SMS spam and Android Trojans in South Korea: A Doctor Web mobile security review for the third quarter of 2014
Virus reviews | Hot news | All the news | Virus alerts
October 30, 2014
The statistics acquired in the third quarter of 2014 indicates that Android hanhdleds remain one of the primary targets for criminals in South Korea: from July till September Doctor Web security researchers registered 338 spam campaigns aiming at infecting mobile devices residinig in this country.
South Korea SMS spam attacks in the third quarter of 2014.
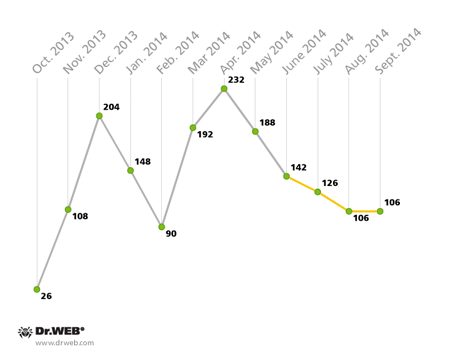
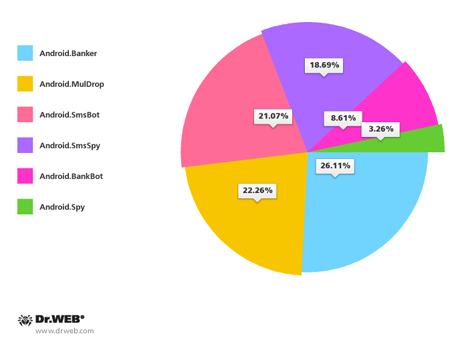
Compared with the second quarter, the number of attacks fell by almost 40%, however, it can hardly be good news, since most banking malware and spyware comprised the majority of applications spread in this way. Android.Banker programs accounted for 26,11% of the total threats distributed via spam. The percentage of other mallware families is as follows: Android.SmsBot – 21,07%, Android.BankBot – 18,69%, Android.SmsSpy – 8,61%, Android.Spy – 3,26%. In addition, a significant portion of threats distributed— 22.26%—is consittuted by the Android.MulDrop droppers. These are used by criminals to deliver other malware, which in most reported cases were the same banking spies. It indicates that criminals who distribute malware via SMS spam in South Korea are primarily focused on acquiring confidential information from owners of Android handhelds, gaining access to their bank accounts and conducting illegal transactions.
Families of Android malware distributed with SMS spam
in South Korea in the third quarter of 2014.
In addition to using malicious applications as containers for other malware in South Korea, criminals more and more often resort to other techniques to conceal threats and reduce probability of their detection by anti-virus software. Protecting malware with packers that encrypt their components is one of such techniques that becomes increasingly popular among cybercriminals. Also, they use all sorts of code obfuscation which produce a similar effect. Recent modifications of Android.SmsSpy.71.origin, which was discovered by Doctor Web's security researchers in January 2014 incorporate such concealment techniques. This malware intercepts SMS messages, steals the contact information, can bar calls and send short messages at given numbers or to all the contacts in the phone book upon a corresponding command from intruders. Similarly to other threats in South Korea, initially it didn't utilize and concealment tricks but over time it got more and more protected, Thus, the recent modifications of Android.SmsSpy.71.origin discovered in September, were encrypted by a complex packer and were spread using droppers that entered the virus database under the names Android.MulDrop.6 and Android.MulDrop.7.
 |
 |
However, cybercriminals also have other techniques in their arsenal. In response to new security features being introduced in Android, virus writers add new features into their programs to bypass these barriers. For example, Android.SmsBot.174.origin which is a bot that executes commands from intruders, hides incoming calls and short messages from a user, employs a peciuliar technique to do the latter. Starting with version 4.4, Android allows only one concurrent application to manage short messages. If the program is not a default SMS Manager, it can still hide notification about incoming messages, but the messages will still be saved in the Inbox and available to the user. To prevent this, Android.SmsBot.174.origin attempts to assign tself as the default SMS Messages by prompting the user to provide a corresponding confirmation. If successful, the malware becomes able to fully block not only incoming calls, but also SMS, including those from financial institutions. Yet the bot's ability to send various messages in accordance with attackers' instructions makes it a serious threat to users.
