Doctor Web’s October 2016 virus activity review
October 27, 2016
In October, Doctor Web’s specialists investigated the first ransomware Trojan written in Go and developed a technique for decrypting files compromised by this Trojan. Soon thereafter, they discovered a backdoor for Linux that was capable of executing commands received from cybercriminals. In addition, Trojans for Android devices continued to spread all month long.
PRINCIPAL TRENDS IN OCTOBER
- The emergence of a ransomware Trojan written in Go
- New malicious programs for Linux
- New malicious programs for Android
Threat of the month
Ransomware Trojans are rightfully considered the most dangerous malicious programs. New versions of these programs appear on a monthly basis; however, until recently Doctor Web’s specialists had never encountered ransomware programs written in Go. The first Trojan of this kind, named Trojan.Encoder.6491, was added to the Dr.Web virus databases in October.
The Trojan uses the AES algorithm to encrypt 140 different types of files. Trojan.Encoder.6491 encrypts original file names with the Base64 method and appends the .enc extension to the files it compromises. For example, the file name Test_file.avi is changed to VGVzdF9maWxlLmF2aQ==.enc. Then, in a browser window, the Trojan opens the file Instructions.html, which orders the user to pay a ransom in Bitcoin cryptocurrency:
Trojan.Encoder.6491 regularly checks the Bitcoin wallet to which the victim is to transfer the ransom amount. Once payment is made, the Trojan uses an internal function to automatically decrypt the files. Doctor Web’s security researchers have developed a new technique that can help decrypt files compromised by this malware. You can read about this technique in the news article published by Doctor Web.
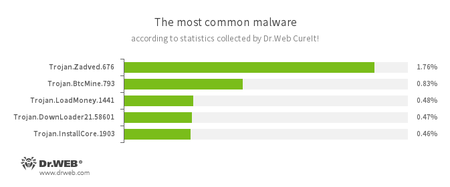
According to statistics collected by Dr.Web CureIt!
- Trojan.Zadved
This Trojan displays fake search results in the browser window and imitates pop-up messages from social networking sites. In addition, the malware can replace advertisements displayed on different Internet resources. - Trojan.BtcMine.793
A Trojan designed to covertly use an infected computer’s resources to generate cryptocurrency—for example, Bitcoin. - Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on a victim’s computer. - Trojan.DownLoader
A family of malicious programs designed to download other malware to a compromised computer. - Trojan.InstallCore.1903
A Trojan that can install unwanted and malicious applications.
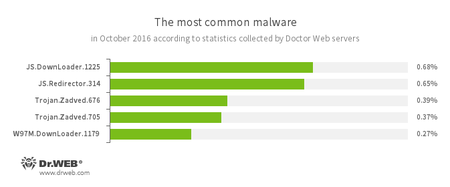
According to Doctor Web’s statistics servers
- JS.Downloader
A family of malicious scripts written in JavaScript and designed to download and install other malware programs on a computer. - JS.Redirector
A family of malicious scripts written in JavaScript and designed to automatically redirect users to other webpages. - Trojan.Zadved
This Trojan displays fake search results in a browser window and imitates pop-up messages from social networking sites. In addition, the malware can replace advertisements displayed on different Internet resources. - W97M.DownLoader
A family of downloader Trojans that exploit vulnerabilities in office applications and can download other malicious programs to a compromised computer.
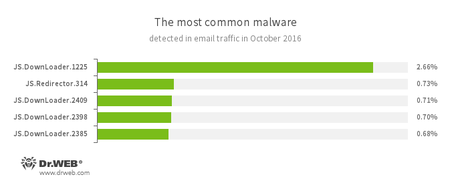
Statistics concerning malicious programs discovered in email traffic
- JS.Downloader
A family of malicious scripts written in JavaScript and designed to download and install other malware programs on a computer. - JS.Redirector
A family of malicious scripts written in JavaScript and designed to automatically redirect users to other webpages.
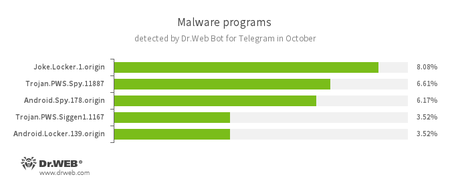
According to statistics collected by Dr.Web Bot for Telegram
- Joke.Locker.1.origin
A joke program for Android that locks the home screen of a device and displays a Microsoft Windows BSOD (Blue Screen of Death) error. - Trojan.PWS.Spy.11887
A Trojan for Windows that steals private information including user passwords. - Android.Spy
A family of multifunctional Trojans for Android that are designed to read and save contacts, receive and send SMS messages, determine GPS coordinates, read and save bookmarks in a browser, and get a device’s IMEI and telephone number. - Trojan.PWS.Siggen1.1167
A Trojan for Windows that steals user passwords. - Android.Locker.139.origin
A ransomware Trojan for Android. Its different modifications can lock a device after displaying a warning to the device’s owner that they have done something illegal. To unlock the device, the owner has to pay a ransom.
