Cybercriminals continue to steal money from Android users
Real-time threat news | Hot news | Threats to mobile devices | All the news
September 21, 2015
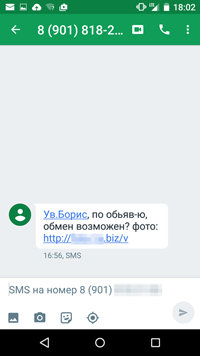
Like other similar malicious programs, this new Trojan, dubbed Android.SmsBot.459.origin, is distributed by cybercriminals via SMS spam. In particular, a potential victim receives a message supposedly from a person who is interested in some advertised item. The message offers the victim to visit a website to find out more about the possible deal. It should be noted that in some cases the victim is referred by their name—thus, we can draw a conclusion that for this well-planned attack cybercriminals used a specially generated base of real advertisements. Such scheme is very likely to fool the victim—if some time ago they actually tried to sell something via the Internet, the message will not raise any suspicions, and the link will be opened. If this happens, the Trojan's APK file will be downloaded to the device. However, for Android.SmsBot.459.origin to start operating, the user needs to install it by themselves. If the user attempts to open the link on a device running under an operating system different from Android, they will be redirected to some harmless resource instead of the one from which the Trojan is downloaded.
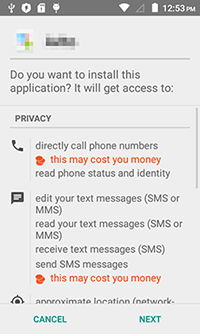
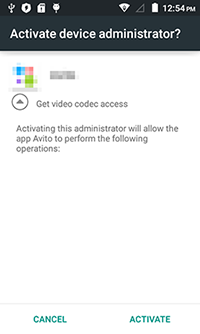
Android.SmsBot.459.origin is disguised as a client application for an advertising website well known in Russia. Even the icon is borrowed from the original program—this way, a potential victim should not have any doubts that they are dealing with the real advertising platform. Right after the Trojan is launched, it attempts to acquire administrator privileges to protect itself from being removed. Moreover, by constantly prompting the user to grant it administrator privileges, the Trojan makes working with the device almost impossible.
Android.SmsBot.459.origin sends the command and control server device-related information, including IMEI, mobile network operator, OS version. As a reply, the Trojan receives a command to check the device for online banking applications of several financial organizations. The malware also checks balances of the user's mobile account and their account in one popular Russian payment system. To do that, the malicious program sends special text messages to all these services concealing replies from the user and forwarding them to the remote server. It should be noted that additional security measures introduced in Android 4.4 and later make it impossible for the Trojan to hide SMS messages from the user—the malicious program just deactivates all sound alerts (including vibro call) and deletes all incoming texts.
Android.SmsBot.459.origin can execute the following commands:
- esms&&& —send a list of all SMS messages to the server,
- getapps&&& —send a list of installed applications to the server,
- sent&&& —send an SMS with a predefined text to the specified number,
- rent&&& —enable intercepting SMS messages,
- sms_stop&&& —disable intercepting SMS messages,
- ussd&&& —send a USSD query,
- export&&& —send a list of contacts to the server,
- u&&& —set a new command and control server address,
- sapp&&& —send a message to the specified number via Viber.
Thus, if the user has money on any of the mentioned accounts, cybercriminals can steal it by issuing an appropriate command. At that, the victim finds out about the attack not right after the crime is committed but some time later, because the Trojan blocks all messages containing conformation codes and notifications on financial operations.
Doctor Web security researchers strongly advise Android users against opening links from dubious SMS messages and installing applications downloaded from unreliable sources. Dr.Web for Android successfully detects Android.SmsBot.459.origin, and, therefore, this malicious program poses no threat to our users.