Virus activity overview: Game robbers and other security events of October 2014
Virus reviews | Hot news | All the news | Virus alerts
October 31, 2014
Viruses
The standings of the malicious programs detected by Dr.Web CureIt! have remained virtually unchanged compared to previous months: the leading positions among the malware identified are still occupied by browser advertising plugins from the Trojan.BPlug amily and the adware installer Trojan.Packed.24524. As before, advertising Trojans occupy the top spots in the rankings of malware detected by Dr.Web CureIt! during October.
Dr.Web statistics servers present a somewhat different picture: the adware installer Trojan.Packed.24524 is in the lead. Compared with the previous month, the number of incidents involving this Trojan has increased by 0.15%. In addition, BackDoor.Andromeda.404, which accounts for 0.34% of the total number of malware programs identified in October, unexpectedly soared to the top of the rankings. In an infected system, this backdoor can execute instructions received from a remote server and download other malware from intruder-owned servers. The most common malware in October also includes Trojan.LoadMoney.336 which can install other programs, such as adware, in a compromised system. But the number of BackDoor.IRC.NgrBot.42 detections remained virtually unchanged compared with September and declined only by 0.02%. Also in October, the advertising Trojan programs Trojan.Zadved.4 and Trojan.Triosir.13 surfaced quite often in Dr.Web statistics.
Detected most frequently in October email traffic were BackDoor.Andromeda.404 (2.22%), the banking Trojan program Trojan.PWS.Panda.5676 (0.97%), and BackDoor.Andromeda.519 (0.88%), another modification of the undisputed leader of these rankings. It should be noted that in October, attackers often used mass mailings to distribute banking Trojans and malware designed to steal passwords and other confidential information. In addition to the aforementioned Trojan.PWS.Panda.5676, email attachments often included Trojan.PWS.Panda.655, Trojan.PWS.Stealer.13025 and Trojan.PWS.Stealer.13259. Combined, their detections reached 2.04% of the total number of mail traffic incidents in October.
As for botnets monitored by Doctor Web, no dramatic changes were registered over the past month. One of the Win32.Rmnet.12 subnets saw 251,500 bots contacting control severs from infected PCs, while in the second subnet that number reached 379,000. The average daily activity of the botnet composed of machines compromised by the file infector Win32.Sector has remained steady at around 57,000 active bots. The botnet built using BackDoor.Flashback.39 is still operational. Throughout October, an average of 16,530 requests were sent daily to command and control servers from infected machines running Mac OS X.
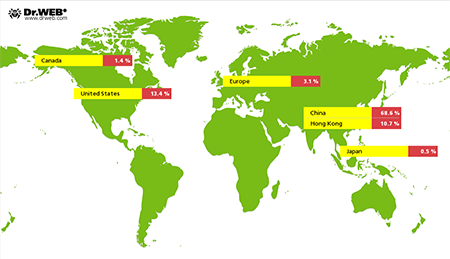
Earlier, Doctor Web reported on a malicious program for Linux that was added to the virus database as Linux.BackDoor.Gates. According to information acquired by Doctor Web's security researchers, in October the Linux.BackDoor.Gates botnet remained operational—the figure below shows the geographic distribution of DDoS attacks carried out with this botnet.
Steam game robbers
Many modern multiplayer online games cast users into virtual worlds that generate millions in profits for their makers. Gaming universes often have their own traditions and laws, codes of conduct, and economic models that enable players to obtain, exchange, and even sell in-game items for real money. In mid-September 2014, Doctor Web discovered and researched the program Trojan.SteamBurglar.1 which was stealing items like these from Steam users. Owned and maintained by Valve, Steam enables users to download and update their games via the Internet and keep up with news from the video gaming world.
However, intruders, opting to cash in on online game fans, did not stop with one malicious program: in October Doctor Web's virus analysts discovered a new Trojan with an almost identical payload. In addition to stealing game assets, Trojan.SteamLogger.1 could log keystrokes on an infected computer and forward the data to criminals. Fans of Dota 2, Counter-Strike: Global Offensive, and Team Fortress 2 came under attack.
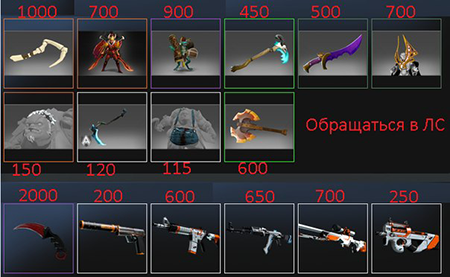
When launched on an infected machine, Trojan.SteamLogger.1 displays an image of in-game items and simultaneously engages in intense malicious activity.
