September 2015 mobile malware review from Doctor Web
October 1, 2015
PRINCIPAL TRENDS IN SEPTEMBER
- First large-scale attack on the App Store
- Detection of a large number of Trojans on Google Play
- New cases of Android firmware being infected with malicious applications
- Emergence of new Android ransomware
- Banking Trojans continue to threaten mobile devices' owners
Number of entries for malicious and unwanted software targeting Android OS in Dr.Web virus database
| August 2015 | September 2015 | Dynamics |
|---|---|---|
| 12,504 | 14,033 | +12.23% |
Mobile threat of the month
In September, one of the most significant mobile security events was related to detection of IPhoneOS.Trojan.XcodeGhost in the App Store that was previously considered the most reliable source of applications for iOS devices. However, cybercriminals found a way to bypass the store's protection system by modifying one of Apple's official developer tools called Xcode and providing the fake suite to creators of legitimate software. As a result, the modified version injected the malicious code into applications already at the assembly stage. This led to originally harmless games and applications, which were “infected” using this method, being able to make their way past Apple's stringent review process and get into the App Store. Due to the fact that the counterfeit software was distributed among Chinese developers, the majority of users affected by activities of IPhoneOS.Trojan.XcodeGhost are owners of iOS devices from China. However, users from other counties could have also fallen victim to this malicious program if they had downloaded infected versions of legitimate applications.
Once an application with embedded IPhoneOS.Trojan.XcodeGhost is launched, the Trojan starts gathering information about the infected device (including its type, model name and UUID, current system language, and data on the network operator) sending it to the command and control server. However, the main threat of IPhoneOS.Trojan.XcodeGhost lies in the fact that it can display fake dialogs to carry out phishing attacks, open links specified by cybercriminals, and even steal passwords from clipboard history.
Banking Trojans
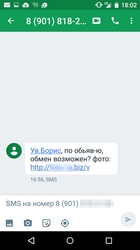
In the past month, cybercriminals continued to target owners of Android devices in order to steal their money. In particular, at the beginning of the month, Doctor Web security researchers registered an SMS spam campaign aimed at users who placed advertisements on some Internet resources. Messages from that campaign offered victims to visit a website to find out more about the possible deal. It should be noted that in some cases the victim was referred by their name, which made this whole scheme quite easy to believe in. If the user actually opened the link from such a message, Android.SmsBot.459.origin designed to steal money from users' bank accounts was downloaded to the mobile device. For more information regarding this incident, refer to the news article published by Doctor Web.
The number of entries for banking Trojans of the Android.SmsBot family in Dr.Web virus database:
| August 2015 | September 2015 | Dynamics |
|---|---|---|
| 495 | 520 | +5% |
Firmware Trojans
The middle of September witnessed a new case of Android firmware being infected with a Trojan. This time, owners of Oysters T104 HVi 3G were the ones who fell victim to a malicious program dubbed Android.Backdoor.114.origin. Due to the fact that the program is incorporated directly into mobile device firmware, it becomes almost impossible to remove it using ordinary tools. To be able to get rid of the malware, the user needs to acquire root privileges, which can be hard (or even dangerous) to accomplish. Another way is to reinstall the operating system. The main purpose of Android.Backdoor.114.origin is to stealthily download, install, and remove applications upon a command from the command and control server. Moreover, the Trojan can activate the disabled option to install applications from unreliable sources and send a remote server comprehensive information regarding the infected device. For more information regarding the malware, refer to this news article.
Android ransomware
In September, some anti-virus companies reported on detection of a ransomware Trojan for Android (dubbed Android.Locker.148.origin by Doctor Web specialists) that was said to use new methods of gaining administrator privileges and setting unlock passwords on compromised mobile devices. However, malicious programs possessing the same features have been already known to Doctor Web security researchers since 2014—in particular, such Trojans as Android.Locker.38.origin and Android.BankBot.29.origin can be mentioned in regards to this news.
Like other programs belonging to this category, right after it is launched, Android.Locker.148.origin attempts to acquire administrator privileges to perform all malicious activities “in full force” and to be protected against removal. To do that, the Trojan displays a notification message on top of a standard system dialog prompting the user to install some update. By giving their consent, the user grants the Trojan administrator privileges. If this happens, the Trojan will be able to lock the device without any problems setting an unlock password and demanding a ransom.
The number of entries for Android ransomware in Dr.Web virus database:
| August 2015 | September 2015 | Dynamics |
|---|---|---|
| 431 | 490 | +13.7% |
Trojans on Google Play
Despite all the efforts taken by Google to ensure utmost protection of Google Play, cybercriminals continue to infiltrate it with all sorts of malicious applications. One of such applications, detected on the mentioned resource and dubbed Android.MKcap.1.origin, was embedded in various games and possessed a rather interesting set of features. In particular, cybercriminals employed it to automatically subscribe users to various chargeable services. The routine looked as follows: first, Android.MKcap.1.origin received a link to some webpage with premium content; then it copied CAPTCHA from that website uploading it to a web portal of a well-known CAPTCHA recognition service. As soon as the image was solved, the Trojan forwarded the result to the webpage with premium content to complete the registration process. At that, if during registration some additional SMS messages with conformation codes were received from the service, Android.MKcap.1.origin processed them too forwarding results to the website.
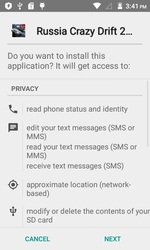
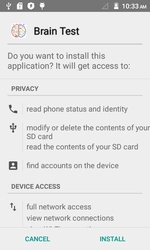
Another Trojan detected on Google Play in September was Android.Backdoor.273.origin. This dangerous backdoor that uses a step-by-step algorithm to infect targeted mobile devices was incorporated into the application called Brain Test. The program itself does not contain the payload—it is downloaded from a remote server. Once launched, Android.Backdoor.273.origin downloads from the remote server several exploits and tries to execute them to acquire root privileges. If successful, the Trojan gets its second malicious component (detected as Android.DownLoader.173) from the server. This component is subsequently used by cybercriminals to download and install other malware on the device.
The features of Android.Backdoor.273.origin are as follows:
- Once launched, the Trojan checks the IP address of the domain used for establishing network connection on the device. If it corresponds to a Google address, the Trojan terminates its work. This technique allows cybercriminals to get past the Google Bouncer.
- Depending on the modification, the malicious program can be either protected by a special packer, which encrypts its code, or be distributed without this protection.
- Tries to acquire root privileges using four exploits downloaded from the command and control server one by one.
- Installs another Trojan that stealthily downloads and installs other malware on the compromised device.
- Installs two additional malicious components that constantly check integrity of each other and, if one of them (or Android.Backdoor.273.origin) is removed, download necessary files and infect the device once again.
Moreover, in September, yet another Trojan was detected on Google Play—the malicious program incorporated into harmless games was added to Dr.Web virus database as Android.MulDrop.67. Depending on the modification, once Android.MulDrop.67 is launched, it can either start performing its malicious activities at once or wait 24 hours to put the victim off their guard. In both cases the Trojan extracts Android.DownLoader.217.origin from its body trying to install it on the device. At that, Android.DownLoader.217.origin prompts the user to grant it administrator privileges to be protected against removal. The main purpose of these malicious programs is to display advertisements and download and install other Trojans.
[% END %]