Attack of a dangerous Trojan on a defense enterprise has been prevented
Real-time threat news | Hot news | All the news | Virus alerts
April 7, 2015
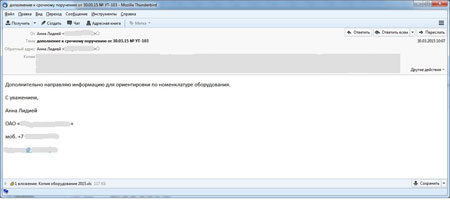
The backdoor, that acquired the name BackDoor.Hser.1, was spread via targeted mass mailing to private and corporate email addresses of the employees of more than ten enterprises that are members of a famous Russian group of companies. All these enterprises are engaged in defense activities or act for military industrial complex. The letter was supposedly sent from an employee of a group of companies headquarters and was titled «Дополнение к срочному поручению от 30.03.15 № УТ-103» (“Addition to an urgent task as of 03/30/15 #UT-103 ”). The message was said to contain a list of some equipment. Attached to the message was a Microsoft Excel file under the name Копия оборудование 2015.xls (Copy equipment 2015.xls).
The file attached to the message contains an exploit that uses the vulnerability CVE2012-0158 that exists in some versions of Microsoft Excel. Once this file is opened on a targeted computer, the excel.exe process, in which this Trojan’s dropper is embedded, is being launched.
From its body, the dropper unpacks the backdoor BackDoor.Hser.1 and saves it on a disk in the folder C:\Windows\Tasks\ under the name npkim.dll, registers this library in the parameters of Windows auto boot and launches the cmd.exe command interpreter to delete the process file in which it was originally embedded.
Once it is launched on an infected computer, BackDoor.Hser.1 decrypts the control and command server address, that is stored in its body, and establishes a connection with this server. The Trojan sends information about the infected computer (computer IP address, its name, operating system version, details regarding the presence of a proxy server in the network) to criminals and waits for further criminals’ commands. Moreover, on a command this malicious program can send a list of active processes that run on the infected PC to a remote server, download and launch any other malicious application, and also open the command console and execute input/output redirection to a cybercriminals’ server, allowing criminals get control over the infected computer.
The signature of the Trojan BackDoor.Hser.1 has been added to Dr.Web virus database, and, therefore, this malicious program no longer poses a threat to computers protected with Dr.Web. Nevertheless, once again we would like to remind our readers of how important it is to install the most recent antivirus software and keep the virus databases up-to-date.