February 10, 2015
Viruses
According to statistics gathered during 2014 with Dr.Web CureIt!, Trojan.Packed.24524, which installs other malware on compromised machines, was the absolute leader in terms of how often it was detected on PCs in the past twelve months. The adware browser pluginsTrojan.BPlug.123 and Trojan.BPlug.100 ranked second and third. These plugins, which are detected by Dr.Web anti-virus software as Trojan.BPlug programs, can be installed on a computer in a variety of ways without the user's knowledge or consent (for example, when installing other free applications) and can incorporate advertisements into loaded webpages to promote all kinds of fraudulent sites.
The 10 malicious programs most frequently detected by Dr.Web CureIt! on PCs in 2014 are listed in the table below:
| Program | % |
|---|---|
| Trojan.Packed.24524 | 1.60 |
| Trojan.BPlug.123 | 0.80 |
| Trojan.BPlug.100 | 0.71 |
| Trojan.MulDrop5.10078 | 0.55 |
| Trojan.BPlug.218 | 0.54 |
| Trojan.BPlug.48 | 0.53 |
| Trojan.BPlug.28 | 0.46 |
| Trojan.Admess.4 | 0.44 |
| Trojan.DownLoader11.3101 | 0.38 |
| Trojan.Click3.8536 | 0.36 |
The statistics clearly indicate that installers of unwanted applications, adware browser plugins, and Trojans that display annoying ads in browsers constitute the greater part of the malicious programs identified. The activity of criminals involved in referral programmes that distribute 'advertising junk' intensified significantly throughout the past year. Apparently, Trojans of this kind yield a substantial income for their makers, so the latter are unlikely to give up on a good thing any time soon. Therefore, the distribution of such programs is expected to persist in 2015.
The SpIDer Gate HTTP monitor incorporated into Dr.Web Security Space 10.0 provides reliable protection from threats of this sort. It blocks access to suspicious sites that are known to be involved in spreading malware.
According to data collected by Doctor Web's statistics servers, Trojan.Packed.24524 (another installer of unwanted software) was most commonly detected on PCs. It was followed by the advertising Trojan program Trojan.InstallMonster.51 which is distributed under the Installmonster referral programme (also known as Zipmonster). These dangerous utilities can install other unwanted applications onto computers. For example, in 2014 Trojan.Click3.9243, which is involved in click fraud, was being spread by Installmonster, as was Trojan.Admess.1 which replaces advertisement code on user-loaded webpages. The 20 most common malicious applications registered by Dr.Web statistics servers in 2014 are shown in the table below:
| 1 | Trojan.Packed.24524 | 0.30% |
| 2 | Trojan.InstallMonster.51 | 0.21% |
| 3 | Trojan.MulDrop5.10078 | 0.20% |
| 4 | BackDoor.IRC.NgrBot.42 | 0.18% |
| 5 | Trojan.LoadMoney.15 | 0.17% |
| 6 | BackDoor.PHP.Shell.6 | 0.16% |
| 7 | Trojan.LoadMoney.1 | 0.14% |
| 8 | Trojan.Fraudster.524 | 0.14% |
| 9 | Trojan.LoadMoney.262 | 0.13% |
| 10 | Trojan.InstallMonster.242 | 0.12% |
| 11 | Win32.HLLW.Shadow | 0.12% |
| 12 | Trojan.MulDrop4.25343 | 0.12% |
| 13 | Trojan.InstallMonster.209 | 0.11% |
| 14 | Win32.HLLW.Autoruner.59834 | 0.11% |
| 15 | Trojan.LoadMoney.263 | 0.11% |
| 16 | Trojan.Triosir.1 | 0.10% |
| 17 | BackDoor.Infector.133 | 0.10% |
| 18 | BackDoor.Andromeda.404 | 0.09% |
| 19 | Win32.HLLW.Gavir.ini | 0.09% |
| 20 | Trojan.LoadMoney.336 | 0.09% |
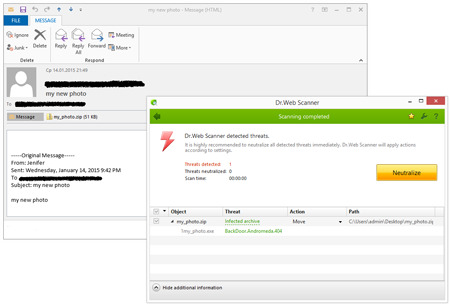
BackDoor.Andromeda.404 was the program most frequently detected by Dr.Web software in email traffic in the past year. Designed to download and install other malicious applications, it was spread on a massive scale as an email attachment throughout 2014.
Trojan.Redirect.197 ranks second. It was added to the virus database in July 2014 and was also spread on a large scale via email. When users opened a bogus message containing this small file, they were redirected to a malignant site from which other Trojans (including Trojan.PWS.Papras.334 which steals confidential information) could be downloaded to their computer.
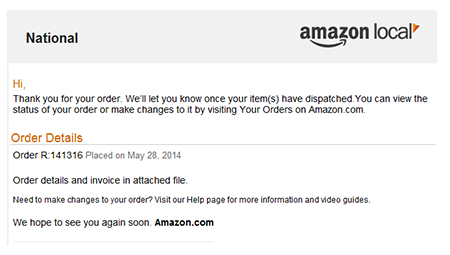
Named “Smoke Loader” by its makers, BackDoor.Tishop.122 is also often distributed with emails, and it ranks third. This program is designed to download other malicious applications onto an infected computer and launch them. In 2014, attackers often sent BackDoor.Tishop.122 in emails that were made to appear to come from various popular web portals and services. For example, in June it was spread with a bulk of fake new “Amazon” order notifications.
