Malware overview: Threats to Mac OS X and other IT security hazards of September 2014
Virus reviews | Hot news | All the news | Virus alerts
October 2, 2014
Viruses
Statistics collected by means of Dr.Web CureIt! in September indicate that browser plugins that display annoying ads during web-surfing, namely, Trojan.BPlug.123 and Trojan.BPlug.100, were the most frequently detected on PCs. Scanning disks with this curing utility also often exposed the presence of the adware installer Trojan Packed.24524. This data has remained largely unchanged over the previous month.
According to Doctor Web's statistics server, September resembled August in that the adware installer Trojan.Packed.24524 was among the malicious programs most frequently detected. It accounted for 0.66% of the incidents detected on infected PCs. Note that in July, Trojan Packed.24524 was involved in 0.56% of the incidents, and in August that figure increased to 0.59%. BackDoor.IRC.NgrBot.42, whose first versions were discovered as early as 2011, ranked second in the detection statistics. Advertising Trojans, including Trojan.InstallMonster.953, Trojan.Zadved.4 and the like, also had high detection scores.
As far as mail traffic is concerned, the malicious downloader BackDoor.Tishop.122 has regained its previously lost leading position—the portion of detection incidents connected with this backdoor has increased from 1.15% to1.54% in the last thirty days. One of its modifications, BackDoor.Tishop.152, ranked second with a share of 1.03%. The third and fourth positions are occupied by Trojans that are designed to steal passwords and other confidential information—namely, Trojan.PWS.Stealer.4118 and Trojan.PWS.Turist.144. Other members of the BackDoor.Tishop family—BackDoor.Tishop.148 and BackDoor.Tishop.144–were also rather frequently spread as email attachments.
No noticeable changes were registered with regard to the activities of the botnets monitored by Doctor Web's security researchers. A subnet of a zombie computer network comprised of machines infected with Win32.Rmnet.12 was still experiencing around 265,000 requests daily to its command and control (C&C) servers, which is almost equal to the August figure. At the same time, the number of bots in the botnet deployed by means of Win32. Sector declined slightly over the past month: an average of 56,000-58,000 active nodes were being registered every 24 hours at the end of September against the average of 65,000 active nodes witnessed in August. Yet there’s been no thinning of the ranks when it comes to the number of Macs compromised by BackDoor.Flashback.39: on average, the number of bots in this botnet stayed at around 14,000 infected hosts. In addition, in September 2014 Doctor Web discovered a new Mac-based botnet created usingMac.BackDoor.iWorm.
Threats to Mac OS X
Although over two years have already passed since Doctor Web security specialists discovered the largest-ever botnet consisting of Macs infected by BackDoor.Flashback.39, the number of malware programs for machines manufactured by Applehas not declined. Moreover, there are indications that such threats are becoming more complex—their payload is increasing, and their makers are adopting state-of-the-art technologies. Apparently, the growing popularity of Mac OS X among users also makes it more popular among intruders. Thus, in the first autumn month of 2014, virus analysts simultaneously added into the Dr.Web virus database multiple entries related to malicious programs targeting machines designed by Apple. These entries included Mac.BackDoor.Ventir.1 and the spy Mac.BackDoor.XSLCmd which has been ported under Mac OS from Windows. They target machines running versions of Mac OS X released before 2013 (i.e., 10.8 and older). Criminals have posted on Google Analytics links for downloading malicious Java scripts that load Mac.BackDoor.XSLCmd onto targeted machines. In addition to performing common spyware functions, Mac.BackDoor.XSLCmd could log keystrokes on infected Macs and take screenshots and forward them to criminals.
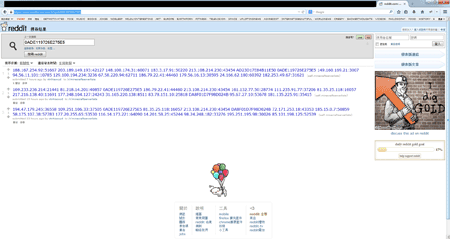
However, Mac.BackDoor.iWorm malware, used by attackers to deploy an active botnet, was of particular interest to security researchers. This backdoor can execute various commands which include detecting the infected Mac's OS version, getting the bot UID, sending a GET-query, downloading a file, opening a socket for an inbound connection, executing instructions received, and executing nested Lua scripts. It is noteworthy that this very sophisticated backdoor uses encryption extensively and acquires a list of control server addresses via the reddit.com search service by specifying the hexadecimal values of the first 8 bytes of the current date MD5 hash value as the search string. The reddit.com search returns a web page containing the list of botnet C&C servers and ports published by criminals in comments to the post minecraftserverlists under the account vtnhiaovyd.