Once information about the infected computer is transmitted to criminals, the malicious program will wait for the user to be authorised on the server and then extract information about their Steam account (the availability of SteamGuard, steam-id, and a security token) and transmit the data to criminals. In response, Trojan.SteamLogger.1 obtains a list of the accounts to which game items from the compromised account can be transferred. If automatic authorisation is disabled in the Steam settings, the malware creates a separate thread to run the keylogger. Information about logged key strokes will be sent to the attackers in 15-second intervals.
To search for inventory and valuable in-game items, Trojan.SteamLogger.1 uses such keywords as Mythical, Legendary, Arcana, Immortal, "DOTA_WearableType_Treasure_Key, Container, and Supply Crate. In other words, the Trojan attempts to steal the most valuable in-game items, chests and chest keys. Trojan.SteamLogger.1 also monitors whether players attempt to sell any of the virtual items themselves, and if they do, it automatically removes the items from the sale dialogue box. To sell Dota 2 chest keys, the malware authors have even created a special eStore.
For more information about this threat, please refer to our review article.
However, spreading malware is not the only technique adopted by criminals to cash in on gamers. They employ many other tricks. Officially, selling accounts is expressly prohibited on most gaming servers; however, this doesn't completely stop account buying and selling. When acquiring an account on a game server, a buyer wants to get not just the character with the maximum number of different "skills" and experience points, but also game items such as armour and mounts (sometimes quite rare ones), as well as the set of skills and professions that are available for this character. The more assets are available, the greater the account price will be. In some cases, it can exceed USD 500.
Fraudsters use various deception techniques. For example, a sold game account can be returned to criminals as soon as the buyer makes an initial request to the game’s technical support service. If the administration discovers that the account has been sold in violation of the rules, it will be blocked.
Also, swindlers can use chat to distribute phishing URLs, e.g., they can publish a fake announcement about a promo on offer from the game developer that requires participants to sign in with their game login and password on a third-party website or offer them malware in the guise of a program that will help them to enhance their characters' attributes.
They also actively use other methods to deceive gamers. You can find out more about these methods in a detailed article on Doctor Web's site.
Threats to Android
Last month, a large number of malicious applications once again threatened Android handhelds. For example, early October witnessed the discovery of the program Android.Selfmite.1.origin which was embedded into a tampered version of the official Google+ client app. Designed to generate illicit profits, this malware can place URL shortcut icons on the Android home screen. Depending on the device's location, the URLs lead to various sites involved in affiliate programs. The program can also advertise other applications on Google Play by opening corresponding sections of the catalogue. Furthermore, Android.Selfmite.1.origin can send SMS messages to all the contacts found in the phone book of an infected mobile device. The bulk of SMS dispatched is unlimited, and, depending on what command the command and control server issues, messages can contain a link to an advertisement or to applications the attackers are promoting, including a copy of the malware.
 |
 |
New ransomware programs continued to emerge. Android.Locker.54.origin (as classified by Doctor Web) is one such program whose payload is no different from that of other similar applications: on infected devices, it accuses users of viewing illegal adult content, locks the device screens, and then demands that a ransom be paid. It is different from other applications of this kind in that it can send short messages containing its download link to all phone book contacts—something that could help significantly increase the Trojan’s spread.
Also discovered in October was Android.Dialer.7.origin which belongs to a presently uncommon class of malicious diallers. Once on a mobile device, the dialler makes an unsolicited call to a premium number specified by criminals so that a certain amount of money is debited from the subscriber's account. More information about this malicious program can be found in a related news publication.
South Korean Android handhelds were hit again. In October, Doctor Web's security researchers registered over 160 spam attacks aimed at distributing all sorts of Android malware via unwanted SMS. One of the malicious programs used by criminals entered the virus database as Android.BankBot.29.origin. This is a common banking malware designed to steal sensitive information from customers of South Korean financial institutions. Similarly to other such programs, in order to resist its removal, Android.BankBot.29.origin requests access to the handheld’s administrator features. However, it does so in a peculiar way. The corresponding dialogue box is hidden under the malicious application's interface so that users may not even notice that they are granting Android.BankBot.29.origin extended privileges.
 |
 |
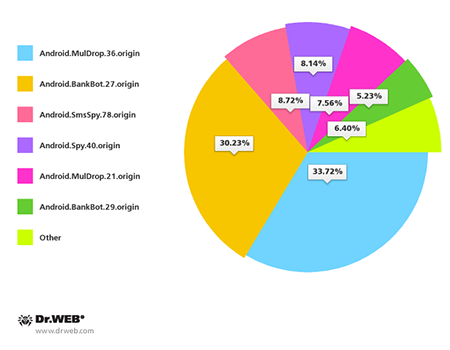
All in all, in the past month, mobile devices in South Korea were most frequently compromised by such malicious programs as Android.BankBot.27.origin, Android.MulDrop.36.origin, Android.SmsSpy.78.origin, Android.Spy.40.origin, Android.MulDrop.21.origin and Android.BankBot.29.origin.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live