After it’s been launched, BackDoor.Tishop.122 scans the surroundings for the presence of a "sandbox" or virtual machine, copies itself into a folder on the hard disk, adds its entry into the autorun section of the Windows Registry, and injects its code into a number of system processes. If an Internet connection exists, the Trojan will attempt to download other malicious programs and run them on the infected computer.
Banking Trojan programs from the Trojan.PWS.Panda family are always on the list of applications considered to be the most popular among spammers. These malicious programs have a wide range of features—they can log keystrokes on an infected PC, execute malicious commands issued by intruders, and take screenshots, but their main purpose is to steal funds from accounts involved in e-banking and to acquire other confidential information. The 20 malicious programs most frequently detected by Dr.Web in email traffic in 2014 are presented in the following table:
| 1 | BackDoor.Andromeda.404 | 0.55% |
| 2 | Trojan.Redirect.197 | 0.40% |
| 3 | BackDoor.Tishop.122 | 0.35% |
| 4 | Trojan.PWS.Panda.655 | 0.34% |
| 5 | Trojan.Fraudster.778 | 0.33% |
| 6 | Trojan.Redirect.195 | 0.32% |
| 7 | Trojan.DownLoad3.32784 | 0.29% |
| 8 | Trojan.PWS.Panda.5676 | 0.29% |
| 9 | Trojan.DownLoad3.28161 | 0.26% |
| 10 | BackDoor.Andromeda.559 | 0.25% |
| 11 | Trojan.PWS.Panda.4795 | 0.24% |
| 12 | Trojan.DownLoad3.33795 | 0.23% |
| 13 | Win32.HLLM.MyDoom.54464 | 0.23% |
| 14 | Trojan.Hottrend | 0.21% |
| 15 | Trojan.Oficla.zip | 0.21% |
| 16 | Trojan.PWS.Stealer.4118 | 0.21% |
| 17 | Trojan.PWS.Panda.2401 | 0.20% |
| 18 | Trojan.Fraudster.517 | 0.19% |
| 19 | BackDoor.Comet.884 | 0.18% |
| 20 | Trojan.PWS.Multi.911 | 0.18% |
Downloader Trojans distributed with emails can turn an unprotected machine into a cesspool containing all sorts of malicious programs. And, backdoors and Trojans (such as Trojan.PWS.Panda programs which frequently appear in the above rankings) steal confidential information from user-submitted forms and also steal money during attacks on remote banking systems.
Available in Dr.Web Security Space and Dr.Web Anti-virus 10.0, the SpIDer Mail monitor provides full protection against malware spread via email. The monitor promptly detects and removes dangerous programs attached to messages and also blocks emails containing suspicious links or dangerous scripts.
Encryption ransomware
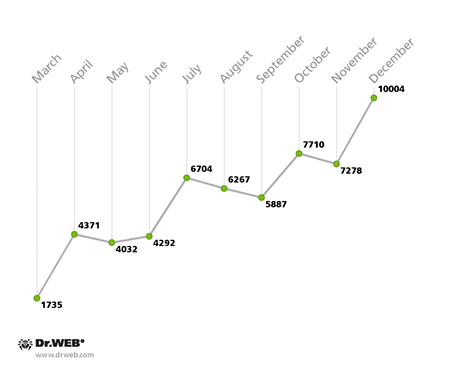
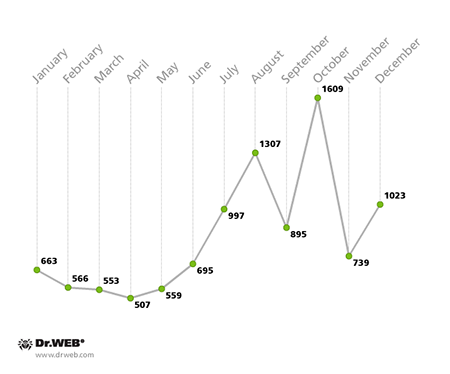
In 2014, malicious programs that encrypt data in compromised systems and demand a ransom for its decryption were one of the most common and severe threats. In the past 12 months, over 10,000 users whose data was compromised by ransomware contacted Doctor Web's technical support. Starting in July, the monthly number of such support requests increased gradually, and the August figure was twice as large as the number registered in January. The diagram below shows how the number of requests grew through 2014. The smallest number—507—was registered in April, while the largest figure—1,609—was registered in October:
The most common versions of encryption ransomware include Trojans of the BAT.Encoder family and a myriad of others: Trojan.Encoder.94, Trojan.Encoder.102, Trojan.Encoder.293, Trojan.Encoder.398, Trojan.Encoder.741 and Trojan.Encoder.567.
It should be noted that 2014 brought considerable success with regards to the development of countermeasures against programs of this sort. Doctor Web was able to create routines for decrypting files affected by some members of this malware family. For example, in July users gained the opportunity to decrypt files compromised by Trojan.Encoder.293. Discovered in September 2013, this program is a later modification of malicious programs of the Trojan.Encoder.102. family. These Trojans perform two-tier file encryption using XOR and RSA ciphers. Once files stored on the hard drive of a compromised machine have been encrypted, the Trojan demands a ransom for their decryption. It is also noteworthy that the criminals behind this Trojan use different contact email addresses.
Later, in November 2014, Doctor Web researchers determined how to recover files compromised by Trojan.Encoder.398 (restoring data affected by this malware had previously been considered impossible). Trojan.Encoder.398 is written in Delphi and appears to be an improved version of the malware program Trojan.Encoder.225. Trojan.Encoder.398 acquires encryption keys from a malicious server. The criminals typically use the following email addresses for communication: mrcrtools@aol.com, back_files@aol.com, backyourfile@aol.com, vernut2014@qq.com, yourfiles2014@yahoo.com, restorefiles2014@yahoo.fr, filescrypt2014@foxmail.com and some others.