The bot picks a random server from the first 29 addresses on the list and sends queries to each of them. Search requests to acquire the list are sent to reddit.com in five-minute intervals. More details about this malicious program and its operation can be found in a news post and detailed threat overview.
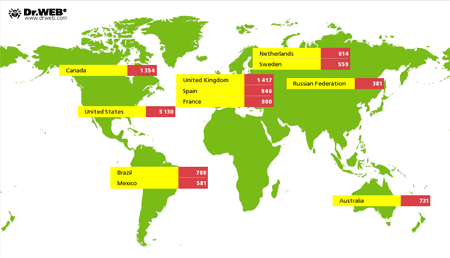
An analysis of the statistics collected by the Doctor Web security researchers monitoring the botnet indicates that, as of September 30, only 19,888 unique IP addresses associated with infected Macs appeared on the network. The USA accounts for 5,130 of them (25.8%); Britain ranks second with 1,417 (7.1%) addresses; and Canada ranks third with 1,354 IPs (6.8%). The late September 2014 geographical distribution of the botnet created with Mac.BackDoor.iWorm is shown in the following illustration:
Trojan for gamers
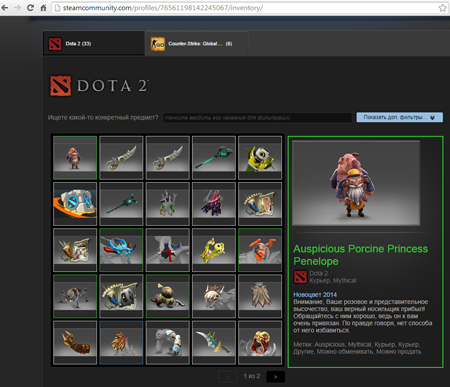
In early September, Doctor Web added into its virus databases the definition of the malicious program Trojan. SteamBurglar.1, which is designed to steal game items from Steam users. Owned and maintained by Valve, Steam enables users to download and update their games via the Internet and keep up with news from the video gaming world. Criminals spread Trojan.SteamBurglar.1 via the Steam chat and forums where they prompt users to view screenshots of weapons or other items supposedly available for purchase. While images of various game items were being displayed on the screen, the Trojan would search the machine's memory for the process steam.exe to extract information about game items. The malware used such keywords as ‘rare’, ‘immortal’ and ‘legendary’ to determine which items were the most valuable and stole them for later resale. The stolen game assets were transferred to a Steam account used by the criminals:
In particular, Trojan.SteamBurglar.1 stole items from a number of Dota 2 fans. Get more details about this threat from the review published by Doctor Web. As of this moment, several dozen representatives of this malware family have already been discovered.
Other security events in September
The overall security situation in September showed that virus makers didn't lose their enthusiasm for creating malware: attacks on PCs and handhelds involved brand-new programs as well as upgraded versions of known malicious applications and commercial applications injected with malignant payloads.
The new piece of encryption ransomware dubbed Trojan.Encoder.761 has been infecting PCs in Australia and Great Britain for two months. The ransom charged to decrypt compromised data is 350 pounds. Another 'cutting-edge' malicious program—Trojan.Encoder.759—is somewhat more moderate in its appetite and demands only around 100 dollars; however, delaying a payment incurs a fee for every 24 hours overdue. Both programs ask their victims to pay the ransom with bitcoins.
Online banking is also a primary target for intruders. Most often they orchestrate attacks on the client host which is a less secure element in customer-bank communications. To conceal the presence of malware on an infected PC, virus makers use modified versions of legitimate applications that incorporate a malicious payload. One such attack involved a modified version of a legitimate program called Program.RemoteAdmin. Attackers used the software to upload a banking Trojan and a key logger onto the target machine after which they were able to draw up and send a payment order instructing the bank to transfer funds from the victim's account to theirs.
In September, attackers used a new version of the Trojan BlackEnergy to collect data from hard drives belonging mostly to public and private companies in Poland and Ukraine. The Trojan's first modification was analysed in 2007 and was designed to launch relatively simple DDoS attacks. This simple DDoS Trojan horse has now evolved into a sophisticated piece of malicious software with a modular architecture which enables attackers to alter the program's functions depending on their objectives. New BlackEnergy modifications are detected by Dr.Web as Trojan.Siggen6.19887 and BackDoor.BlackEnergy.73.