Encryption ransomware
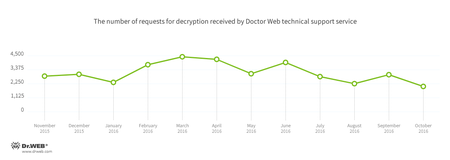
In October, cases involving the following ransomware modifications were registered by Doctor Web’s technical support service:
- Trojan.Encoder.858 — 26.85% of requests
- Trojan.Encoder.761 — 21.01% of requests
- Trojan.Encoder.3953 — 5.25% of requests
- Trojan.Encoder.567 — 4.61% of requests
- Trojan.Encoder.3976 — 2.92% of requests
Dr.Web Security Space 11.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows.
| Data Loss Prevention | |
|---|---|
 |  |
Dangerous websites
During October 2016, the URLs of 338,670 non-recommended websites were added to the Dr.Web database.
| September 2016 | October 2016 | Dynamics |
|---|---|---|
| +298,985 | +338,670 | +13.27% |
Among the non-recommended websites that were added to the database are fraudulent web resources. Fraudsters continue contriving new ways of tricking Internet users—one of them is described in our overview.
The creators of the fraudulent website “Detector Millionaire” use mass spam mailings to get gullible users to test their program “Detector Millionaire.” This scam has reportedly already benefited the program’s creators to the tune of several million dollars. To start using it, a potential victim has to transfer a certain sum of money to the cybercriminals’ account. Obviously, all the money deposited is irrevocably gone. In addition, a simple search of the domain registration database reveals that detektor-millionera.com is administrated by one Bob Douglas, who owns many other suspicious web resources.
Find out more about Dr. Web non-recommended sites
Linux
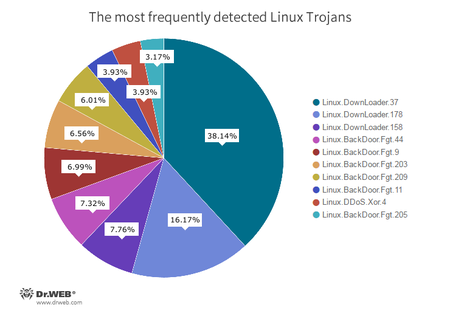
Since the beginning of October, Doctor Web’s specialists have registered 40,756 attacks by Linux Trojans—35,423 of them were performed over the SSH protocol and 5,333 of them over the Telnet protocol. The below diagram shows the proportional relationship between the most frequently detected Linux Trojans:
- Linux.Downloader
A family of malicious programs and scripts for Linux designed to download and install other malware applications on an infected computer. - Linux.BackDoor.Fgt
A family of Trojans for Linux designed to carry out DDoS attacks. Numerous versions of Trojans exist for different Linux distributions, including for the MIPS and SPARC architectures. - Linux.DDoS.Xor
A family of Trojans for Linux designed to perform DDoS attacks on various network nodes.
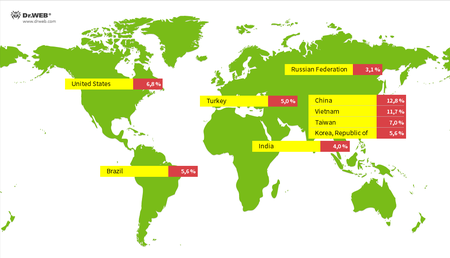
Below you can see the geographical spread of the IP addresses from which malware programs were installed onto Linux devices:
The end of October was marked by the emergence of Linux.BackDoor.FakeFile.1, a backdoor Trojan for Linux spread as a PDF, Microsoft Office, or Open Office file. This Trojan could:
- Send the C&C server the quantity of messages transferred during a session;
- Send a list of the contents of a specified folder;
- Send the C&C server a specified file or folder together with all the contents;
- Delete a directory;
- Delete a file;
- Rename a folder;
- Remove itself;
- Launch a new copy of a process;
- Close the current session;
- Establish backconnect and run sh;
- Terminate backconnect;
- Open the executable file for a writing process;
- Close the process file;
- Create a file or folder;
- Write the transmitted values to a file;
- Obtain the names, permissions, sizes, and creation dates of files in a specified directory;
- Set 777 privileges on a specified file;
- Terminate the backdoor’s operation.
For more information about Linux.BackDoor.FakeFile.1, refer to the news article published by Doctor Web.
Malicious and unwanted programs for mobile devices
October began with the appearance of Android.SockBot.1, a Trojan that can redirect Internet traffic through infected mobile devices, transforming them into proxy servers.
The following October events related to mobile malware are the most noteworthy:
- The discovery of a new Trojan on Google Play—Android.SockBot.1—which can transform mobile devices into proxy servers.
Find out more about malicious and unwanted programs for mobile devices in our special overview.