About 2,000 websites already compromised by Linux.Encoder.1
Real-time threat news | Hot news | All the news | Virus alerts
November 13, 2015
Cybercriminals distributing Linux.Encoder.1 mainly targeted websites deployed on servers running Linux and created using various content management systems (CMS), for example, WordPress, and such online-store management system as Magento. To mount attacks, virus makers exploited an unidentified vulnerability.
Once cybercriminals could get access to a website, the error.php file was planted on that Internet resource (for Magento, it was placed into the /skin/ system directory). That file acted as a shell script allowing cybercriminals to perform other illegal actions, in particular, by sending it various commands. Using the script, hackers could plant the 404.php file, which was, in fact, a dropper for Linux.Encoder.1, on a server. It is assumed that upon a command from cybercriminals issued by referring to the PHP file after entering an appropriate address into the browser address bar, the dropper identifies the operating system architecture (32-bit or 64-bit), extracts from the body a corresponding sample of encryption ransomware, runs it, and then initiates its own removal.
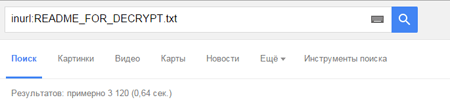
Since Linux.Encoder.1 is run with www-data privileges (that is, it is run with the same user privileges as Apache itself runs), these privileges are enough to encrypt all files in directories for which this particular user has write-access permissions, in other words, directories with files and components of the CMS. If, by some chance, the Trojan acquires more elevated privileges, its malicious activities will not be limited to the web server directory alone. After that, the malicious program saves the README_FOR_DECRYPT.txt file containing decryption instructions and cybercriminals' demands on the server disk. Judging from search results acquired by using an appropriate Google query, as of November 12, 2015, about 2,000 websites have already been compromised by Linux.Encoder.1.
The attack scheme shows that cybercriminals do not actually need root privileges to compromise web servers running Linux and encrypt files. Moreover, the Trojan still poses a serious threat to Internet resources owners, especially taking into account that many popular CMSes have unfixed vulnerabilities, and some webmasters either disregard the necessity of timely updates or just use outdated versions of CMSes.
Due to the fact that the code of Linux.Encoder.1 has a number of significant flaws, data encrypted by the Trojan can be decrypted. If your files have been compromised by Linux.Encoder.1, follow the guidance below:
- Notify the police.
- Do not, under any circumstances, attempt to change the contents of directories with encrypted files.
- Do not delete any files from the server.
- Do not try to restore the encrypted data by yourself.
- Contact Doctor Web technical support (free decryption service is only available to users who have purchased commercial licenses for Dr.Web products).
- Attach a file encrypted by the Trojan to the request ticket.
- Wait for a response from technical support. Due to a large number of requests, it may take some time.
Once again we would like to point out that free decryption service is only available to users who have purchased commercial licenses for Dr.Web products. Doctor Web cannot guarantee that all your files will be decrypted successfully. However, our specialists will do their best to recover the encrypted data.
Despite the fact that some flaws in the architecture of Linux.Encoder.1 prevent it from irreversibly damaging or destroying all server data, there is a possibility that after some time cybercriminals will come up with a way to fix all current bugs. That is why even users of such relatively secure OS as Linux—especially webmasters of websites running on popular platforms—can get affected by malicious actions of this program. We would like to remind Internet users that Linux.Encoder.1 has already been added to Dr.Web virus databases for Linux. Doctor Web security researchers will continue to monitor this situation.