Blocker of Windows and other virus threats of December 2009
Virus reviews | All the news
January 2, 2010
Windows blockers
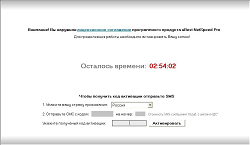
Numerous modifications of Windows blockers featuring new counter-analysis tehcnologies emerged in December. Under the Dr.Web classification such programs are named as Trojan.Winlock. In recent months these programs have become the main tool for extracting money in Russian and Ukraine.
Active Trojans of this class prevent launching of utilities used for analysis and may force a system shutdown. They also create numerous copies of themselves in Windows system folders to make manual removal of the malware from the system more difficult. The name of the Trojan process also differs from the name of the malicious executable file.
Trojans via e-mail
Spam remains one of the main channels for distribution of malware.
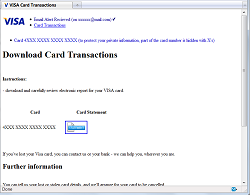
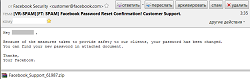
In December 2009 various modifications of Trojan.PWS.Panda were spread as VISA card transaction reports or as Facebook account passwords.
Such malicious programs as Trojan.NtRootKit.3226 and modifications of Trojan.Packed were delivered to users as “compromising photos” while Trojan.Botnetlog arrived at user machines as document from DHL.
Audio spam
December saw several types of spam mailings with attached audio files. As a rule such files are provided in the mp3 format and have a low bit rate (16 Kbit/s).
Messages with audio attachments advertised e-stores and healthcare products – an audio file contained a an address of the advertised web-site. Mailings that aimed to draw users into participating in pyramid schemes provided mp3 files larger than 6 MB with approximately sixty minutes length of a lecture.
From 2009 into 2010
In 2009 virus makers tended to focus on acquiring funds of users – an easy prey when large numbers of people follow links supposedly from credible organizations or friends, download programs serving different puporses. Criminals made money transfer demands appear in browser windows, on top of all other windows or right on a desktop. Traditional virus spreading channels — e-mail and instant messengers – were used along with new ones such as social networking web-sites and blogs.
The trend when cyber criminals target users of a wide range of operating systems and browsers simultaneously will most likely persist in 2010. In subsequent years developers of viruses will not merely focus on bypassing the conventional signature-based or heuristic detection but will be making a considerable effort in creating and refining methods to evade behaviour blockers. Examples of such evasions techniques can already be seen in the present. Most certainly rootkit technologies will continue to evolve as well and the technological contest between virus makers and anti-virus vendors will be as tough. It is also highly probable that a rootkit targeting Windows x64 will emerge in the wild in 2010. Yet makers of bogus web-sites will reach better efficiency by increasing the number of fraudulent web-resources. Even now anti-phishing technologies implemented in browsers to protect users from cyber-fraud often fail.
The number of malicious programs found in e-mail traffic in December increased 2.8 times compared to the November figures. The share of malicious files in the total number of files scanned on user machines increased 2.2 times. Cyber criminals raise the amount of money demanded from users for restoring their systems.
Viruses detected in e-mail traffic in December
01.12.2009 00:00 - 01.01.2010 00:00 | ||
| 1 | 12417046 (14.38%) | |
| 2 | 9400042 (10.89%) | |
| 3 | 6643369 (7.69%) | |
| 4 | 6574865 (7.61%) | |
| 5 | 5380941 (6.23%) | |
| 6 | 4924800 (5.70%) | |
| 7 | 3791901 (4.39%) | |
| 8 | 3555068 (4.12%) | |
| 9 | 3221976 (3.73%) | |
| 10 | 3012162 (3.49%) | |
| 11 | 2355690 (2.73%) | |
| 12 | 2135038 (2.47%) | |
| 13 | 1846800 (2.14%) | |
| 14 | 1794382 (2.08%) | |
| 15 | 1732410 (2.01%) | |
| 16 | 1717600 (1.99%) | |
| 17 | 1504800 (1.74%) | |
| 18 | 1429018 (1.66%) | |
| 19 | 1390881 (1.61%) | |
| 20 | 1301627 (1.51%) | |
| Total scanned: | 84,146,920,455 |
| Infected: | 86,343,017 (0.103%) |
Viruses detected on user machines in December
| 01.12.2009 00:00 - 01.01.2010 00:00 | ||
| 1 | 2410816 (12.69%) | |
| 2 | 1627202 (8.56%) | |
| 3 | 1297220 (6.83%) | |
| 4 | 802751 (4.23%) | |
| 5 | 647967 (3.41%) | |
| 6 | 585736 (3.08%) | |
| 7 | 525731 (2.77%) | |
| 8 | 466105 (2.45%) | |
| 9 | 399722 (2.10%) | |
| 10 | 397594 (2.09%) | |
| 11 | 374109 (1.97%) | |
| 12 | 368920 (1.94%) | |
| 13 | 311983 (1.64%) | |
| 14 | 298597 (1.57%) | |
| 15 | 295692 (1.56%) | |
| 16 | 264613 (1.39%) | |
| 17 | 230928 (1.22%) | |
| 18 | 229697 (1.21%) | |
| 19 | 218138 (1.15%) | |
| 20 | 210376 (1.11%) | |
| Total scanned: | 89,457,410,121 |
| Infected: | 18,999,657 (0.0212%) |