A research study conducted by Doctor Web to create an effective decryption routine resulted in the ability to restore corrupted data. These efforts paid off: by the time Doctor Web came up with its decryption routine, it was the only company whose experts were able to recover—with a 90% success rate—files encrypted by Trojan.Encoder.398. The criminals subsequently changed the encryption routine, so that figure has declined slightly. However, Doctor Web is continuing its research on encryption ransomware and how to effectively neutralise it.
The above information shows that encryption ransomware poses a severe threat to data, and the number of infections involving these malicious programs is on the rise. And this trend is expected to persist in 2015.
If your files have been compromised by this malware, follow these steps:
- Notify the police;
- Never attempt to solve the problem by reinstalling the operating system;
- Do not delete any files from the hard drives;
- Do not try to restore the encrypted data on your own;
- Contact Doctor Web technical support at https://support.drweb.com/new/free_unlocker/?keyno=&for_decode=1&lng=en (this service is available to users who purchased commercial licenses for Dr.Web software);
- Attach a .DOC file encrypted by the Trojan to the ticket;
- Wait for a response from a virus analyst. Due to the large volume of requests, it may take some time to receive a response.
By performing timely backups and placing reasonable restrictions on user privileges, and by using a state-of-the-art anti-virus equipped with routines that neutralise such threats, PC owners can protect their data from encryption ransomware. Dr.Web Security Space 10.0, which incorporates special proactive data-protection features, is up to the job. To keep your data safe, follow the recommendations below:
1. Make sure that in the anti-virus settings you toggle on the preventive protection which protects your PC against threats yet unknown to Dr.Web.
2. Go to the ‘Tools’ menu to turn on ‘Data loss prevention’ and configure the parameters of the backup storage containing your important files.
3. Create a custom schedule to back up your valuable data.
Botnets
Over the course of the past year, Doctor Web security researchers carefully observed several botnets. In doing so, they noticed that the monthly activity of a zombie network comprised of two subnets, encompassing personal computers infected with the file infector Win32.Rmnet.12, was gradually changing, and, by year’s end, it had gotten noticeably bigger. The virus consists of several modules and can embed content into loaded web pages, redirect a browser to a site specified by criminals, and send user-entered information from web forms to remote hosts. Win32.Rmnet also steals passwords stored by popular FTP clients, such as Ghisler, WS FTP, CuteFTP, FlashFXP, FileZilla, and Bullet Proof FTP. In addition, this malicious program runs an FTP server on the machine it has infected. Another Win32.Rmnet.12 component is able to execute commands received from a remote command center and transfer the information it gathers in the infected system to criminals. This file infector can replicate itself by infecting executable files and spreads with the help of VBScript code embedded in web pages.
The activity of the Win32.Rmnet.12 botnet is illustrated in the graphs below:
Average Win32.Rmnet.12 infected host activity in 2014
(1st subnet)
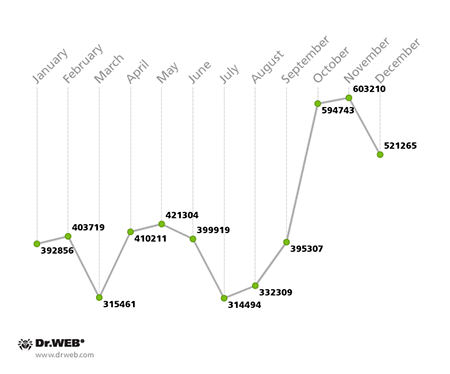
Average Win32.Rmnet.12 infected host activity in 2014
(2nd subnet)
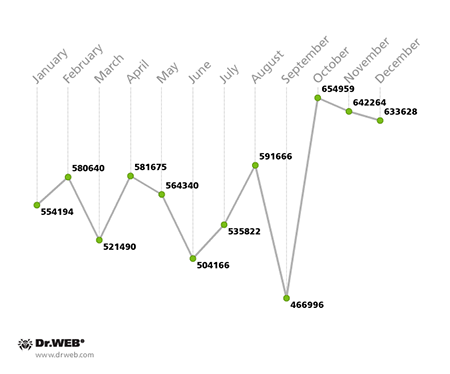
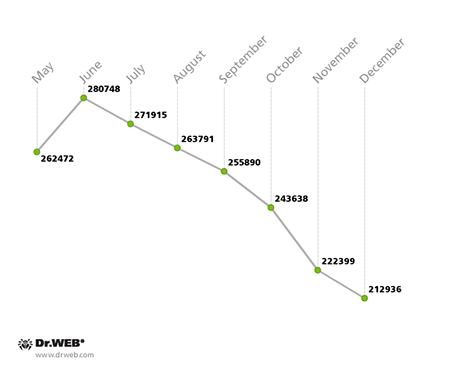
Another botnet closely monitored by Doctor Web since May 2014 was created with the polymorphic file infector Win32.Sector which was discovered in 2008. This malware can replicate itself (without user intervention) and infect files. Its main function is to download various executables via P2P networks and run them on infected machines. This malicious program can inject its code into running processes, terminate certain anti-viruses and block access to the sites of their respective developers. Doctor Web security researchers assessed this botnet’s activity and size—its activity intensified steadily in early 2014 and started to decline in July. This trend is demonstrated in the diagram below:
Average Win32.Sector infected host activity in 2014
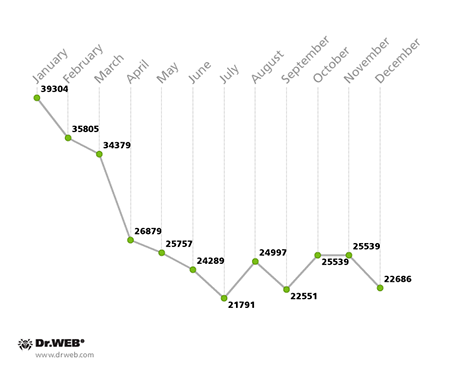
The botnet comprised of machines running Mac OS X and infected with BackDoor.Flashback.39 is slowly decreasing in size too. If, at the beginning of the year, this botnet experienced the activity of 39,304 compromised hosts, by December that number dropped to an average of 22,686. Through the year, the overall number of BackDoor.Flashback.39 bots declined by 42%.
