Dangerous banking Trojan threatens Android users
Real-time threat news | Hot news | All the news | Virus alerts
June 11, 2015
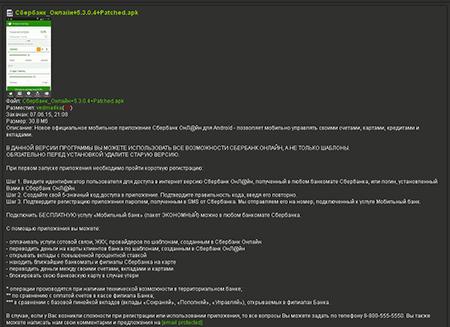
Security researchers have been familiar with the following malware distribution scheme for quite some time: cybercriminals inject malicious code into legitimate applications planting them in various software catalogues and on file-sharing resources. Due to the fact that a compromised application looks and operates as a legitimate one, potential victims are very likely to install it on their mobile devices. However, instead of a real program, users get a modified version containing a Trojan able to perform different malicious actions on the infected device.
Recently, Doctor Web analysts have detected a banking Trojan under the name of Android.BankBot.65.origin incorporated into a Sberbank Online mobile application and distributed using the scheme described above. By adding malicious functionality to the program, Cybercriminals modified it and planted the new version on one popular website dedicated to mobile devices. The compromised copy of an application operates exactly like its original version; so users do not expect the downloaded program to be a malicious one, which puts their confidential data in danger. So far, more than 70 Android devices' owners have already downloaded the modified application.
Once the compromised version is installed and run, Android.BankBot.65.origin creates a special configuration file containing operating parameters for the Trojan. Using these settings, the malware establishes a connection to the command and control server and sends it the following information using a POST request:
- IMEI
- Mobile network operator
- MAC address of the Bluetooth adapter
- Data on availability of QIWI Wallet
- API version of the device
- Trojan's version
- Trojan's package name
- Currently executed command
If Android.BankBot.65.origin receives the “hokkei” command from the remote host, it sends an encrypted list containing the user's contacts to the server and updates the configuration file upon cybercriminals' command.
This malware is rather similar to other banking Trojans. In particular, like other Trojans belonging to this family, Android.BankBot.65.origin can perform the following actions: upon the server's command, it can intercept incoming SMS messages and send different texts to numbers specified by cybercriminals. Moreover, Android.BankBot.65.origin can add various texts to the list of incoming SMS messages. Using these methods, cybercriminals can steal money from users' bank accounts (by sending SMS commands to transfer money from the victim's account to the account of cybercriminals or by intercepting messages containing verification codes) and implement other fraudulent schemes. For example, cybercriminals can plant a specially generated message informing the user that their credit card has been blocked and asking them to call the “bank” at the specified number or a message prompting the user to refill a mobile phone account of “a relative who got into some trouble”, or some other message.
Doctor Web security researchers strongly recommend Android devices' owners to download online banking applications only from reliable sources (for example, from Google Play or from official websites of credit organizations) and to use Dr.Web for Android or Dr.Web for Android Light to protect their devices. The signature of Android.BankBot.65.origin has been added to Dr.Web virus database. Therefore, this malicious program poses no threat to our users.