October 1, 2015
The beginning of autumn was marked by high activity on the part of virus makers—in September, security researchers detected several installers of unwanted and adware applications designed for Windows and OS X. Moreover, various malicious programs for Linux and Android and a new Trojan targeting POS terminals came into light.
PRINCIPAL TRENDS IN SEPTEMBER
- Emergence of a new Trojan for POS terminals
- Distribution of new installers of adware and unwanted applications for Windows and OS X
- Distribution of new malicious programs for Android and Linux
Threat of the month
For many years POS terminals running Windows operating systems remain one of the most favorite targets for virus makers. Various methods of stealing bank card data stored by such devices have been known to cybercriminals for quite some time. In September, Doctor Web security researchers examined a malicious program that was used for exactly that purpose—the Trojan, which turned out to be a modification of BackDoor.Neutrino.50, was dubbed Trojan.MWZLesson.
Trojan.MWZLesson can execute the following commands:
- CMD—forward the command to the command interpreter (cmd.exe)
- LOADER—download and run a file (dll—using the regsrv tool, vbs—using the wscript tool, exe—run directly)
- UPDATE—update itself
- rate—set a time interval for communication sessions with the command and control server
- FIND—search documents using a mask
- DDOS—mount an HTTP Flood attack
For more information regarding this Trojan, refer to the news article published by Doctor Web.
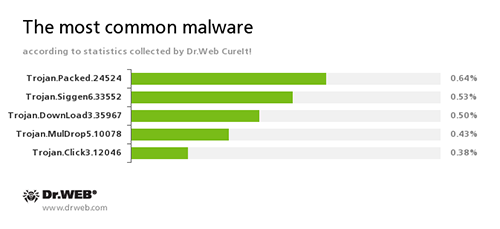
According to the statistics gathered by Dr.Web CureIt!
Over the course of September, Dr.Web CureIt! detected 155,554,503 unwanted, potentially dangerous, and malicious objects.
Trojan.Packed.24524
An installer of adware and unwanted programs distributed by cybercriminals under the guise of legitimate software.
Trojan.Siggen6.33552
A malicious program designed to install other dangerous software on the infected computer.
Trojan.DownLoad3.35967
A Trojan that can download other malicious programs from the Internet and install them on the infected computer.
Trojan.MulDrop5.10078
A malicious program designed to install other malware on the infected computer.
Trojan.Click
A family of malicious programs designed to generate traffic for various websites by redirecting users to the corresponding webpages.
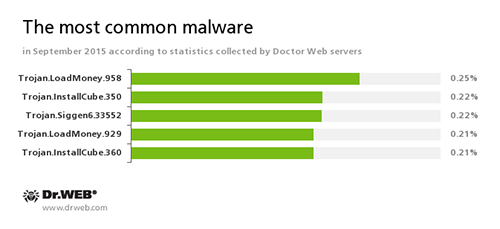
According to Doctor Web statistics servers
Trojan.LoadMoney
A family of downloader programs generated by servers belonging to the LoadMoney affiliate program. These applications download and install unwanted software on the victim's computer.
Trojan.InstallCube
A family of downloader programs designed to install unwanted and useless applications on the user’s computer.
Trojan.Siggen6.33552
A malicious program designed to install other dangerous software on the infected computer.
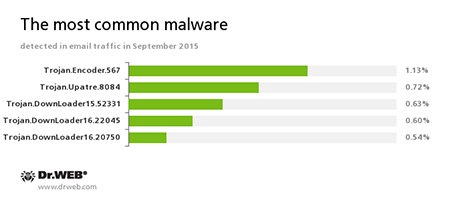
Statistics concerning malicious programs discovered in email traffic
Trojan.Encoder.567
A malicious program belonging to the family of encryption ransomware Trojans that encrypt files and demand a ransom for decryption of compromised data. This program can encrypt important user files, for example, of the following types: .jpg, .jpeg, .doc, .docx, .xls, xlsx, .dbf, .1cd, .psd, .dwg, .xml, .zip, .rar, .db3, .pdf, .rtf, .7z, .kwm, .arj, .xlsm, .key, .cer, .accdb, .odt, .ppt, .mdb, .dt, .gsf, .ppsx, .pptx.
Trojan.Upatre
A family of Trojans that covertly download and install other malicious applications on the infected computer.
Trojan.DownLoader
A family of malicious programs designed to download other malware to the compromised computer.