Average BackDoor.Flashback.39 infected host activity in 2014
Linux threats
The past year proved to be rather fruitful in terms of new Linux malware programs. Chinese virus makers were especially active in this regard and crafted a significant amount of new Trojans for Linux that are designed to mount DDoS attacks.
Compared with previous months, in April and May 2014 Doctor Web security experts researched a record-high number of these Linux Trojans. They include Linux.DDoS.3 which can mount TCP flood, UDP flood and DNS Amplification attacks. Another modification of the threat, dubbed Linux.DDoS.22, targets Linux ARM distributions, while Linux.DDoS.24 can infect servers and desktops running 32-bit versions of Ubuntu and CentOS. The Linux.DnsAmp family includes several species: Some of them make use of two command and control (C&C) servers and can infect 32-bit Linux versions (Linux.DnsAmp.1, Linux.DnsAmp.3, Linux.DnsAmp.5), as well as 64-bit Linux versions (Linux.DnsAmp.2, Linux.DnsAmp.4). These malicious applications have a rather extensive payload with which they can organise different types of DDoS attacks when commanded to do so by their C&C server.
The Trojans Linux.DnsAmp.3 (for 32-bit versions of Linux) and Linux.DnsAmp.4 (for 64-bit Linux distributions) are modifications of the first version of Linux.DnsAmp which had a limited set of features. Here, we also need to mention a malicious program for ARM-compatible Linux distributions that was named Linux.Mrblack. This Trojan is also designed to perform DDoS attacks via TCP/IP and HTTP.
Malicious programs of another family known as Linux.BackDoor.Gates incorporate both backdoor and DDoS attack features. This program targets 32-bit Linux distributions, and some of its properties allow us to conclude that the malware has been designed by the same criminals who crafted Linux.DnsAmp and Linux.DDoS.
Another DDoS Trojan, which was given the name Linux.BackDoor.Fgt.1, was examined by Doctor Web in November 2014. This application spreads itself using an unusual routine: The backdoor incorporates a special routine to scan 256 random IP addresses in one loop. The scan cycle is initiated by the attackers. While generating IP addresses, Linux.BackDoor.Fgt.1 checks whether they fall within the address range used within the LAN—these addresses are ignored. If a connection is established, the malicious program tries to connect to a remote host port via Telnet and stands by for a login prompt. After sending a login from its generated list to the remote host, Linux.BackDoor.Fgt.1 begins to analyse the remote machine’s responses. If any of them contains a password request, the backdoor tries to log in by providing passwords found on its list. If successful, it commands the attacked host to download a special script. The script is used to download and launch Linux.BackDoor.Fgt.1 on the compromised machine. It is noteworthy that the C&C server stores a large number of Linux.BackDoor.Fgt.1 executable files compiled for different Linux versions and distributions, including MIPS and SPARC server ports. Thus, the backdoor can infect not only Internet-connected servers and PCs running Linux, but also other devices, such as routers.
In other words, during the year the Dr.Web virus database received a significant number of new entries for Linux Trojan families, and that number can justifiably be considered a record-high. They include families of Trojans designed to carry out DDoS attacks: Linux.DnsAmp, Linux.BackDoor.Gates, Linux.Mrblack (for ARM), Linux.Myk and Linux.DDoS. New Linux backdoors are organised into the following families: Linux.BackDoor.CNGame, Linux.BackDoor.BossaBot, Linux.BackDoor.Fgt, Linux.BackDoor.WopBot, and the web-server backdoor Linux.Roopre. Also discovered was a Linux worm belonging to the family Linux.Themoon. In 2014, an entry for a Linux rootkit was also entered into the Dr.Web virus databases—this program was dubbed Linux.Azazel. In addition, criminals designed several Trojans to mine cryptocurrencies—these are Linux.BtcMine and Linux.CpuMiner. Finally, during the past year, complex Linux Trojans were identified and registered in the virus databases. They include Linux.BackDoor.Fysbis (Sednit), Linux.BackDoor.Turla and Linux.BackDoor.Finfisher.
The number of samples of malware for Linux acquired by Doctor Web's virus laboratory in 2014
A significant increase in the quantity of malware for Linux was one of the most obvious and notable trends of 2014. The attackers' main objective is to orchestrate mass-scale DDoS attacks via infected devices. Dr.Web for Linux reliably protects machines from this kind of malware.
Threats to Mac OS X
In the past year, Mac OS X didn't escape the attention of virus-makers either. As early as February 2014, Doctor Web security researchers discovered the program Trojan.CoinThief which is designed to steal bitcoins from machines manufactured by Apple. Trojan.CoinThief infects hosts running Mac OS X, and its first samples were found in the wild in autumn 2013 when the bitcoin exchange rate was growing rapidly. The program is disguised as a legitimate bitcoin mining application, such as BitVanity, StealthBit, Bitcoin Ticker TTM, and Litecoin Ticker.
