, which uses a random key to encrypt the files on the computers. While in operation, Trojan.Encoder.11432 deletes shadow copies and disables the system restore function. The Trojan creates a separate list of files, which are encrypted with a different key: the malicious program can decrypt these files for its victim for free. As these test files and all the other files on the computer are encrypted with different keys, the computer’s owner has no guarantee that their files will be decrypted successfully even if they pay the ransom. Detailed information regarding this Trojan can be found in a review and in a detailed technical description of the worm.
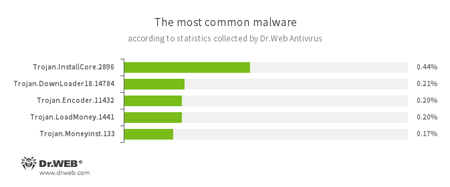
According to Dr.Web Anti-virus statistics
- Trojan.InstallCore
A family of installers of unwanted and malicious applications. - Trojan.DownLoader
A family of malicious programs designed to download other malware to the compromised computer. - Trojan.Encoder.11432
A network worm that launches a dangerous ransomware Trojan on a victim’s computer. It is also known as WannaCry. - Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on the victim's computer. - Trojan.Moneyinst.133
A malicious program that installs various software, including other Trojans, on a victim's computer.
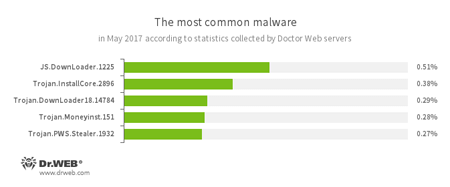
According to Doctor Web’s statistics servers
- JS.DownLoader
A family of malicious JavaScripts. Download and install malicious software. - Trojan.InstallCore
A family of installers of unwanted and malicious applications. - Trojan.DownLoader
A family of malicious programs designed to download other malware to the compromised computer. - Trojan.Moneyinst.151
A malicious program that installs various software, including other Trojans, on a victim's computer. - Trojan.PWS.Stealer
A family of Trojans designed to steal passwords and other confidential information stored on an infected computer.
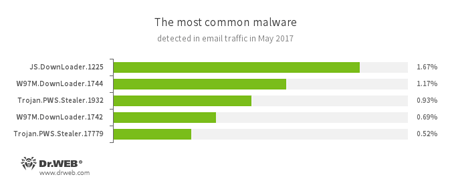
Statistics concerning malicious programs discovered in email traffic
- JS.DownLoader
A family of malicious JavaScripts. Download and install malicious software. - W97M.DownLoader
A family of downloader Trojans that exploit vulnerabilities in office applications. Designed for downloading other malware to a compromised computer. - Trojan.PWS.Stealer
A family of Trojans designed to steal passwords and other confidential information stored on an infected computer.
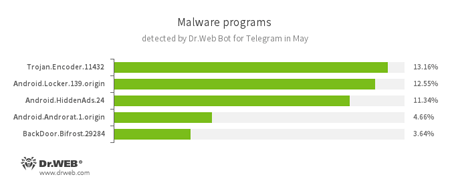
According to Dr.Web Bot for Telegram data
- Trojan.Encoder.11432
A network worm that launches a dangerous ransomware Trojan on a victim’s computer. It is also known as WannaCry. - Android.Locker.139.origin
A ransomware Trojan for Android. It can lock a device after alleging via an on-screen warning that the device owner has done something illegal. To unlock the device, the owner has to pay a ransom. - Android.HiddenAds.24
A Trojan designed to display unwanted ads on mobile devices. - Android.Androrat.1.origin
A spyware program for Android devices. - BackDoor.Bifrost.29284
A backdoor Trojan that executes commands received from cybercriminals.
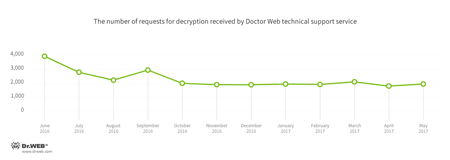
In May, Doctor Web’s technical support was most often contacted by victims of the following modifications of encryption ransomware:
- Trojan.Encoder.858 — 14.39% requests;
- Trojan.Encoder.11432 — 8.36% requests;
- Trojan.Encoder.3953 — 7.41% requests;
- Trojan.Encoder.761 — 2.62% requests;
- Trojan.Encoder.10144 — 2.60% requests;
- Trojan.Encoder.567 — 2.47% requests.
