New Trojan.Mayachok displays advertisements and tricks users
Real-time threat news | Hot news | All the news
August 25, 2014
Trojan.Mayachok.18831 is distributed via mass mailings. Once launched on an infected machine, this Trojan checks whether its copy is already present in the system and, if so, stops functioning. It also tries to detect the running processes of virtual machines or popular anti-virus software. This data will then be sent to a remote server belonging to criminals. Then Trojan.Mayachok.18831 gets information from the registry on the current Windows user's home directory, and tries to read from it the configuration file it has created; if unsuccessful, the Trojan uses the settings stored in its body. In addition, Trojan.Mayachok.18831 generates a second configuration file which contains all the information about the infected computer. This file will be sent to the remote server. In addition to executing basic malicious functions, Trojan.Mayachok.18831 can download from the Internet other Trojan programs, for example, Trojan.LoadMoney.15, as in the present case.
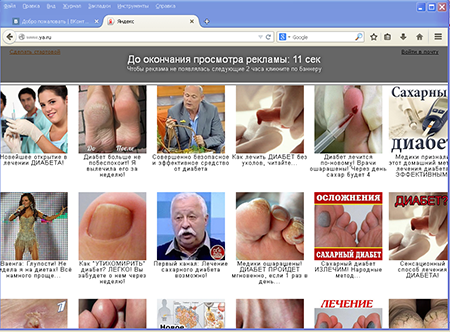
This malware runs under 32- and 64-bit versions of Windows, but depending on the OS bit, its algorithm may have a few functional differences. However, in both cases, Trojan.Mayachok.18831 has the same goal: it embeds extraneous content into web pages that have been loaded into these browsers: Microsoft Internet Explorer, Google Chrome, Mozilla Firefox, Opera, and Yandex.Browser. So, when a user visits certain Internet resources, the Trojan program displays annoying ads in the browser windows:
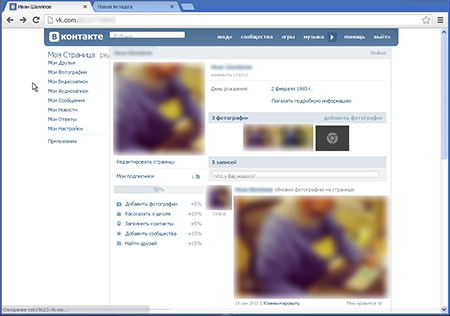
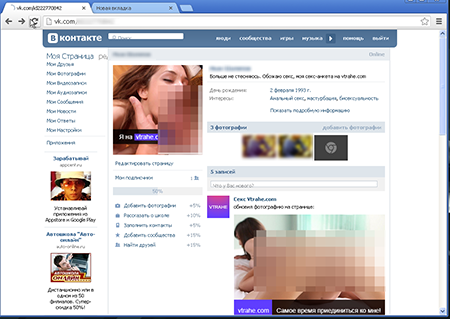
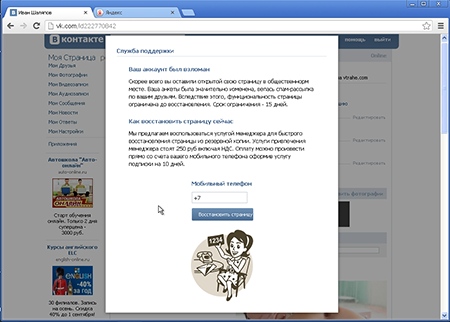
However, displaying ads was not enough for these virus writers. When the victim logs into a social networking site, Trojan.Mayachok.18831 displays obscene photos and misleading information about the victim's sexual preferences (below) instead of the usual pages of the victim's profile (top):
The Trojan program embeds its own content into the social network page so that the user's name and personal data (except for his/her interests) remain intact. Meanwhile, the malware gets the text and images from its own script. If the user tries to edit his/her profile, the "manager" will offer to restore the user’s hacked profile for 250 rubles:
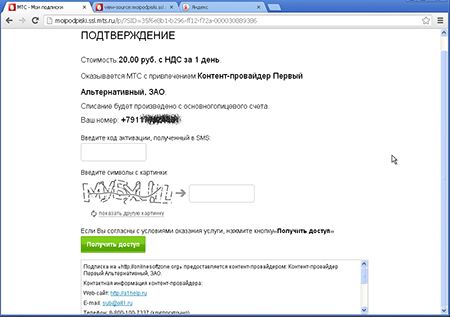
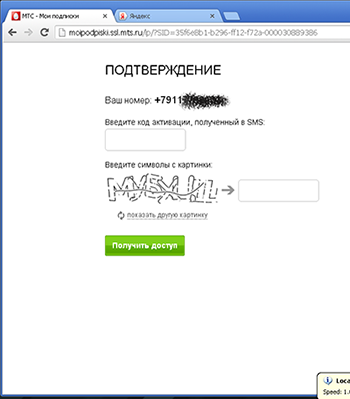
This form allows the victim to specify any phone number, not necessarily the one attached to the current user account. After clicking on Restore Page, a special subscription form generated by the mobile operator's website should appear on the screen. Usually, it looks like this:
However, Trojan.Mayachok.18831 makes some changes to this web page, so on the infected computer, the page is displayed like this:
After clicking on Gain Access, the victim will receive an SMS notifying them about their 20-ruble-per-day subscription to the site http://onlinesoftzone.org.
The Trojan can also take screenshots of the infected computer and send them to the criminals. The signature of the threat has been added to the Dr.Web virus database, so Trojan.Mayachok.18831 poses no serious threat to systems protected by Doctor Web products. However, Doctor Web recommends that users exercise caution when dealing with applications received as attachments in dubious emails.