With the help of another malicious program, Mac.BackDoor.iWorm, attackers created a botnet that, as of September 2014, included 18,519 unique IP addresses of infected Macs. This program lets attackers execute an extensive set of commands on an infected Mac. The directives can be divided into two types: various instructions that depend on binary data received and Lua scripts. Statistics gathered by Doctor Web show that the largest number of infected Mac IP addresses (26.1% of the total) reside in the USA; Canada ranks second with 7%; followed by Great Britain with 6.9%.
On top of that, a number of new backdoors for Mac OS X were also discovered in 2014. They include Mac.BackDoor.WireLurker, Mac.BackDoor.XSLCmd, Mac.BackDoor.Ventir, BackDoor.LaoShu and BackDoor.DaVinci (although the latest backdoor on the list has been known since 2013, a number of new versions of it appeared in 2014). The advertising Trojans for Mac OS X — Trojan.Genieo, Trojan.Vsearch and Trojan.Conduit — were also registered in the virus database.
The number of malware samples for Mac OS X received by Doctor Web in 2014 is illustrated in the figure below:
The number of malware samples for Mac OS X acquired by Doctor Web's virus laboratory in 2014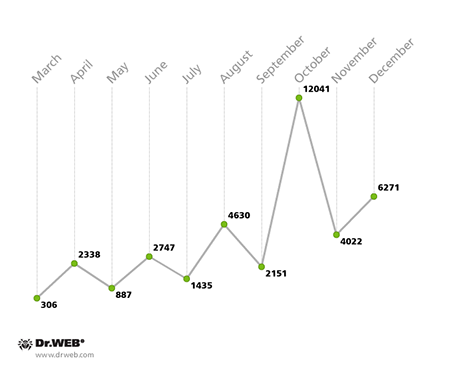
Dr.Web Anti-virus for Mac OS X 10.0 protects Apple machines from all sorts of threats. The anti-virus now includes the HTTP monitor SpIDer Gate which scans HTTP traffic and controls Internet access. With SpIDer Gate HTTP monitor, Dr.Web for Mac OS X scans all traffic on all ports in real time, intercepts all HTTP connections, and provides protection against phishing and dubious websites of all kinds. It provides additional protection when users download malware onto their Macs. In addition, SpIDer Gate can restrict Internet access according to a blacklist of non-recommended sites.
Internet fraud
In 2014, online scammers kept seeking new ways to take advantage of unsuspecting users. Dr.Web Security Space can address these threats with its SpIDer Gate and Parental Control whose databases receive an average of 2,000 to 6,000 new links to fraudulent, suspicious, or objectionable sites every day.
Criminals often prey on people looking for quick fixes for their financial issues; so-called “binary options” were particularly popular in the past year. Fraudsters advertise certain websites—mainly through spam mailings—that address the user ostensibly on behalf of a successful businessman who has earned millions on the Internet in a matter of days or on behalf of a blogger who has found a new way to make money.
These sites always tell you a story about a “unique” trading technique involving “binary options”. According to fraudsters, “binary options” pay out if the price of an asset (currency, precious metals, stocks, etc) increases or goes down. If you guess which way it will go correctly, your initial amount will increase by a percentage; if not, you lose the bet.
To organise the trading process, fraudsters develop special sites where bots allegedly accept bets, but, in truth, no connection exists between these sites and international currency markets or stock exchanges. Instead users are “playing” with a local bot running on a server. If a victim of such fraud attempts to withdraw their money, they will face overwhelming difficulties that ultimately make this task impossible.
Another popular scam, by no means a new one, gained popularity during the Sochi Olympics. Here criminals also attempted to cash in on a get-rich-quick mentality. Enterprising criminals designed sites specifically for this category of user to offer them reliable and credible information about negotiated contests whose outcomes are supposedly already known. Network swindlers claim that this information can be used to make bets that result in a multi-million-dollar payout within weeks!
These happiness merchants offer their victims the chance to purchase information about the outcome of a contest or to pay for a subscription to receive this type of data on a regular basis. The service fee seldom exceeds 150 dollars. To put users off guard, sites like these often display screenshots showing winning bets and glowing feedback from fortunate clients—all fake, of course.
In reality, in the best case scenario, a victim will get a professional sports analyst’s prediction that is already in the public domain. In other words, scammers sell predictions that are already established facts, and there is no guarantee that users will win. Sometimes, the swindlers offer a refund if their prediction proves to be false, but they still earn a profit because some users are provided with one outcome while others are given the exact opposite. Even if a user loses, they can have a hard time getting their money back: Instead of money, the indignant customer is usually offered another prediction for free.
Fans of multiplayer games also often become fraud targets. Many modern games cast players into virtual worlds that are complete with their own traditions, history, and culture. They even have their own economic models that enable players to buy and sell objects and even characters that have been upgraded to a certain level.
When acquiring an account on a game server, a buyer wants to get not just the character with the maximum number of different "skills" and experience points, but also game items such as armour and mounts (sometimes quite rare ones), as well as the set of skills and professions that are available for this character. Here the risk for the buyer lies in the fact that the fraudsters who sold them the account can get that account back as soon as the buyer (the current owner) makes their first support request. If the administration overseeing the game discovers that the account had been sold in violation of the rules, it will be blocked.
So, a potential buyer has a good chance of ending up with a stolen account that was hijacked earlier from another user. Criminals can also use chat to distribute phishing URLs, e.g., they can publish a fake announcement about a promo on offer from a game developer that requires participants to sign in to a third-party website with their game login and password or the criminals can offer them malware in the guise of a program that will help them enhance their characters' attributes.
Parental Control, which is available in Dr.Web Security Space 10.0, can protect users from various Internet scams. The Parental Control component lets you limit Internet access to websites related to a certain topic, and filter suspicious content. And, using its database of non-recommended URLs, the component can shield users from fraudulent sites, potentially dangerous and shocking content, and from sites which are known to distribute malware.
