May virus review by Doctor Web released
Virus reviews | All the news
June 1, 2007
May'07 virus and spam review by Doctor Web, Ltd.
Virus Monitoring Service of Doctor Web, Ltd. reports on virus events in May 2007.
May 2007 virus environment took over the strain it survived the previous month. Win32.HLLM.Limar in various modifications remained the prime trouble-maker. It accounted from 30 up to 70% of the infected traffic starting from the midst of May. As the scheme below proves hardly ever a month had escaped sudden outbreaks caused by its modifications.
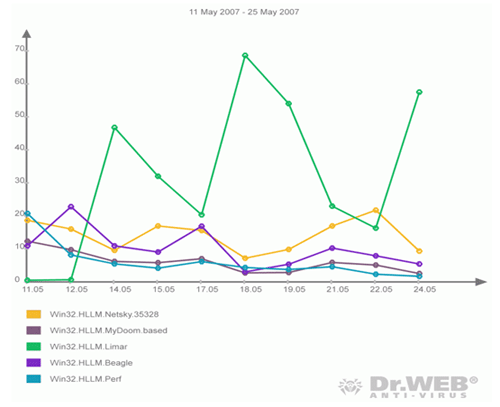
Another event to be noted is new modifications of Win32.HLLM.Graz, disseminated via spam in attached *.hta files of different kind which made it even more difficult to detect the infection. However, both the former and the current versions of this mail worm run the same way: they install a rootkit component to hide the worm’s files on the disk and in the log files of the infected system.
Malware of Asian origin in numerous modifications of Win32.HLLW.Gavir, Win32.HLLP.Whboy, Win32.HLLW.Cent, Win32.HLLW.Autoruner and Win32.HLLW.Creater made a triumphal go, too. They all uniquely auto-start every time Windows is started, with copies of the malware and the autorun.inf file with the rout to the malware carrier created in the Windows directory. Both malware copies and the autorun.inf file are hidden. Disabling hidden files representation in the Explorer requires that a corresponding parameter in the log should be changed. Win32.HLLW.Gavir, Win32.HLLP.Whboy, Win32.HLLW.Creater can infect .exe files. Mail worms seem to have taken up the function of malware download. Win32.HLLW.Autoruner, for example, downloads Trojan.PWS.Wsgame stealing on-line games passwords and other malware - BackDoor.Paziruk, BackDoor.Cafezz.
Trojan.RedBrowser mobile phones malware along with its clones Adware.Freesms and Trojan.Webser – Symbian.Viver sprang up from oblivion. It originally disguised itself as multimedia codec sending SMS messages to the paid telephone number while being incapable of self-dissemination or self-installation on the targeted phones. The malefactors took over Trojan.Webser experience in social engineering and did their best.
Spam review
As far as spam events are concerned, May 2007 showed a splash of tourist spam activity. It came in timely as high season has been approaching and people started planning their holidays. Spam like this is considered a most “heavy” one – it comprises from 30 to 10 KB of graphics which makes it difficult to download such messages in slow traffic channels. Graphics include as a rule company contacts – phone numbers, e-mail – advertisement and shots of the advertised tourist area.Although summertime is within sight spam targeting financial directors and accountants with invitations to seminars devoted to taxation and legislation aspects has only slightly decreased comprising 67% of the overall Russian spam. The bulk of English spam (about 80%) is still owed to medical ads offering medicine, medical services or plastic surgery.
9474 virus entries were added to Dr.Web virus database in May 2007.
Below goes a short summary table online check for this month:
| Virus name | Quantity |
|---|---|
| VBS.Psyme.239 | 419 |
| Win32.HLLM.Limar | 335 |
| Trojan.Spambot | 166 |
| Trojan.Virtumod | 151 |
| Win32.HLLM.Wukill | 120 |
| Trojan.Peflog.31 | 98 |
| Win32.HLLM.Beagle | 78 |
| VBS.Igidak | 58 |
| Trojan.PWS.Maran | 48 |
| Win32.HLLP.Jeefo.36352 | 46 |
Here is also a summary table of most spread viruses detected on mail servers protected by Dr.Web in May 2007:
| Virus name | % of the general quantity |
|---|---|
| Win32.HLLM.Limar | 23.68 |
| Win32.HLLM.Netsky.35328 | 14.27 |
| Win32.HLLM.Beagle | 12.45 |
| Win32.HLLM.Perf | 6.88 |
| Win32.HLLM.MyDoom.based | 6.82 |
| Win32.HLLM.Netsky.based | 5.69 |
| Win32.HLLM.Graz 108951 | 4.69 |
| Win32.HLLP.Sector | 3.79 |
| Win32.Hazafi.30720 | 3.72 |
| Win32.HLLM.MyDoom.33808 | 2.26 |
| Win32.HLLM.Limar.based | 1.65 |
| Win32.HLLM.MyDoom.49 | 1.06 |
| Win32.HLLM.Generic.422 | 0.91 |
| Win32.HLLM.Netsky | 0.89 |
| Exploit.MS05-053 | 0.80 |
| Win32.HLLM.Beagle.pswzip 16938 | 0.73 |
| Exploit.IframeBO | 0.69 |
| Win32.Grum | 0.62 |
| Win32.HLLM.Oder | 0.56 |
| Win32.HLLM.Generic.391 | 0.54 |
| Other malicious programs | 7.03 |