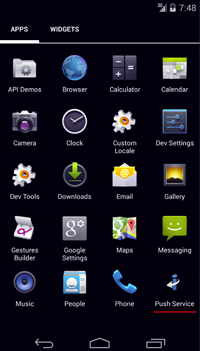 |
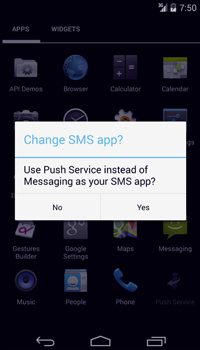 |
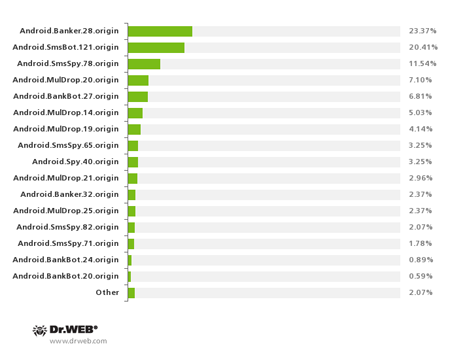
All in all, over the past 3 months, attackers unleashed more than 20 malicious applications onto South Korean Android users. The most common threats included Android Banker. 28.origin, Android. SmsBot.121.origin, Android. SmsSpy.78.origin, Android. MulDrop.20.origin and Android. BankBot.27.origin.
Android malware distributed with SMS spam
in South Korea in the third quarter of 2014.
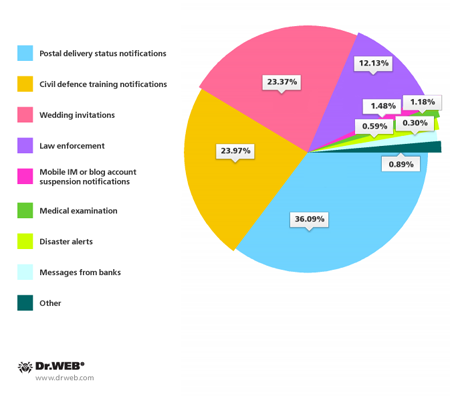
As mentioned earlier, all these programs were distributed with unwanted SMS messages containing malware download links in South Korea. To get users to install the programs onto their mobile devices, cybercriminals again actively used social engineering— most unsolicited messages dispatched by the intruders concerned worldly matters. For example, fake postal delivery notifications account for 36.09% of fraudulent SMS, the message on behalf of the Court or the police constitute 23.37%, bogus civil defence messages make up 23.97%, and fake wedding invitations represent 12.13% of the unwanted messages. In addition, criminals exploited other urgent topics, for example, they sent fake messages on behalf of banks and popular web services but they accounted for less than 5% of all reported spam incidents in South Korea.
Topics of fake short messages used to spread
malware in South Korea
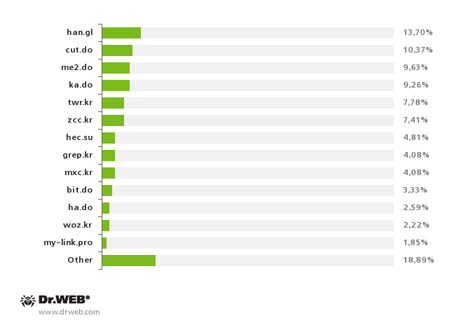
In 80% of incidents, URL shortening services were used to disguise the malicious download links found in the messages. Cybercriminals used 41 online services for shortening URLs and the most popularones included han.gl, cut.do, me2.do, ka.do, twr.kr and zcc.kr.
Most popular URL shortening services ,
used by criminals in the third quarter of 2014
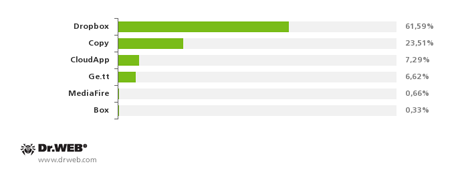
As before, most malicious programs distributed in South Korea resided on servers of known file hosting services. Criminals used this hosting option in 89% of the incidents. The most popular services employed by the criminals included Dropbox, Copy, CloudApp and Ge.tt with the Dropbox occupying the top notch. The remaining portion of maware was stored on criminals' sites crafted specifically to infect mobile devices of South Korean users.
File hosting services ,
used by criminals to spread malware in South Korea
Sites
hosting threats distributed in South Korea
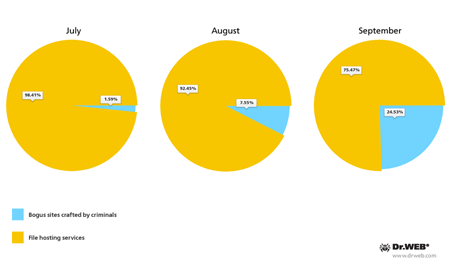
The continued interest in gaining access to confidential information and bank accounts of South Korean users on the part of criminals indicates that in the foreseeable future, attempts to infect mobile devices in South Korea will persist. Ever evolving malware and new techniques will surely be employed to compromise Android-powered devices in other countries too, so, to keep their handhelds secure, users are encouraged to exercise caution and install reliable anti-virus software.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live