Attacks on mobile devices
The past year will also be remembered for the number of attacks of every possible kind that were made on handhelds. As before, smartphones and tablets running Android were the primary targets. Throughout the year, the Dr.Web virus database received a large number of entries for all kinds of malicious and unwanted programs for Android, and by the end of 2014, it contained 5,681 entries (up 102% compared with 2013).
Growth in the number of entries for malicious, unwanted and potentially dangerous programs for Android in 2010-2014.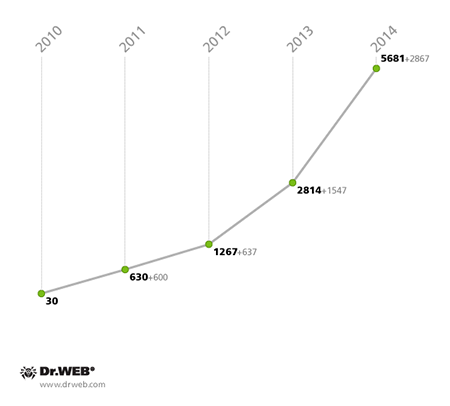
Once again, the virus writers behind the malicious software for Android devices were driven by their main goal of extracting maximum profits. To this end, they once again employed time-tested fraudulent schemes involving sending SMS messages to premium numbers and signing up users to chargeable content services. Android.SmsSend programs—the oldest and most common malicious applications for Android—played a key role in helping these criminals. By the end of the year, the Dr.Web virus database included 2,689 entries for these Trojans; at the same point in 2013, the figure was almost half that and constituted 1,377 definitions.
Android.SmsSend malware in the Dr.Web virus database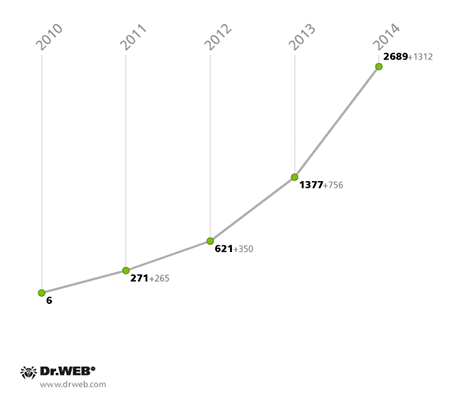
However, old-school SMS malware is not the only tool at criminals' disposal. In 2014, the range of malicious applications that generate profit by sending SMS messages to premium numbers expanded considerably. For example, the number of Android.SmsBot family Trojans increased significantly. These are capable of not only subscribing users to paid services, but also performing many other undesirable attacker-initiated actions on infected mobile devices. In addition, virus makers acquired some more “assistants” in the form of Trojans of the Android.Bodkel malware family. These programs also send SMS messages to premium numbers, and what is most interesting about them is that they threaten device owners with permanent data loss whenever they try to remove them, although in reality, these threats are empty.
Apart from sending premium messages, cybercriminals have other sources of illicit gain—stealing confidential financial information and employing banking Trojans to covertly transfer data from bank accounts associated with infected devices. Once a smartphone or tablet gets infected, the malicious applications on them not only lure users into divulging bank account access credentials but also drain the users’ accounts when they use online banking. In 2014, the number of attacks involving banking Trojans increased notably, and the geography of the incidents involving malware of this sort expanded. For example, the programs Android.BankBot.33.origin and Android.BankBot.34.origin targeted devices in Russia and could automatically transfer funds to attacker accounts. To do so, they sent an SMS query to a bank’s online banking department and attempted to retrieve information about available banking cards and available funds. If the malware got a positive reply, it used special SMS commands to transfer money to the criminals' account and concealed all the inbound notifications from the bank. In some cases, these Trojans would steal a variety of personal information about users, such as their phone numbers and email account passwords.
 |
 |
 |
Criminals made heavy use of banking Trojans in South Korea. Many of the malicious programs infesting handhelds in this country in 2014 were spread via unwanted SMS messages containing Trojan download links. Over the past 12 months, Doctor Web recorded over 1,760 such spam campaigns, each of which could hit from several hundred devices to tens of thousands of them.
The number of spam campaigns orchestrated in 2014 to distribute Android Trojans in South Korea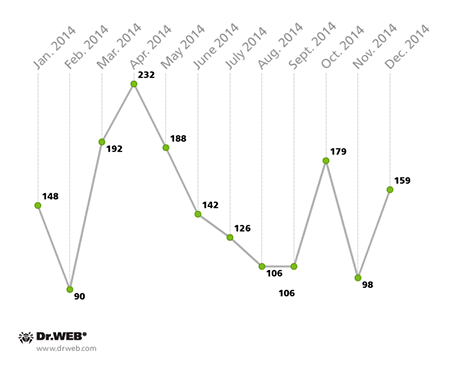
Many of the Trojans discovered in 2014 in South Korea have a rather extensive payload and incorporate state-of-the-art design. For example, Android.Banker.28.origin stole valuable banking information by mimicking banking applications and, more radically, by deleting programs of this sort and replacing them with counterfeit copies. Also, a large portion of South Korean Trojans used various protective features. These include all kinds of packers, code obfuscation, incorporating Trojans into other applications, and the ability to remove anti-viruses.
 |
 |
 |
Here we must mention the Trojan Android.Wormle.1.origin which became bona fide international malware. In November 2014, Android.Wormle.1.origin infected over 15,000 Android handhelds in about 30 countries including Russia, Ukraine, the USA, Belarus, Uzbekistan, Kazakhstan, Tajikistan and China. When commanded by attackers, the Trojan not only covertly transferred money from the victim's credit card, but also was capable of performing a variety of other harmful tasks. For example, it could send SMS messages, delete installed programs and files, steal a variety of confidential information, and even carry out DDoS attacks on websites. In addition,Android.Wormle.1.origin could spread with the help of SMS messages containing its download link.
