March 31, 2016
The majority of applications that are used to distribute Android.Spy.277.origin are bogus versions of various popular software. Attackers borrowed names and appearances of legitimate programs in order to attract users and, thus, increase downloads of the Trojan. In particular, among these fake apps, Doctor Web specialists found different utilities, photo editing and animated wallpaper apps, graphical shells, and other programs. At that, most of them do not possess the ability to perform the mentioned task. In total, Doctor Web security researchers registered more than 100 applications infected by Android.Spy.277.origin, and the number of downloads exceeded 3,200,000. Doctor Web has already informed Google about this incident. Therefore, some of these malicious programs are not available on Google Play anymore.
Once one of the above-mentioned malicious applications is launched, the Trojan transmits the following information on the device to the server:
- Email address connected to a Google user account
- IMEI identifier
- OS version
- SDK system version
- Device model
- Screen resolution
- Google Cloud Messaging identifier (GCM id)
- Cell phone number
- User’s geolocation
- CPU type
- MAC address of the power adapter
- the “user_agent” parameter generated using a special algorithm
- Mobile network operator
- Network connection type
- Network subtype
- Availability of root access
- Whether an infected application has administrator privileges
- Name of an infected application
- Presence of a Google Play application on the device
At every launch of any installed application, the Trojan resends all the information mentioned before together with the name of the running application. In addition, it requests parameters necessary for advertising. Android.Spy.277.origin can execute the following commands:
- “show_log”—enable or disable logging;
- “install_plugin”—install a plug-in hidden inside the malicious application;
- “banner”, “interstitial”, “video_ads”—display different types of advertisements (including, on top of the OS interface and other applications);
- “notification”—display a notification with the received parameters;
- “list_shortcut”—create shortcuts with received parameters on the home screen (tapping these shortcuts leads to opening of specified sections in Google Play);
- “redirect_gp”—open a webpage with a specified address in Google Play;
- “redirect_browse”—open a specified webpage in a preinstalled browser;
- “redirect_chrome”—open a specified webpage in Chrome;
- “redirect_fb”—open a Facebook webpage specified by the command.
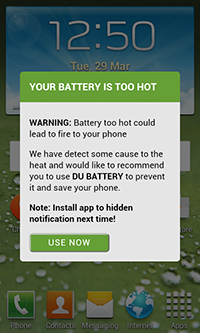
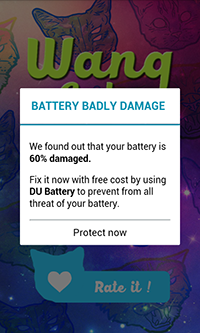
As you can see below, the Trojan can intimidate the user, for example, by allegedly claiming that the device’s battery is damaged, and offering to download unwanted applications to fix it:
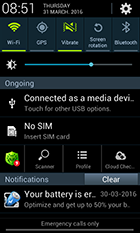
The following examples demonstrate advertisements that are displayed in the notification bar and advertising shortcuts, tapping which leads to webpages of advertised applications published on Google Play:
It is noteworthy that a plug-in hidden in the Trojan’s program package possesses the same features as the Android.Spy.277.origin itself. Once the Trojan receives instructions from the server, it tries to install this plug-in, masquerading it as an important update. Therefore, the device, in fact, contains two copies of Android.Spy.277.origin—thus, even if the original version of the Trojan is deleted, there is still its counterpart, which continues to deliver advertisements.
