Over one million PCs compromised by Win32.Sector file infector
Real-time threat news | Hot news | All the news | Virus alerts
May 21, 2014
Known to analysts since 2008, Win32.Sector is a complex polymorphic malicious program that can spread on its own (without user intervention) and infect files. Its main function is to download various executables via P2P networks and run them on infected machines. This malicious program can inject its code into running processes, terminate certain anti-viruses and block access to the sites of their respective developers. Win32.Sector can infect files on local and removable disks (in the latter case, it can create the file autorun.inf on removable media) as well as in shared network folders. At present, there are several Win32.Sector modifications, each with a different P2P network communication protocol and different structural features.
By design, Win32.Sector has no control servers; instead it connects with other bots running on infected machines. It determines whether the computer has an external IP address or connects to a network that uses NAT. When launched on an infected computer, Win32.Sector uses an initial list of IP addresses to connect to other bots. If successful, the file infector executes the following commands:
- Use a download link to request a configuration file via UDP.
- Request plugins (via TCP).
- Check for NAT; if unavailable, the bot receives a unique identification number ID (via UDP).
- Obtain the IP address of another infected machine to establish a connection (via UDP).
The third command makes the program operate as a router to which other bots (those operating in networks that use NAT and, therefore, have no external IP addresses of their own) connect. The fourth directive enables the file infector to acquire lists of IP addresses from other bots. Doctor Web's security researchers used these two commands to determine the number of infected hosts connected to the botnet and to assess the scale of the infection.
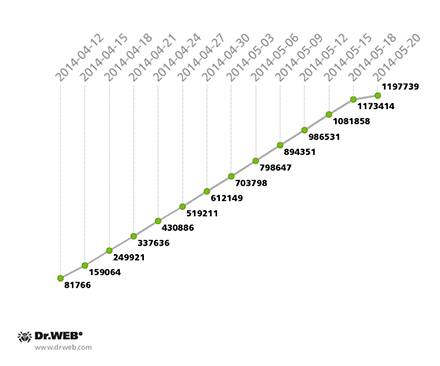
As of May 20, 2014, the Win32.Sector botnet was comprised of 1,197,739 unique bots, 109,783 of which had external IP addresses and could operate routers for other infected hosts. The growth of the botnet can be traced in the graph below:
On average, about 60,000 infected computers interacted over the botnet on a daily basis. A Win32.Sector botnet activity graph is presented below:
Average daily activity in the Win32.Sector botnet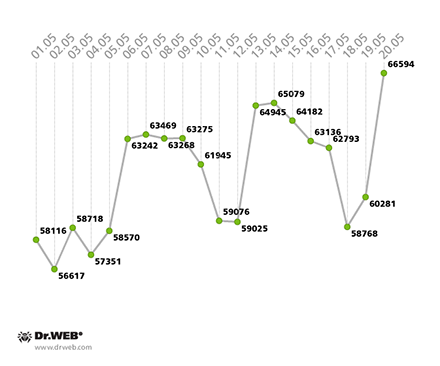
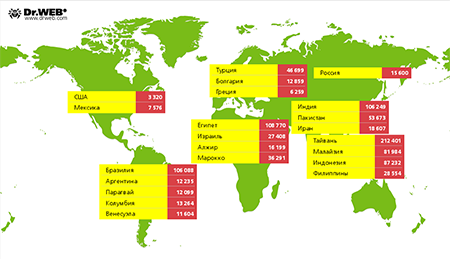
From a geographical standpoint, the largest number of hosts infected with Win32.Sector are found in —212,401. ranked second (108,770), and ranked third (106,249). In , 15,600 infected computers were identified. Win32.Sector’s geographical spread by country is shown in the illustration below:
Currently several malicious programs are being spread via the Win32.Sector botnet:
- Trojan.PWS.Stealer.1630which steals passwords and other confidential information;
- Trojan.Mssmsgs.4048 — a spam plugin;
- Trojan.DownLoader8.17844 which operates as an http and socks5 proxy;
- Trojan.DownLoader10.49375 which operates as an http and socks5 proxy;
- Trojan.Siggen6.11882 which establishes DNS tunnels (53 udp port) and TCP tunnels (port 80);
- Trojan.Rbrute which gains access to Wi-Fi routers;
- Trojan.Proxy.26841 which establishes a tunnel to transmit http traffic to specified nodes.
All of these threats, including Win32.Sector, are successfully detected and removed by the Dr.Web antivirus, so they pose no threat to computers protected by Doctor Web's software. The company's security researchers will continue to monitor further developments.