June 2016 mobile malware review from Doctor Web
June 30, 2016
In June, Doctor Web security researchers detected several malicious applications on Google Play store. One of them was designed to steal login credentials for VK user profiles; and the other—to load suspicious websites as advertising banners in order to get users’ mobile phone number and subscribe them to chargeable services.
PRINCIPAL TRENDS IN JUNE
- Detection of a Trojan that steals logins and passwords from VK user profiles
- Detection of a Trojan that opens suspicious websites as advertisements on Google Play
Mobile threat of the month
Although Google Play is still considered to be the most secure Android app store, from time to time, attackers try to spoil its reputation by spreading their malicious programs via this catalog. This month, Doctor Web specialists detected a group of Android applications that were found to contain Android.Valeriy.1.origin. This Trojan is able to redirect to dubious websites and display them as advertisements in order to get their mobile phone number and subscribe them to chargeable services. Then a certain subscription fee is written off from the user’s mobile account every day. At that, Android.Valeriy.1.origin intercepted all SMS messages informing the user about the subscription. The Trojan can also download malicious programs and execute JavaScript scripts.
More information about Android.Valeriy.1.origin can be found in the corresponding review published by Doctor Web.
According to statistics collected by Dr.Web for Android
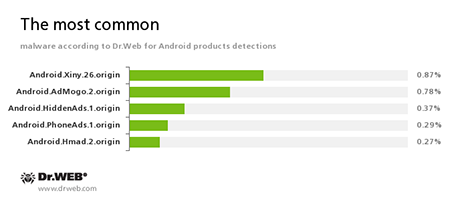
Android.Xiny.26.origin
A Trojan that gets root privileges, copies itself into the system registry, and then is able to install various applications without user knowledge. In addition, it displays annoying advertisements.Android.AdMogo.2.origin
A Trojan designed to deliver advertisements. It is installed to Android system catalog by other malicious applications.Android.HiddenAds.1.origin
A Trojan designed to display advertisements. It is distributed under the guise of popular apps by other malicious programs that are covertly installed into the system directory.Android.PhoneAds.1.origin
A Trojan that delivers annoying advertisements.Android.Hmad.2.origin
A Trojan that delivers annoying advertisements and installs unwanted applications.
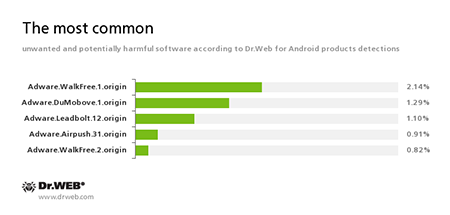
Adware.WalkFree.1.origin
Adware.DuMobove.1.origin
Adware.Leadbolt.12.origin
Adware.Airpush.31.origin
Adware.WalkFree.2.origin
An unwanted program module that is incorporated into the Android applications and is responsible for advertising on mobile devices.
Trojans on Google Play
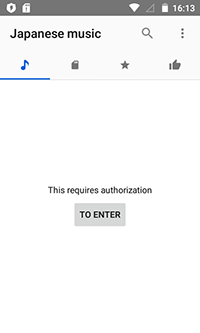
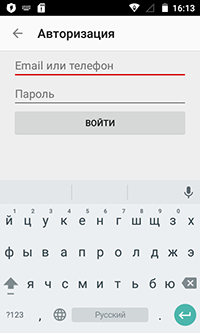
Apart from Android.Valeriy.1.origin, another Trojan was found in Google Play—Android.PWS.Vk.3. This Trojan was represented as a media player for VK music. It prompted the user to enter their login and password for the VK user account and then covertly sent this private information to cybercriminals.
For more information about Android.PWS.Vk.3, refer to the news article published by Doctor Web.
Doctor Web strongly advises users to install only official applications and protect their devices with anti-virus software.