New multipurpose backdoor for Linux detected
Real-time threat news | Hot news | All the news | Virus alerts
January 22, 2016
This malicious program was added to the Dr.Web virus database under the name of Linux.BackDoor.Xunpes.1. It consists of a dropper and the backdoor itself that performs main spy functions on an affected device.
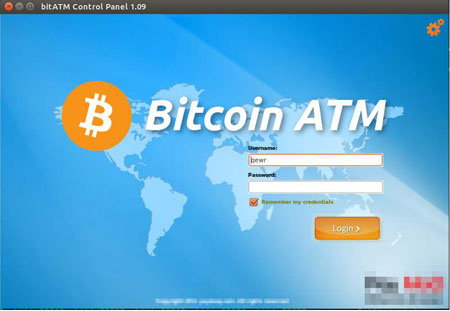
The dropper is contrived using Lazarus, a free cross-platform IDE for the Free Pascal compiler. Once launched, it displays the following dialog with a list of devices designed to carry out operations with the Bitcoin cryptocurrency:
The dropper body contains the backdoor—the second component of the Trojan—that is stored in unencrypted form and saved into the /tmp/.ltmp/ folder after the dropper is launched. It is the backdoor that is responsible for performing main malicious functions.
Once launched, the backdoor written in C decrypts the configuration file using the key that is hard-coded in its body. Its configuration parameters include a list of C&C servers and proxy servers addresses and other information necessary for the correct operation of the malicious program. After that, the Trojan establishes connection to the server and waits for commands from cybercriminals.
In total, Linux.BackDoor.Xunpes.1 is capable to execute more than 40 commands. Among them are keylogging—recording of keystrokes on an infected device—and downloading and running of a file, whose path and arguments are received from the server, which terminates the work of the backdoor. Besides, it can also send file names in a specified directory and upload selected files to the server. In addition to this, the Trojan creates, removes and renames files and folders, takes screenshots, executes the bash commands; and the list is far from being exhaustive.
The signature of Linux.BackDoor.Xunpes.1 has been added to Dr.Web virus databases. Thus, users of Dr.Web for Linux are under reliable protection.