Banking Trojan infected dozens of Android apps worldwide
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
May 12, 2016
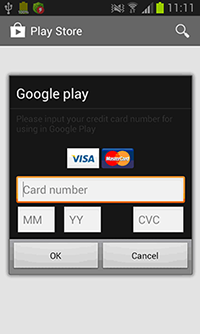
Early versions of Android.SmsSpy.88.origin discovered in April 2014 had a quite primitive architecture. Initially, the Trojan was designed to intercept SMS messages containing one-use bank passwords, to covertly send text messages, and to make phone calls. Some time later, virus makers modified Android.SmsSpy.88.origin by adding the ability to steal credit card information. In particular, if the user launched Google Play or online banking applications developed by several well-known Russian banks, the Trojan displayed a fraudulent input form on top of the running application. The information about the bank card entered by user was immediately sent to cybercriminals.
It is noteworthy that all first versions of the Trojan attacked users only in Russia and CIS countries. At that time, it was spread via spam SMS messages that offered the victim to follow the given link and get familiar with the reply to the announcement posted on the Web. In fact, all those links redirected the user to scam websites that distributed the malicious application under the guise of a benign program.
Later, the number of attacks considerably reduced. Yet, at the end of 2015, Doctor Web security researchers registered the emergence of new and more sophisticated versions of Android.SmsSpy.88.origin designed to infect Android devices all over the world.
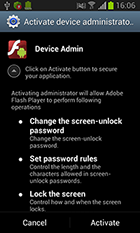
This Trojan still masquerades as benign programs—for example, Adobe Flash Player. Once launched, Android.SmsSpy.88.origin prompts the user to grant it administrator privileges in order to stay on the device as long as possible.
The Trojan establishes Internet connection and keeps it active by using Wi-Fi or a transmission channel of mobile network operator. Therefore, the Trojan is continuously connected to the C&C server and prevents possible malfunctions. The malware then generates a unique identifier for the infected device. The identifier and other technical details are sent to the server, where the infected device is registered.
The main purpose of Android.SmsSpy.88.origin was still to steal login credentials from online banking programs and send them to cybercriminals, which helped it to covertly steal money from the victim’s bank accounts. To do that, the Trojan checked whether the banking application specified in the Trojan’s configuration file is running. The number of applications the Trojan monitors can be different, but Doctor Web specialists have already found about 100 of such applications.
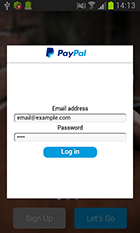
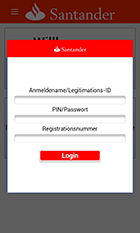
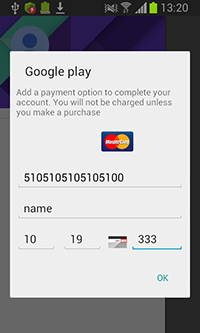
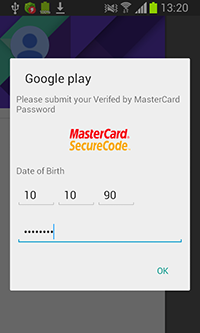
Once one of the specified applications is launched, Android.SmsSpy.88.origin uses WebView to display a phishing input form to access user account of online banking programs. If the user provides necessary information, it is sent to the server, and virus makers gain full control over the victim’s bank accounts.
One of the malware’s key features lies in the fact that it can attack clients of almost any bank in the world. Thus, cybercriminals create a new template of a fraudulent authentication form and command the Trojan to update its configuration file. Once updated, the file will contain the name of the necessary banking application.
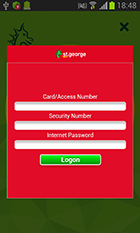
Apart from stealing logins and passwords for user accounts, the Trojan still tries to get information on the user’s bank card information. Android.SmsSpy.88.origin monitors the launch of some system programs and popular applications. When the Trojan detects that one of them is running, it immediately displays a phishing form of Google Play payment service settings.
However, the Trojan is able to perform other malicious functions: to intercept and send SMS and MMS messages, to send USSD requests, to send SMS messages to all contacts from the contact list, to transmit all saved messages to the server, to set a password to the lock screen, and to lock the home screen by using a specially-formed dialog. If the command is to lock the home screen, the Trojan displays a template of a fake dialog that informs the user that they illegally store and distribute pornography and have to pay for the iTunes Gift Card if they want to unlock the device.
Thus, Android.SmsSpy.88.origin acts not only as a banking Trojan and a spyware program but also as a ransomware Trojan, allowing attackers to make more money on gullible users.
In addition, Android.SmsSpy.88.origin has a self-protection function because it tries to hinder the work of some anti-virus programs and service utilities, preventing them from launching.
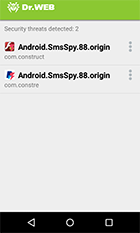
At the beginning of 2016, Doctor Web security researchers accessed to more than 50 botnets that consisted of mobile devices infected with different versions of Android.SmsSpy.88.origin. Our analytics registered that the Trojan affected users of more than 200 countries and at least 40,000 mobile devices.
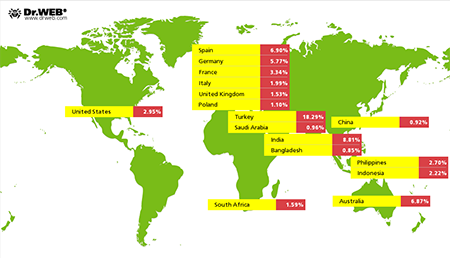
Users in the following countries suffered most of all: Turkey (18,29%), India (8,81%), Spain (6,90%), Australia (6,87%), Germany (5,77%), France (3,34%), the USA (2,95%), the Philippines (2,70%), Indonesia (2,22%), Italy (1,99%), South Africa (1,59%), Great Britain (1,53%), Pakistan (1,51%), Poland (1,1%), Iran (0,98%), Saudi Arabia (0,96%), China (0,92%), and Bangladesh (0,85%).
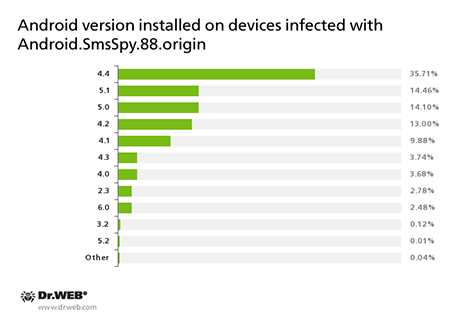
At that, the majority of infected mobile devices were running Android 4.4 (35,71%), 5.1 (14,46%), 5.0 (14,10%), 4.2 (13,00%), and 4.1 (9,88%).
The reason why Android.SmsSpy.88.origin is so widely distributed lies in the fact that its creators advertise the program on different underground forums and sell it as a commercial product. Apart from the Trojan itself, those who buy the Trojan also get the server part together with an administration panel that allows them to manage infected devices.
To protect your smartphone or tablet from such-like banking Trojans, Doctor Web recommends you to follow the guidance below:
- Use another mobile device for making online bank transactions if possible.
- Set a limit on cash withdrawal from your bank account via online banking services.
- Do not follow links received in dubious SMS messages.
- Do not download applications from unreliable resources.
- Protect your device with anti-virus software.
Dr.Web for Android successfully detects all the known applications containing Android.SmsSpy.88.origin, so they do not pose any threat to our users.