The number of devices infected by Android.Wormle.1.origin in November 2014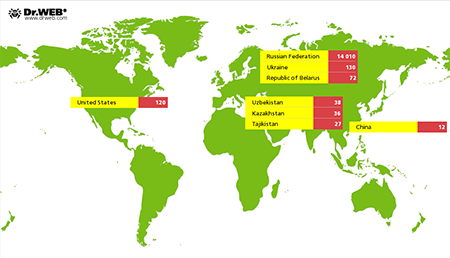
The past year also saw the emergence of brand new Trojans for Android that helped criminals take advantage of users. These program included ransomware blockers—their desktop editions are still quite a nuisance. The emergence of the mobile versions was something to be expected. With the huge Android software and hardware market and the simplicity of ransomware design, what other encouragements did criminals need? The first programs of this sort were discovered in May 2014, and one of them proved to be rather dangerous. Dubbed Android.Locker.2.origin by Doctor Web, it didn't just block access to infected devices; it also encrypted practically all data of value including images, music, documents and videos. In effect, Android.Locker.2.origin became the first-ever encryption ransomware for Android.
Luckily, other ransomware examples found in 2014 weren't so vicious and merely blocked the screen and demanded a ransom. However, in most cases, users were left with smartphones or tablets that were completely useless because Android.Locker programs prevented them from closing the ransomware window, running other programs, and opening system settings.
Some of these Trojan horses have even more dangerous features. For example, Android.Locker.38.origin (discovered in September 2014) not only locked smartphones and tablets to demand a ransom, but also could set an unlock password which further complicated its removal.
Less than eight months after Android.Locker programs appeared, the number of ransomware programs for Android increased significantly, and, by the end of 2014, the Dr.Web virus database contained 137 entries for these applications.
Mining Trojans, which are designed to extract various electronic cryptocurrencies, were another type of malware crafted by criminals last year in order to take advantage of Android users. For example, Android.CoinMine.1.origin and Android.CoinMine.2.origin, which were spread in popular applications modified by criminals, were discovered in March. These programs were distinguished by the fact that they would only become active if the user remained inactive in the system for a long period of time. Since the Trojans utilised the hardware resources of the smartphones and tablets, they could affect the overall performance of the devices and even render them non-operational.
 |
 |
 |
A bit later, virus makers released improved versions of the malware. Unlike the original malicious programs, the upgraded versions didn't exhaust all the hardware resources. Nonetheless, the compromised devices would still operate to the benefit of the intruders.
In summary, the past year showed that cybercriminals not only sustained their interest in getting money from Android users but also significantly intensified their attacks, hoping to swindle users out of even more money. In this regard, owners of Android smartphones and tablets should exercise caution when it comes to installing applications and, if in doubt, refrain from using suspicious programs. It is also recommended that all users without exception install anti-virus software and, if engaged in mobile banking, maintain constant control over all transactions involving their accounts and bank cards.
Stealing confidential information is another lucrative illicit business that once again became a pressing issue for Android users in 2014. Virus makers produced a myriad of diverse spying Trojans, and attacks involving programs of this type were registered all over the world. For example, Android.Spy.67.origin, which was discovered in January in China, collected confidential information including SMS messages, the call history, and GPS data and forwarded it to a remote server. In addition, the malware could activate mobile device cameras and microphones; it could also index images and create special thumbnails of them. Android.Spy.67.origin had another peculiar feature: If this malware gained root access, it would disrupt the operation of popular Chinese anti-viruses, remove their virus databases, and install a malicious program that could, in turn, covertly install other applications. In the spring, Android.Dendroid.1.origin went up for sale on underground hacker forums. This program could be embedded into any harmless Android application and allowed criminals from all over the world to perform a number of illegal actions on infected mobile devices. Specifically, Android.Dendroid.1.origin could intercept phone calls and SMS messages, acquire information on the device’s current location, steal phone book data and browser history, activate the built-in camera and microphone, and send SMS messages. Also discovered in 2014 were rather unusual Trojans that did not merely steal information but also executed commands from intruders and carried out many other types of malicious activities. As an example, in March South Korean virus writers created the backdoor program Android.Backdoor.53.origin. It was based on a legitimate program for the remote administration of mobile devices. When launched, the Trojan would delete its shortcut from the home screen to hide its presence in the system and connect to a remote host to allow attackers full access to the infected device. Android.Backdoor.96.origin, which was discovered in August, is another no less interesting backdoor. This program stole all sorts of confidential information including SMS data, call and browsing history, GPS data and contact information. Android.Backdoor.96.origin could also display various messages on the device's screen, send USSD queries, toggle on the device's microphone, record phone calls, and upload the gathered information to a remote server.
However, the malware program Android.SpyHK.1.origin, which was spread in Hong Kong, was one of the most remarkable spying Trojans of 2014. Once launched, it sent some general information about the infected mobile device to a remote server and awaited further instructions from its makers. Those instructions included eavesdropping on phone calls, stealing SMS messages, determining the device's location, uploading files stored on the memory card to a server, activating voice recording, and acquiring the browsing history and contact information.
The rich diversity of spy Trojans for Android discovered in 2014 proves once again that Android-powered devices serve as an excellent source of valuable information for cybercriminals. Therefore, users should always factor in the risk that their confidential information can be stolen and never expect that some segment of their data won’t be of interest to cybercriminals. Even if you regard a piece of information as insignificant, that doesn't mean that criminals won't find a way to use it to their advantage.