Dr.Web Security Space 11.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows.
| Data Loss Prevention | |
|---|---|
 |  |
During May 2017, Doctor Web added 1,129,277 URLs into the Dr.Web database of non-recommended sites.
| April 2017 | May 2017 | Dynamics |
|---|---|---|
| + 568,903 | + 1,129,277 | + 98.5% |
Other information security events
At the beginning of May, Doctor Web detected a Trojan that was being distributed via links in comments left by cybercriminals on the official “Doctor Web” group page of the “VK” social network. In their messages, the crooks offered users the opportunity to download free license keys for the Dr.Web anti-virus; however, anyone who followed the link would actually end up downloading Trojan.MulDrop7.26387 onto their computer.
This malicious program can execute various commands issued by cybercriminals: for example, it can change the Windows Desktop wallpaper, open and close the optical disk drive, swap the functions of mouse keys, play a specific phrase using a voice synthesizer and speakers, and even display frightening videos. For more information, refer to this article published on our website.
Linux malware
In May, Doctor Web specialists examined a multi-component Linux Trojan written in Lua. This malicious program, which was dubbed Linux.LuaBot, consists of 31 Lua scripts and can infect not only computers but also other “smart” devices: network storages, routers, set-top boxes, IP cameras, etc. The Trojan generates a list of IP addresses to attack and then attempts to establish a connection with remote devices via this list and sign in by brute-force login using a special vocabulary. If successful, it downloads its own copy on the infected computer and launches it.
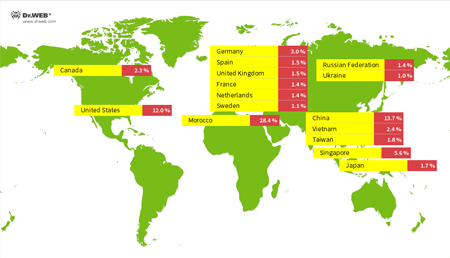
This Trojan is in fact a backdoor; in other words it executes commands issued by cybercriminals. In addition, this Trojan launches a web server on the infected device. This server allows cybercriminals to load different files. Doctor Web’s specialists have collected statistics on the unique IP addresses of devices infected with Linux. LuaBot—they are shown in the following diagram.
For more detailed information on this multi-component Trojan, refer to our news article or the technical description of the threat.
Malicious programs for macOS
The last spring month of 2017 was marked by the distribution of a backdoor for macOS. The Trojan has been added to the Dr.Web virus databases under the name Mac.BackDoor.Systemd.1. The backdoor can execute the following commands:
- Receive a list of the contents of a specified directory;
- Read a file;
- Write to a file;
- Get the contents of a file;
- Delete a file or folder;
- Rename a file or folder;
- Change the privileges for a file or folder (chmod command);
- Change the owner of a file object (chown command);
- Create a folder;
- Execute a command in the bash shell;
- Update the Trojan;
- Reinstall the Trojan;
- Change the command and control server’s IP address;
- Install a plug-in.
More information about this malicious program can be found in an article published by Doctor Web.
Malicious and unwanted programs for mobile devices
In May, Android.RemoteCode.28 was detected on Google Play. It downloaded other programs and shared information with the command and control server. Applications that conceal Android.Spy.308.origin were also detected in the catalog. This Trojan downloaded and ran additional program modules and displayed ads. This past month, cybercriminals distributed Android.BankBot.186.origin as MMS messages. This banking Trojan stole money from user accounts.
Among the most notable May events related to mobile malware, we can mention the following:
- The detection of Android Trojans on Google Play;
- The distribution of a banking Trojan that stealthily stole money from users and transferred it to cybercriminals.
Find out more about malicious and unwanted programs for mobile devices in our special overview.