In September, an entry for another IPhoneOS.PWS.Stealer. 2, modification was added to the virus database. This program targets jailbroken iOS handhelds. Initial samples were discovered in May 2014. The Trojan harvests the logins and passwords required to buy software in the App Store. It is believed that IPhoneOS.PWS.Stealer.2 gets onto devices when users download a Cydia Substrate tweaker or a program used for jailbreaking. IPhoneOS.PWS.Stealer.2 downloads and installs on the infected device a fake utility that allows an attacker to access the App Store and buy applications without the user's knowledge or consent.
At the end of September, backdoors targeting Linux—Linux.BackDoor.Shellshock.1 and Linux. BackDoor.Shellshock.2—were discovered. Attackers have developed their programs to exploit the ShellShock vulnerability (or CVE-2014-7169) which allows intruders to execute arbitrary commands on affected machines whose operating systems are based on the Linux kernel and feature the shell Bash (such as CentOS, Debian, Redhat, and Ubuntu). Affected devices include servers, modems, routers, cameras, and many other pieces of Internet-connected hardware with embedded operating systems. And the software for many of them never gets updated. The ShellShock vulnerability was assigned the highest level of risk.
Threats to Android
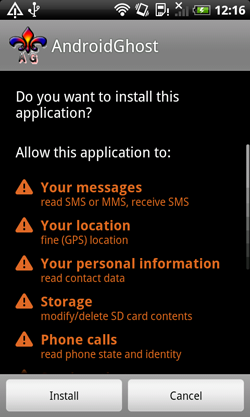
This past September, Doctor Web added to its virus database many new definitions for a variety of malicious software programs for Android mobile devices. Among them is yet another locker ransomware which has been dubbed Android.Locker.38.origin. Like most programs of its kind, the extortionist locks the infected mobile device's screen and demands a ransom to unlock it. But, in addition, the malware can lock an Android smart phone or tablet with a password, which complicates its neutralisation significantly. You can find more information about Android.Locker.38.origin in the corresponding publication on Doctor Web's site.
 |
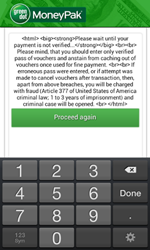 |
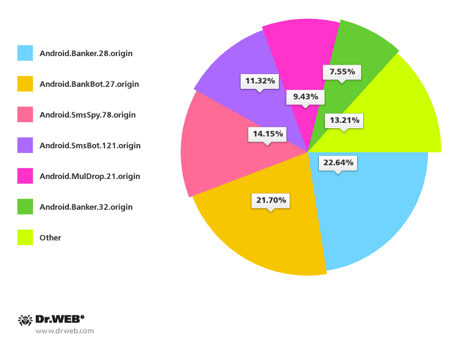
Banking Trojans constituted a significant portion of the malware for Android discovered in September. Many of them were used along with SMS spam for the now regular attacks against users in South Korea. All in all, Doctor Web's security researchers discovered over 100 spam campaigns aimed at distributing Android malware in South Korea. The most common malicious programs included Android.Banker.28.origin, Android.BankBot.27.origin, Android.SmsBot.121.origin, Android.SmsSpy.78.origin, Android.Banker.32.origin and Android.MulDrop.21.origin.
Chinese users had their share of cyber attacks too. In September, Doctor Web's security researchers discovered a spying Trojan that was added to the virus database as Android.Spy.130.origin. This malicious application steals various types of sensitive information such as SMS messages, the call history, and GPS coordinates. Also, it can covertly call specified numbers which effectively turns compromised smart phones or tablets into eavesdropping devices.
Discovered at the end of last month, Android. Elite.1.origin turned out to be the exact opposite of most threats to Android. In contrast to them, Android.Elite.1.origin is not designed for illicit profit or for stealing valuable information, but it still represents a grave danger. Once on a mobile device, this Trojan would format the memory card and interfere with the normal operation of a variety of applications. In addition, this malicious program would dispatch a bulk of short messages, which could deplete the user's mobile account. More information about this threat can be found in the relevant publication on Doctor Web's site.
Learn more with Dr.Web
Virus statistics Virus descriptions Virus monthly reviews Laboratory-live