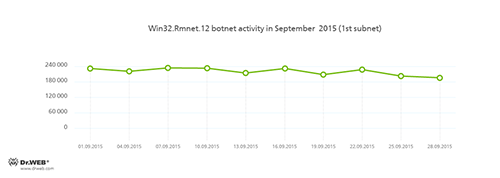
Botnets
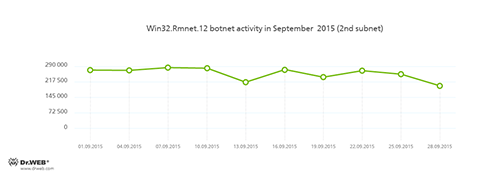
Doctor Web security researchers continue to monitor botnets created by cybercriminals using the Win32.Rmnet.12 file infector. The average daily activity of these botnets is shown in the following graphs:
Rmnet—is a family of viruses spread without any user intervention. They can embed content into loaded webpages (this theoretically allows cybercriminals to get access to the victim's bank account information), steal cookies and passwords stored by popular FTP clients, and execute other commands issued by cybercriminals.
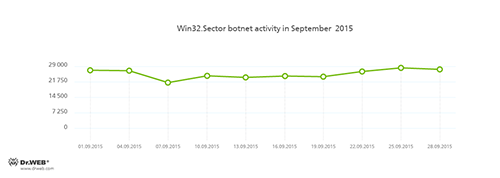
The botnet consisting of computers infected with Win32.Sector is also still active. Its average daily activity can be seen in the following picture:
Win32.Sector can perform the following actions:
- Download various executable files via P2P networks and run them on infected machines.
- Inject its code into running processes.
- Prevent some anti-viruses from operating and block access to the websites of their respective developers.
- Infect files on local disks, removable media (where the malware creates the autorun.inf file during the infection process), and in shared folders.
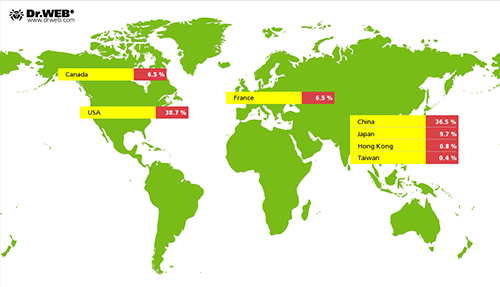
In September, cybercriminals controlling the Linux.BackDoor.Gates.5 botnet became more active and intensified DDoS attacks on various Internet resources—in comparison with the previous month, the number of attacked IP addresses increased by 263.5 per cent and was estimated 7,572. At that, the United States were ranked first, while China took the second place. Detailed information on locations of cybercriminals' targets is presented in the following picture:
Encryption ransomware
The number of requests for decryption received by Doctor Web technical support service
| August 2015 | September 2015 | Dynamics |
|---|---|---|
| 1,425 | 1,310 | -8% |
The most common ransomware programs in September 2015
- Trojan.Encoder.567
- Trojan.Encoder.858
Dr.Web Security Space 10.0 for Windows
protects against encryption ransomware
This feature is not available in Dr.Web Anti-virus for Windows
| Preventive Protection | Data Loss Prevention |
|---|---|
 |  |
Linux
In September 2015, Doctor Web security researchers had to face Linux Trojans once again—among them, Linux.Ellipsis.1 and Linux.Ellipsis.2 are the most noteworthy. The latter Trojan is designed to brute-force login systems of various devices using a special vocabulary. To ensure anonymous access to devices hacked by means of Linux.Ellipsis.2, cybercriminals employ Linux.Ellipsis.1. This malicious program has a rather interesting behavior described by Doctor Web security researchers as “paranoid”.
Linux.Ellipsis.1 is designed to set up a proxy server on the infected machine allowing cybercriminals to get anonymous access to compromised devices. For that, the Trojan monitors connections on a local address and port proxying all traffic transmitted via them.
The “paranoid” behavior of Linux.Ellipsis.1 also lies in the fact that the Trojan encompasses a large list of strings for which it searchers network traffic. If any of the strings is detected, the Trojan blocks data transfer to the remote server at the corresponding IP address. Apart from blocking remote nodes from the list, the malware checks all network connections and sends the remote server the IP address to which the connection is established. If the server responds with the “kill” command, the Trojan shuts down the application that established the connection and blocks the IP address for two hours. For more information regarding these Trojans, refer to the news article published by Doctor Web.
