Banking Trojan discovered in hacked Android games
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
May 26, 2016
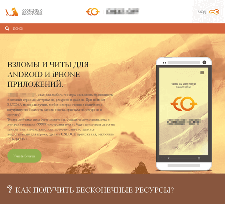
This time, attackers focused their attention on those who prefer to play hacked games, which makes a gameplay easier and faster. To successfully distribute the Trojan, virus makers monitor whether the potential victim surfs the Web in order to find cheat codes for the game to simplify its walkthrough (for example, infinite gold, crystals, and so on) or they would like to download a hacked version of the favorite game. Thus, among the search results, the user sees links that lead to various fraudulent websites specially designed to trick naive gamers.
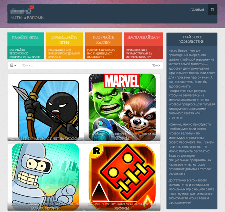
These websites can inform users about more than 1,000 different mobile games—thus, the search engine displays fraudulent links on top of the search results. It is noteworthy that all these resources have valid digital signatures, which makes them seem quite legitimate.
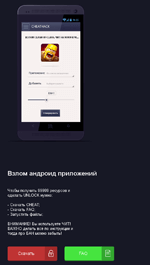
When the user tries to download a game from this site, they are redirected to another scam webpage that is used to spread Android.BankBot.104.origin under the guise of a hacked game or a game cheating software. In addition to this banking Trojan, the webpage can distribute other threats belonging to the Android.ZBot family.
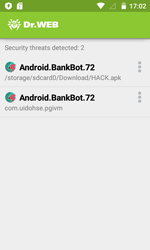
Android.BankBot.104.origin is protected with a special packer that complicates an anti-virus detection of the Trojan and its analysis. One of its last modifications was named Android.BankBot.72; yet, given that attackers always create new repacked versions of the Trojan, this malware can be detected under different names. Android.BankBot.104.origin is an obfuscated version of Android.BankBot.80.origin, which means that its code is securely encrypted.
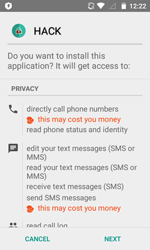
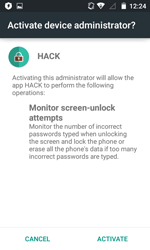
Android.BankBot.104.origin is installed on a mobile device as an application named “HACK”. Once launched, the Trojan tries to get administrator privileges and then removes its shortcut from the home screen.
After that, the Trojan determines whether there is an online banking application installed on the device, and how much funds are available on the user’s bank accounts. To do that, Android.BankBot.104.origin sends special SMS commands to banking systems numbers. If successful, the Trojan attempts to covertly transfer money from the victim’s bank accounts to cybercriminals’.
Moreover, attackers control the Trojan from the remote server. Thus, this malware can enable forwarding to the specified number, hide and intercept SMS messages, send text messages and USSD requests, and perform other malicious actions.
Doctor Web specialists strongly recommend to avoid visiting such-like dubious resources and downloading hacked mobile games and applications if you do not want to lose all the money from your bank accounts. Dr.Web for Android successfully detects all the known modifications of this Trojan, and, therefore, this malicious program poses no threat to our users.