Pre-installed malicious programs or those that have been embedded into firmware became another severe threat to Android users. Over the past 12 months, a large number of such incidents were registered, the most striking one involving the emergence of the first-ever Android bootkit. That bootkit, the Trojan Android.Oldboot.1, was discovered in January on a large number of mobile devices. It was located on a hidden partition and got a jumpstart on the Android OS whenever a smartphone or tablet infected with the Trojan was turned on. When launched, Android.Oldboot.1 extracted several components, put them in the system folders, and installed them as ordinary applications. These malicious objects then connected to a remote server and could perform unwanted, criminal-initiated actions. In most cases, the bootkit covertly downloaded, installed and removed various programs.
In February, Doctor Web security researchers discovered two malicious programs in Android firmware installed on inexpensive Chinese-made devices. The programs’ main purpose was to pay the usage fee on a Chinese music portal. Dubbed Android.SmsSend.1081.origin and Android.SmsSend.1067.origin, these programs covertly sent special short messages for which subscribers would be charged around 10 US cents. Also in November, Android.Becu.1.origin was found pre-installed on a significant portion of low-cost Android handhelds. This program featured modular architecture and could be used by criminals to install other unwanted programs onto compromised devices.
Similar programs were discovered in December too. One of them, Android.Backdoor.126.origin enabled criminals to implement various kinds of fraud and could add short messages with arbitrary content into the SMS inbox. Dubbed Android.Backdoor.130.origin, another malicious program could—without the knowledge or consent of the device's owner—send text messages; make calls; display advertisements; download, install and run applications; and send various bits of confidential information, including the call history, SMS messages and data on the mobile device’s location, to a remote server.
Thus, it is completely clear that compliance with the basic security rules for Android devices, which includes installing software only from trusted sources and using anti-virus software, is no longer enough. Special attention also needs to be paid when choosing a device. Make sure especially that the device was produced by a reliable manufacturer and that the vendor selling the device is reputable. In addition, you should avoid using dubious Android builds and refrain from downloading firmware from untrusted sources.
Dr.Web for Android incorporates an arsenal of features to keep state-of-the-art smartphones, tablets, and other handhelds secure.
Although the majority of the attacks targeted Android device users, smartphones and tablets running iOS also came under fire. It is worth noting, though, that the majority of malware for iOS could only infect jailbroken devices; however, there was a Trojan horse that could infect handhelds running unaltered iOS. IPhoneOS.Spad.1 was discovered in March and targeted devices in China. This malware would make specific modifications to advertising modules embedded in various iOS applications. As a result, the profit generated by the advertisement went to an account belonging to the enterprising hackers rather than the authors of those programs. Discovered in April, IPhoneOS.PWS.Stealer.1 stole Apple IDs. IPhoneOS.PWS.Stealer.2, discovered in May, stole Apple IDs, but it could also buy software in the App Store at the user's expense as well as download and install purchased programs. Detected in September, the Trojan program IPhoneOS.Xsser.1 posed a rather severe threat. It could obey commands to steal such confidential information as the contents of the phone book, photos, passwords, SMS messages, the call history, and the device location. And in December, the integrity of personal information on jailbroken devices was threatened by the dangerous Trojan IPhoneOS.Cloudatlas.1 which was designed to collect a wide range of sensitive data. However, IPhoneOS.BackDoor.WireLurker was 2014’s most dangerous Trojan for iOS users. This program could be installed on jailbroken handhelds as well as on smartphones and tablets whose operating systems remained intact. To accomplish this, virus writers were aided by a desktop relative of the malware. Mac.BackDoor.WireLurker.1, in particular, was spread by hackers in pirated versions of legitimate programs and infected computers running Mac OS X. It monitored USB connections for target mobile devices and used a special "corporate" digital certificate to install IPhoneOS.BackDoor.WireLurker onto connected mobile devices. Once IPhoneOS.BackDoor.WireLurker was successfully deployed on an iOS handheld, it could steal confidential information, including contact information and SMS messages, which was then relayed to a server controlled by the intruders.
Attacks on Apple smartphones and tablets in 2014 give users a clear signal that the danger is real, and crafty intruders will do their best to take advantage of iPhone and iPad users. Doctor Web recommends that Apple fans pay special attention to applications they install (including those installed onto Apple desktops and laptops), avoid dubious websites, and refrain from opening links found in suspicious short messages.
Prospects and likely trends
Based on an analysis of the situation in 2014, we can assume that encryption ransomware will persist, its diversity will increase, and the technologies and designs employed by criminals will be further perfected and upgraded.
We should also expect new malicious programs for Linux and Mac OS X. New banking Trojans as well as more sophisticated malware engaged in data theft in remote banking will also surely emerge. Some of them will interact with malicious programs on handhelds.
The further development and proliferation of all sorts of gadgets—including tablet PCs, smartphones and GPS navigation devices—will result in criminals becoming even more interested in mobile platforms. Banking technologies will also certainly continue to be their focus, and 2015 is likely to witness new banking Trojans for Android. Threats involving chargeable SMS messages will definitely still be relevant, and new ransomware lockers for Android will also appear in the wild. And, it is also safe to assume that personal information stored on mobile devices will be targeted just as much as it has been in the past.
Owners of Apple handhelds should also remain vigilant in 2015. The past year showed that criminals have become increasingly interested in this platform.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live









![[VK]](http://st.drweb.com/static/new-www/social/no_radius/vkontakte.png)
![[Twitter]](http://st.drweb.com/static/new-www/social/no_radius/twitter.png)
![[facebook]](http://st.drweb.com/static/new-www/social/no_radius/facebook.png)

Tell us what you think
To ask Doctor Web’s site administration about a news item, enter @admin at the beginning of your comment. If your question is for the author of one of the comments, put @ before their names.
Other comments