The Trojan is currently known to compromise the following applications:
- com.true.icaller
- com.appstorenew.topappvn
- com.easyandroid.free.ios6
- com.entertainmentphotoedior.photoeffect
- lockscreenios8.loveslockios.com.myapplication
- com.livewallpaper.christmaswallpaper
- com.entertainment.drumsetpro
- com.entertainment.nocrop.nocropvideo
- com.entertainment.fastandslowmotionvideotool
- com.sticker.wangcats
- com.chuthuphap.xinchu2016
- smartapps.cameraselfie.camerachristmas
- com.ultils.scanwifi
- com.entertainmenttrinhduyet.coccocnhanhnhat
- com.entertainment.malmath.apps.mm
- com.newyear2016.framestickertet
- com.entertainment.audio.crossdjfree
- com.igallery.styleiphone
- com.crazystudio.mms7.imessager
- smartapps.music.nhactet
- com.styleios.phonebookios9
- com.battery.repairbattery
- com.golauncher.ip
- com.photo.entertainment.blurphotoeffect.photoeffect
- com.irec.recoder
- com.Jewel.pro2016
- com.tones.ip.ring
- com.entertainment.phone.speedbooster
- com.noelphoto.stickerchristmas2016
- smartapps.smstet.tinnhantet2016
- com.styleios9.lockscreenchristmas2016
- com.stickerphoto.catwangs
- com.ultils.frontcamera
- com.phaotet.phaono2
- com.video.videoplayer
- com.entertainment.mypianophone.pianomagic
- com.entertainment.vhscamcorder
- com.o2yc.xmas
- smartapps.musictet.nhacxuan
- com.inote.iphones6
- christmas.dhbkhn.smartapps.christmas
- com.bobby.carrothd
- om.entertainment.camera.fisheyepro
- com.entertainment.simplemind
- com.icall.phonebook.io
- com.entertainment.photo.photoeditoreffect
- com.editphoto.makecdcover
- com.tv.ontivivideo
- smartapps.giaixam.gieoquedaunam
- com.ultils.frontcamera
- com.applock.lockscreenos9v4
- com.beauty.camera.os
- com.igallery.iphotos
- com.calculator.dailycalories
- com.os7.launcher.theme
- com.trong.duoihinhbatchu.chucmungnammoi
- com.apppro.phonebookios9
- com.icamera.phone6s.os
- com.entertainment.video.reversevideo
- com.entertainment.photoeditor.photoeffect
- com.appvv.meme
- com.newyear.haitetnew
- com.classic.redballhd
- com.entertainmentmusic.musicplayer.styleiphoneios
- com.camera.ios8.style
- com.countdown.countdownnewyear2016
- com.photographic.iphonecamera
- com.contactstyle.phonebookstyleofios9
- com.entertainment.blurphotobackground.photoeffect.cameraeditor.photoeffect
- com.color.christmas.xmas
- com.bottle.picinpiccamera
- com.entertainment.videocollagemaker
- com.wallpaper.wallpaperxmasandnewyear2016
- com.ultils.lockapp.smslock
- com.apppro.phonebookios9
- com.entertainment.myguitar.guitarpro
- com.sticker.stickerframetet2016
- com.bd.android.kmlauncher
- com.entertainment.batterysaver.batterydoctor
- com.trong.jumpy.gamehaynhatquadat
- com.entertainmentphotocollageeditor
- smartapps.smsgiangsinh.christmas2016
- smartapps.musicchristmas.christmasmusichot
- com.golauncher.ip
- com.applock.lockscreenos9v4
- com.imessenger.ios
- com.livewall.paper.xmas
- com.main.windows.wlauncher.os.wp
- com.entertainmentlaunchpad.launchpadultimate
- com.fsoft.matchespuzzle
- com.entertainment.photodat.image.imageblur
- com.videoeditor.instashot
- com.entertainment.hi.controls
- com.icontrol.style.os
- smartapps.zing.video.hot
- com.photo.entertainment.photoblur.forinstasquare
- com.entertainment.livewallpaperchristmas
- com.entertainment.tivionline
- com.iphoto.os
- com.tool.batterychecker
- com.photo.multiphotoblur
- smartapps.nhactet.nhacdjtet
- com.runliketroll.troll
- com.jinx.metalslug.contra
Doctor Web strongly recommends Android users to pay careful attention to applications they are going to download, and install programs developed only by reputable companies. Dr.Web for Android successfully detects and removes all known modifications of Android.Spy.277.origin, and, therefore, this malicious program poses no threat to our users.






![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments