Phishing emails with RAT malware threaten corporate users
Real-time threat news | Hot news | All the news | Virus alerts
December 11, 2020
The samples can be divided into two groups:
- Self-extracting archives that contained the original Remote Utilities executable files and a malicious module loaded via DLL Hijacking. This module prevents the operating system from displaying the program’s windows and other signs of operation. Dr.Web detects it as BackDoor.RMS.180.
- Self-extracting archives that contained the original Remote Utilities installation module and a pre-configured MSI package that silently installs the remote access software and then sends a notification that it’s ready to be remotely connected to the server the attacker specified. Dr.Web detects it as BackDoor.RMS.181.
Attack scenario
Both groups of malware are united by the Remote Utilities software used and the layout of the phishing emails. These emails can be described as relatively well-written and lengthy Russian messages designed to entice recipients to open and read about various topics of interest. Also noteworthy, is that malicious payload is password protected, while the password itself is attached to the same email as the text file. The password is the date when the email was sent.
Here’s an example of an email with a malicious attachment that uses DLL Hijacking.
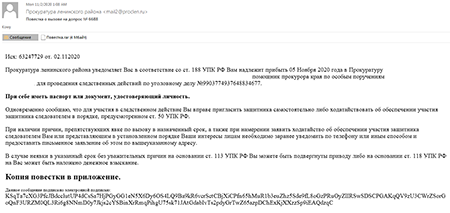
This email is disguised as an official notification requesting the recipient appear at the Prosecutor's office for investigative actions in a criminal case. It has a fake digital signature, which is just a random string in Base64.
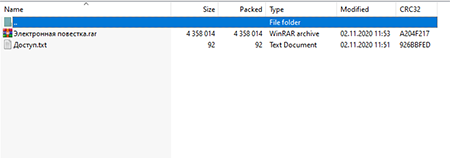
The attached archive contains a protected RAR archive and a text file with a password to it.
An automatic password is set to protect the privacy of this attachment: 02112020
The archive named “Электронная повестка.гаг" contains the dropper as a self-extracting RAR archive, which in turn contains BackDoor.RMS.180.
Below is an example of an email with an attachment that uses the MSI package.
This email, disguised as a notification from a transport company regarding cargo arrival, asks the recipient to specify the shipping address. This email also contains a fake digital signature.
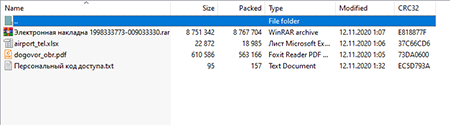
“Документы.гаг” contains dummy documents in addition to an archive with the malicious payload (BackDoor.RMS.181) and a password.
Due to corporate security policy, this attachment is protected with an access code: 12112020
During our research, we also uncovered a sample phishing email containing a link to a dropper that launched the Remote Utilities installation from a configured MSI package (detected by Dr. Web as BackDoor.RMS.187). This email implements a different malicious module with another infection method.
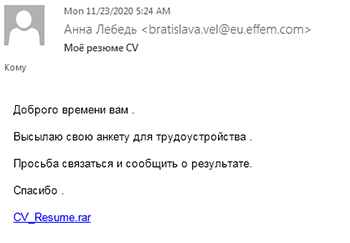
This email is disguised as a message from a job seeker with an attached CV. The "CV_resume.rar” attachment is a link to a compromised website that redirects the user to another resource to download a malicious archive with BackDoor.RMS.187.
Analyzing the network infrastructure attackers used to distribute BackDoor.RMS.187 allowed us to unearth several more compromised websites and a sample of the Trojan.Gidra malware. According to our data, the program Dr.Web detected as Trojan.GidraNET.1 was used to initially penetrate the system through a phishing email with further capabilities to upload a backdoor that silently installs the Remote Utilities software on a compromised computer.
For a detailed description of the malware used and how it works, see the Dr.Web Virus Library.
BackDoor.RMS.180
BackDoor.RMS.181
BackDoor.RMS.187
Trojan.GidraNET.1
Conclusion
The backdoors based on the remote desktop software remain a threat and are still widely used in corporate sector cyberattacks. In turn, phishing emails are the most common way to deliver payloads to targeted computers. Payload archiving using a password is a distinctive feature of malicious attachments. This allows messages to overcome mail servers’ built-in security tools. Another marker is the presence of a text file with a password to the bogus archive. In addition, using a malicious library and DLL Hijacking attack ensures unauthorized remote access software runs silently.