Encryption ransomware threatens Linux users
Real-time threat news | Hot news | All the news | Virus alerts
November 6, 2015
Once launched with administrator privileges, the Trojan dubbed Linux.Encoder.1 downloads files containing cybercriminals' demands and a file with the path to a public RSA key. After that, the malicious program starts as a daemon and deletes the original files. Subsequently, the RSA key is used to store AES keys which will be employed by the Trojan to encrypt files on the infected computer.
First, Linux.Encoder.1 encrypts all files in home directories and directories related to website administration. Then the Trojan recursively traverses the whole file system starting with the directory from which it is launched; next time, starting with a root directory (“/”). At that, the Trojan encrypts only files with specified extensions and only if a directory name starts with one of the strings indicated by cybercriminals.
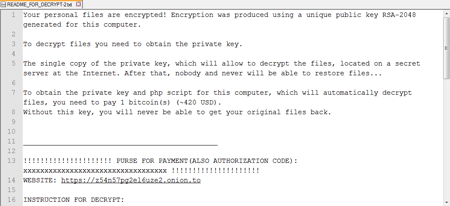
Compromised files are appended by the malware with the .encrypted extension. Into every directory that contains encrypted files, the Trojan plants a file with a ransom demand—to have their files decrypted, the victim must pay a ransom in the Bitcoin electronic currency.
Doctor Web recommends users whose files have been encrypted to contact technical support providing detailed information on the incident and sending several samples of encrypted files. To decrypt files, it is very important that the user does not modify or delete them—otherwise, encrypted data may be permanently lost.