A downloader Trojan hides in Word documents
Real-time threat news | Hot news | All the news | Virus alerts
August 14, 2015
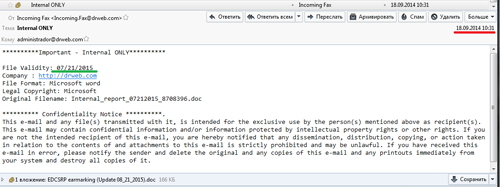
W97M.DownLoader.507 is a Microsoft Word document distributed as an attachment to email messages—at that, a sample examined by Doctor Web security researchers was disguised as a fax message. However, cybercriminals made a significant mistake specifying a wrong creation date.
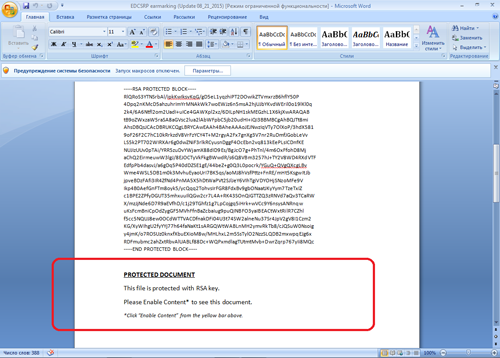
The file itself is supposed to be encrypted with RSA. To be able to read the contents of the message, the victim is prompted to enable macros.
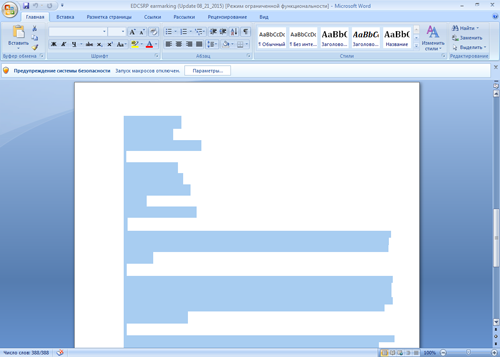
The document also contains an empty page that actually has the text typed in white which becomes visible once the user enables macros.
After macros are activated, the text is shown to the victim. At the same time, the Trojan starts downloading several code fragments from the remote server. Using these fragments and depending on the Windows version, the malicious program generates scripts with .bat, .vbs, or .ps1 extensions, saves them on the computer, and then runs. The scripts, in turn, download from the server controlled by cybercriminals an executable file and run it—in our case, W97M.DownLoader.507 was used to deliver Trojan.Dyre.553, which is a dangerous banking Trojan, to the infected computer.
Once again Doctor Web analysts would like to remind users to be careful and cautious—it is not recommended to open Microsoft Office attachments received from unknown senders without checking them with anti-virus software first. Moreover, we strongly advice against enabling macros in Word if you decide to open an attached Word file.