Anti-virus review for 2009 from Doctor Web
Virus reviews | All the news | Virus alerts
Rootkits
In 2009 authors of new rootkits provided most complex puzzles for virus analysts of Doctor Web. With their capabilities to hide from users and anti-viruses rootkits can just as well hide presence of other malicious programs they download from the Internet. A rootkit component can be registered in the database of an anti-virus and yet remain undetected.
BackDoor.Tdss rootkits (as classified by Dr.Web) were the most notable representatives of this type of malware in 2009. Doctor Web promptly released several hot scanner add-ons that incorporated updates for the Dr.Web Shield anti-rootkit module to enable the anti-virus to counter latest rootkit technologies.
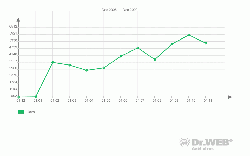
In March Doctor Web issued a news report concerning a modification of BackDoor.Tdss that disrupted operation of resident file monitors included in some anti-virus products and evaded detection by anti-rootkits. At that point the rootkit wasn't found in high numbers in the wild.
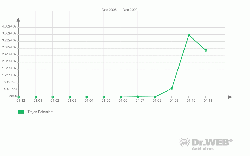
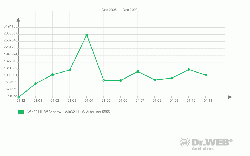
Later in November new modifications of BackDoor.Tdss spread far wider. Doctor Web’s statistics server registered 400 000 instances of detection of the malware on user machines. In previous months the figure rarely rose higher than 1 000 detections per month.
It is worth noting that later modifications of BackDoor.Tdss were enhanced with advanced hiding technologies such as a hidden virtual drive that stored some of the rootkit’s files and a sophisticated mechanism for bypassing behaviour blockers. In spite of such complications Doctor Web was able to provide its anti-viruses with the curing algorithm that enabled them to neutralize BackDoor.Tdss.
Fake anti-viruses
The late months of 2009 saw a high number of fake anti-viruses registered in Dr.Web classification as Trojan.Fakealert. Such programs have look and feel of a genuine anti-virus but serve only one purpose: to lure a victim to a bogus-web site where the user is offered to purchase a “full version”.
As a rule fake anti-viruses arrive to users as downloaders with spam messages or over fraudulent web-sites. Once launched a malicious program retrieves other components from a server of cyber criminals. In such programs the emphasis is put on the look and \feel. Applications of this type fake a Windows system information window showing that the supposed anti-virus is protecting the system while the main program window displays scanning progress and simulates detection of viruses.
Paying for a "full version" won't bring an end to the user's problems – he is not off the hook yet while the "anti-virus" can download and install other malicious programs.
Since September 2009 Doctor Web’s virus analysts had been registering a surge in activity of fake anti-viruses with tens of millions of detections in October and November. Before September the figure was four times lower.
Windows blocker
Windows blockers – programs belonging to the Trojan.Winlock family in the Dr.Web classification – brought a lot of trouble to users in 2009. As Windows starts, a blocker displays a message on top of all other windows that informs the user that his system has been blocked and the user has to unlock it with a paid SMS.
The most typical reason for blocking given to a user was a supposed detection of a non-genuine copy of Windows or of other software products. Criminals went as far as providing a windows locker construction set at a moderate price available to anyone who wanted to buy it.
Several years ago earlier versions of malware from the Trojan.Winlock family were less harmful and removed themselves automatically in several hours after installation if a user didn’t do anything, neither did they start in the Safe mode, entering a correct combination of symbols did unlock the system and the SMS charge was lower.
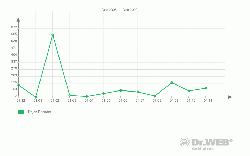
Later modifications of Trojan.Winlock turned out to be more harmful and the SMS fee rose. Some modifications didn't even feature the unlocking mechanism and therefore users paying cyber-criminals could end up with nothing. The Trojan’s data is not removed from the system automatically after a certain period of time. Malicious programs of this Trojan.Winlock have also been "taught" to block launch of many programs that might make analysis of the blocker in the infected system easier or those that shut the system down upon an attempt to start such a program.
f your system has been compromised by one of the modifications of Trojan.Winlock, do not send money to virus-makers. Instead contact the technical support of the vendor whose anti-virus you are using or ask for help on Doctor Web's forum.
Banners
Another modification of Trojans extortionists is the family of malicious programs that are installed into a system as a browser plugin. In a compromised system a Trojan displays a window that may occupy as much as 50% of the browser window. Here a user is also required to send an SMS to remove the window.
