Another banking Trojan targets South Korea
Real-time threat news | Hot news | Threats to mobile devices | All the news | Virus alerts
December 4, 2014
To distribute the program, criminals incorporated Android.BankBot.35.origin into another malware program that is registered in the virus database as Android.MulDrop.46.origin. This Trojan performs dropper tasks and can be downloaded in the guise of various applications. Currently, Doctor Web security researchers know about incidents of Android.MulDrop.46.origin spreading as a popular browser; however, the choice of disguise depends entirely upon the imagination of the virus makers.
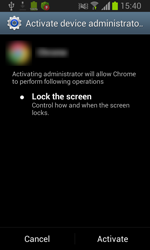
Once the dropper has been installed on an Android handheld, it can be launched by the user (when they tap on the corresponding icon) or automatically during the next screen unlock or device reboot. If a user launches Android.MulDrop.46.origin, the Trojan prompts them to grant it access to the administrative features of the mobile device, and then deletes its icon. From then on, the malware operates as a system service and becomes 'invisible' to the device's user.
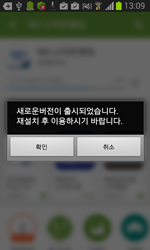
Following its successful initialisation, the dropper extracts the dex executable <44><42Android.BankBot.35.origin from its resources using the DexClassLoader routine, allowing applications (in this case, Android.MulDrop.46.origin) to load additional software modules without pre-installation or user participation. After gaining control, Android.BankBot.35.origin goes into standby mode and periodically checks whether certain online banking applications belonging to several South Korean financial organisations are present on the infected device. If any of the programs is discovered, the malware downloads the relevant fake application for it from a remote server and then attempts to replace the legitimate program with the fake one. To accomplish this, Android.BankBot.35.origin prompts the user to install a supposedly new version of the banking program. If the user consents to installing the 'update', the malware will initiate the removal of the legitimate application and, when done, will commence with installing the bogus one.
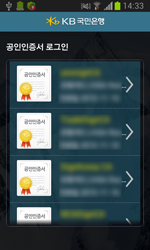
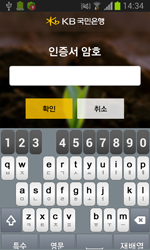
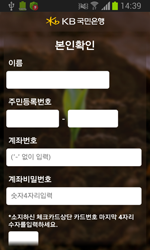
All the fake banking applications downloaded by Android.BankBot.35.origin are in fact various modifications of Android.Banker.46.origin. This malicious program gives criminals access to the bank accounts of South Korean users, which can result in unintended financial transactions and even wiped-out accounts. To steal all the sensitive information it needs, Android Banker.46.origin mimics the interface of legitimate online banking applications and prompts users to enter data such as the login and password they use to access their accounts, their account number, and credit card number, and information about the digital certificate used to secure their transactions.
 |
 |
 |
Along with replacing legitimate banking applications with bogus copies, Android.BankBot.35.origin can also perform other unwanted actions. In particular, when tasked by a command and control (C&C) server, the malware can:
- Send SMS with a specific text to a specified number.
- Enable or disable Wi-Fi.
- Upload data from the phone book (including phone numbers saved in the SIM card) to the server.
- Download a specified dex file from the remote host and run it.
To run the downloaded file, the Trojan uses the dex-related routine of Android.MulDrop.46.origin which was previously employed to initialise Android.BankBot.35.origin. Thus, this malicious program makes use of modular architecture and, depending on the needs of virus makers, can significantly expand its payload.
In addition to stealing contact information, the Trojan can also relay other sensitive information to the C&C server, such as the phone number, handheld model, OS version and type of mobile and Wi-Fi network used. In addition, Android.BankBot.35.origin can intercept and delete SMS messages from certain numbers on the Trojan's blacklist.
It is noteworthy that the malware also possesses an interesting self-defence mechanism. So, if the Trojan detects a popular South Korean anti-virus being launched on an infected device, Android.BankBot.35.origin will disrupt its initialisation and return the user to the home screen. Similarly, the Trojan blocks access to the application manager and to the feature used to assign device administrators, which is why users of compromised devices won't be able to manage their installed applications if the Trojan's self-defence mechanism has been activated. However, this protective mechanism does not work if at least one of the original banking clients hasn't yet been replaced or if the Trojan hasn't been granted administrator permissions.
To avoid infection, owners of Android handhelds should refrain from installing applications that haven't been obtained from Google Play. Doctor Web also encourages users to install reliable anti-virus software on their devices. Dr.Web Anti-virus for Android and Dr.Web Anti-virus for Android Light detect and neutralise the Trojans above, so they pose no threat to devices protected with Dr.Web.