Win32.Rmnet.16 attacks UK and Australia
Real-time threat news | All the news | Virus alerts
May 14, 2012
Win32.Rmnet.16 is written in C and Assembly and consists of several functional modules. The injector that deploys the virus in the system works in exactly the same way as that of Win32.Rmnet.12: it injects its code into browser processes, saves its driver into a temporary folder and runs it as a Micorsoft Windows Service, then copies the virus body into a temporary directory and startup folder. The body file has a random name and the extension. exe.
The backdoor payload is also similar to that of Win32.Rmnet.12. This component can execute commands received from a remote server, in particular, to download and run arbitrary files, update itself, to take screenshots and send them to criminals, and even render the operating system non-operational. However, there are also important differences: Win32.Rmnet.16 uses a digital signature to sign control server IP-addresses which are no longer embedded in the malicious application resources but generated using a special routine. In addition, the module can end processes of the majority of popular anti-virus programs, which makes the malware even more dangerous. Malicious components and configuration files downloaded by the backdoor are stored in an encrypted file with the extension .log while the file name is generated using information about the compromised system. This file is located in the folder% APPDATA%. The module implemented in the modules.dll file loads data from the file with the extension. log and performs all the manipulations with the loaded code in the computer's memory, so the components' code is not decrypted onto the hard drive.
Like its predecessor, Win32.Rmnet.16 can modify the MBR and encrypt and save its files at the end of the disk. After rebooting, control is transferred to malicious code in the infected boot record, which reads and decrypts modules in the memory and then runs them. This component of the malicious program is dubbed MBR.Rmnet.1. It should be noted that the Dr.Web anti-virus software can restore a boot record, modified by Win32.Rmnet.
Modules downloaded by Win32.Rmnet.16 from remote command centers also include Ftp Grabber v2.0, designed to steal passwords stored by popular FTP-clients, its own FTP-server and a spy module.
The Infection module incorporated into the new version is polymorphic. It is downloaded from a remote site maintained by intruders. The virus infects all exe and dll files found on the disks, including system ones, but, unlike Win32.Rmnet.12, can not copy itself to removable flash drives.
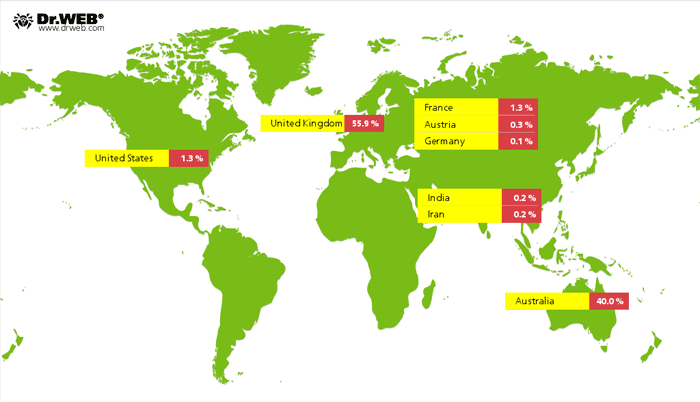
Doctor Web virus analysts closely monitor operation of one of the Win32.Rmnet.16 botnets. As of May 11, 2012, this botnet included 55,310 infected hosts and 55.9% of compromised machines are located in the UK. Australia comes second with 40% , the United States and France divide the third place (1.3%) , less than 1% of infected computers are located in Austria, Iran, India and Germany. London accounts for the greatest number of Win32.Rmnet.16 infection incidents (5747 infected PCs, or 10.4%), Sydney ranks second (3120 computers, or 5.6%), followed by Melbourne (2670 cases of infection, or 4.8%), Brisbane (2323 PCs, or 4.2%), Perth (1481 PCs, or 2.7%) and Adelaide (1176 PC, or 2.1%). Around 1.5 of infected hosts are found in Birmingham and Manchester in Britain. The figure below shows distribution of hosts infected by Win32.Rmnet.16 across the world.
The spread of the botnet Win32.Rmnet.16 by country
In Russia the cases of infection by Win32.Rmnet.16 still are rare, but over time this may change. Doctor Web continues to closely monitor activity of the botnet.