Under the Dr.Web classification The Trojans are usually detected as a modification of Trojan.Blackmailer or of Trojan.BrowseBan. While a Trojan.Blackmailer program usually works only with Internet Explorer, Trojan.BrowseBan is compatible with Mozilla Firefox and Opera. A special script embedded by cyber-criminals on a web-site spreading the malware allows detecting the victim’s browser and providing him or her with a corresponding version of the Trojan.
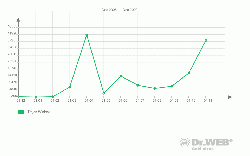
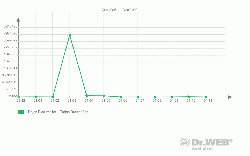
The number of such programs found in the wild surged in March 2009. About three million detections of Trojan.Blackmailer on user machines were registered while the average figure through the year stayed within 5 000 – 10 000 per month.
Document encryptors
Malicious programs that encrypted documents stored on hard drives were another problem that many users had to face in 2009. Dr.Web anti-viruses detect such programs as Trojan.Encoder modifications. Once in a system, the Trojan encrypts user documents while keeping system files in tact. Once encryption is completed, the user is notified that his documents have been encrypted and he has to transfer an amount of money onto the specified account to be able to work with his files again.
A maker of a Trojan.Encoder program went as far as to use Dr.Web corporate design on his web-site Users also received spam messages supposedly from Doctor Web’s staff members and some modifications of the extortionist program added the drweb extension to names of encrypted files. Probably such actions by the criminal were provoked by active assistance to victims of the extortion on the part of Doctor Web.
In spite of a relatively small number of such programs in the wild they inflict a considerable damage – information contained in encrypted files may be quite valuable to a user. If your data has been encrypted by a Trojan.Encoder program, you can always ask Doctor Web's virus laboratory for help. In most cases our virus analysts will be able to help you restore your data and will do it for free.
Worm
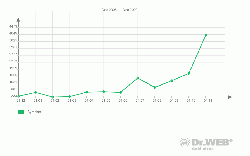
In 2009 worms forced many administrators of local networks to study IT security basics once again. Win32.HLLW.Shadow.based became the most notorious program of this kind.
Since the worm spreads over removable data storage devices and network drives showing once again that disabling autorun for such disks is among the key requirements to anti-virus security. Moreover, the worm can perform dictionary attacks using the SMB protocol inherent in all Windows networks. And finally Win32.HLLW.Shadow.based exploits several known vulnerabilities of Windows that had been closed before the worm was found in the wild.
Installing all available security updates for an operating system is another frequently neglected security essential.
The graph shows that Win32.HLLW.Shadow.based is still found in great numbers on user machines.
ntegrated development environments
It has already been mentioned that some malicious objects are capable of detecting a target operating system, web-browser and versions of popular programs installed in a system to increase their chances of a successful attack. But can virus-makers provide malicious software that would be compatible with all widely used platforms?
Analysis of statistical information about malware by different platforms provides the following conclusions. Interest of virus makers to different platforms is growing steadily. When it comes to Mac OS, Linux or Windows CE, it is not so obvious even though news of discovered malicious programs for these platforms appear on the Internet every now and then. Yet interest towards such platforms as Java or Symbian appears to be growing on monthly basis even though the share of malicious code targeting mobile platforms in the total amount of malicious traffic remains insignificant.
Doctor Web follows the developments. Dr.Web for Symbian OS currently in beta-testing will soon hit the market and will be available to all users of smart phones running the OS.
2010 forecast
The trend in the malware design when virus-makers aim to target a wider range of operating systems and browsers will mostly likely persist in 2010. Web-sites with embedded scripts for detection of a target OS and other installed software to provide a user with a corresponding version of a malicious program will also grow in number.
The operating systems market is becoming more diverse with new OS and mobile devices appearing and users taking interest in open source solutions. Consequently virus-makers will keep up with emerging trends.
In subsequent years developers of viruses will not merely focus on bypassing the conventional signature-based or heuristic detection but will be making a considerable effort in creating and refining methods to evade behaviour blockers which can already be observed in the present.
Most certainly rootkit technologies will continue to evolve as well and the technological contest between virus makers and anti-virus vendors will be as tough. It is also highly probable that a rootkit targeting Windows x64 will emerge in the wild in 2010. Many experts believe that it is only a matter of time. A wider application of polymorphic technologies as a countermeasure against cloud anti-viruses is also something to be expected. If a number of unique viruses will constitute a significant share of malicious traffic, efficiency of such anti-virus solutions will be rather low.