Dangerous programs targeting OS X
Installers of adware and unwanted applications for Windows do not come as a surprise to the majority of Internet users. However, in September, Doctor Web security researchers detected an installer that targeted not Windows but OS X. This sample, which was dubbed Adware.Mac.WeDownload.1, is disguised as a distribution package of Adobe Flash Player and spreads by means of an affiliate program focused on generating income from file downloads.
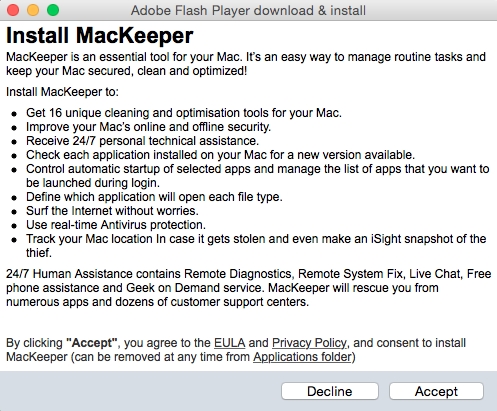
Once an appropriate request is sent, Adware.Mac.WeDownload.1 receives from the command and control server a list of applications that the user will be prompted to install. The list has not only unwanted programs but also malicious ones, including Program.Unwanted.MacKeeper, Mac.Trojan.Crossrider, Mac.Trojan.Genieo, Mac.BackDoor.OpinionSpy, various Trojans belonging to the Trojan.Conduit family, and some other dangerous applications. At that, the total number and types of programs depend on the victim's geolocation.
Find out more about the installer in this news article.
Other malicious applications
In September 2015, installers of unwanted, adware, and even dangerous applications distributed via affiliate programs focused on generating income from file downloads became especially widespread.
In particular, at the beginning of the month, Doctor Web security researchers examined Trojan.InstallCube.339—this malicious program can be downloaded by potential victims from various fake file-sharing resources and torrent trackers. Once launched, the Trojan retrieves the configuration file from the server and then demonstrates the user a dialog with information on the downloaded object. At that, the dialog supposedly belongs to the well-known mTorrent application. Servers that control this program have a rather interesting way of behavior—they allow Trojan.InstallCube.339 to download the payload only if the infected computer has a Russian IP address.
Another dangerous installer was dubbed by security researchers as Trojan.RoboInstall.1. Like many other programs belonging to this category, the Trojan is distributed though file-sharing websites, fake torrent trackers, and other similar Internet resources created by cybercriminals. Moreover, some developers of free applications also employ such malicious programs to generate income. As a result, they receive monetary compensation for every additional tool downloaded by Trojans to victims' computers. However, this particular installer has one characteristic feature—sometimes dialogs displayed by Trojan.RoboInstall.1 do not contain installation check boxes, and files downloaded by the Trojan get installed without any conditions.
At the end of September, cybercriminals made an attempt to distribute a malicious application via email messages claiming to be from Doctor Web.
Cybercriminals offered their victims to take part in testing of some tool called Dr.Web CureIt 2. However, instead of this “tool”, Trojan.PWS.Stealer.13052 was downloaded to users' computers. This Trojan is designed to steal passwords and other confidential information stored on compromised machines. To make the number of infected devices larger, cybercriminals prompted users to turn off their anti-virus software, because it can be incompatible with the “tool”. For more information regarding the incident, refer to this news article.
Dangerous websites
During September 2015, 399,227 URLs of non-recommended websites were added to Dr.Web database.
| August 2015 | September 2015 | Dynamics |
|---|---|---|
| +834,753 | +399,227 | -51.39% |
Malicious and unwanted programs for Android
September proved to be quite rich in terms of mobile security events. Over the course of the first autumn month, security researchers detected a large number of programs containing a Trojan in the App Store. Moreover, once again, cybercriminals used Google Play to distribute their malicious creations. In the middle of the month, Doctor Web analysts registered yet another incident of Trojans being embedded in official Android firmware. Banking Trojans, Android ransomware, and other malicious applications also continued to threaten mobile devices' users.
Among the most noticeable events related to mobile malware we can mention
- Detection of a large number of programs containing IPhoneOS.Trojan.XcodeGhost in the App Store
- Detection of a large number of Trojans on Google Play
- New case of Android firmware being infected with a malicious application
- Emergence of new Android ransomware
- Distribution of new banking Trojans for Android
Find out more about malicious and unwanted programs for mobile devices in our special overview.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live