Makers of bogus web-sites will reach better efficiency by increasing the number of fraudulent web-resources. Even now anti-phishing technologies implemented in browsers to protect users from cyber-fraud often fail. A number of similar phishing sites can be so huge that ant-phishing watch groups are simply unable to register all addresses in time.
At the end of the review Doctor Web offers you some advice on how to reduce the infection risk. First of all it is recommended to establish a multi-layer security system.
Configure automatic updating of the OS and other applications you use to ensure that malicious programs won’t take advantage of vulnerabilities that have not been closed. Set your anti-virus to update automatically so it would be able to detect latest threats. Remove permissions to perform the general system configuration for the user account used to work in the Internet. It is also highly recommended to disable autorun for removable data storage devices.
Apart from the quite obvious recommendation for businesses to use corporate anti-virus solutions it is also a good idea to establish a security policy and utilize at least a small part of the working time of employees to teach them security basics.
Please, remember that users of Dr.Web software can always contact the technical support service of Doctor Web if a suspicious activity is detected in the system.
Viruses detected in e-mail traffic in 2009
| 01.12.2008 00:00 - 01.12.2009 00:00 | ||
| 1 | Win32.HLLM.Netsky.35328 | 45817344 (16.28%) |
| 2 | Trojan.DownLoad.47256 | 25287535 (8.99%) |
| 3 | Win32.HLLM.Beagle | 22187775 (7.88%) |
| 4 | Trojan.DownLoad.36339 | 15808084 (5.62%) |
| 5 | Trojan.Fakealert.5115 | 15588235 (5.54%) |
| 6 | Trojan.DownLoad.37236 | 12785630 (4.54%) |
| 7 | Win32.HLLM.MyDoom.33808 | 12283970 (4.37%) |
| 8 | Trojan.Fakealert.5238 | 10516195 (3.74%) |
| 9 | Trojan.Packed.683 | 6970575 (2.48%) |
| 10 | Trojan.MulDrop.40896 | 6932828 (2.46%) |
| 11 | Trojan.PWS.Panda.122 | 6591442 (2.34%) |
| 12 | Win32.HLLM.MyDoom.based | 6563953 (2.33%) |
| 13 | Trojan.DownLoad.50246 | 5684473 (2.02%) |
| 14 | Win32.HLLM.MyDoom.44 | 4988808 (1.77%) |
| 15 | Trojan.Botnetlog.9 | 4958443 (1.76%) |
| 16 | Trojan.Packed.2915 | 4722719 (1.68%) |
| 17 | Trojan.MulDrop.19648 | 4612563 (1.64%) |
| 18 | Win32.HLLM.Netsky.based | 4578015 (1.63%) |
| 19 | Trojan.Fakealert.5825 | 4529188 (1.61%) |
| 20 | Trojan.Fakealert.5356 | 4051498 (1.44%) |
| Total scanned: | 768,599,094,754 |
| Infected: | 281,404,910 (0.04%) |
Viruses detected on user machines in 2009
| 01.12.2008 00:00 - 01.12.2009 00:00 | ||
| 1 | Trojan.DownLoad.47256 | 15123101 (6.72%) |
| 2 | Win32.HLLW.Gavir.ini | 13451665 (5.97%) |
| 3 | Win32.HLLW.Shadow.based | 8168356 (3.63%) |
| 4 | Win32.HLLM.Beagle | 7552860 (3.35%) |
| 5 | Trojan.Fakealert.5115 | 7111405 (3.16%) |
| 6 | Trojan.DownLoad.36339 | 6896609 (3.06%) |
| 7 | Win32.HLLM.Generic.440 | 6139494 (2.73%) |
| 8 | Trojan.Fakealert.5238 | 5705545 (2.53%) |
| 9 | DDoS.Kardraw | 5234473 (2.32%) |
| 10 | Win32.HLLM.Netsky.35328 | 4756893 (2.11%) |
| 11 | JS.Nimda | 4476017 (1.99%) |
| 12 | Win32.Virut.14 | 4199541 (1.87%) |
| 13 | Trojan.MulDrop.16727 | 3682581 (1.64%) |
| 14 | Trojan.Botnetlog.9 | 3350630 (1.49%) |
| 15 | Win32.Virut.5 | 3268197 (1.45%) |
| 16 | Win32.HLLW.Autoruner.5555 | 3234720 (1.44%) |
| 17 | W97M.Thus | 3202955 (1.42%) |
| 18 | Win32.Alman | 3025843 (1.34%) |
| 19 | Win32.Sector.17 | 2966478 (1.32%) |
| 20 | Win32.HLLM.MyDoom.49 | 2907279 (1.29%) |
| Total scanned: | 2,289,643,009,454 |
| Infected: | 225,141,202 (0.01%) |