Linux Trojan ported to Windows
Real-time threat news | Hot news | All the news
August 14, 2014
In May 2014, Doctor Web issued a report about a large number of Linux Trojans that are designed to mount DDoS attacks. The virus analysts examining the malware concluded that the Trojans had been crafted by Chinese virus makers. Not long ago, several new modifications of these Trojans were discovered. Despite the apparent similarity with previously found DDoS Trojans, these programs differed significantly from their predecessors. They are ported Windows versions of earlier Trojans.
Trojan.DnsAmp.1 is one such program which, in fact, is a Windows-compatible version of Linux.DnsAmp. It is installed into the system under the guise of the Windows service Test My Test Server 1.0 whose executable file is saved in the system folder under the name vmware-vmx.exe. When launched, Trojan.DnsAmp.1 sends information about the infected computer to the intruders' server and awaits the command to begin a DDoS attack. In addition, the Trojan may download and run other malicious programs. Certain features discovered by Doctor Web's researchers in the Trojan's code indicate that it has been written by the virus makers behind Linux.DDoS and Linux.BackDoor.Gates malware. For more information about how Trojan.DnsAmp.1 operates, please refer to the technical review describing this threat.
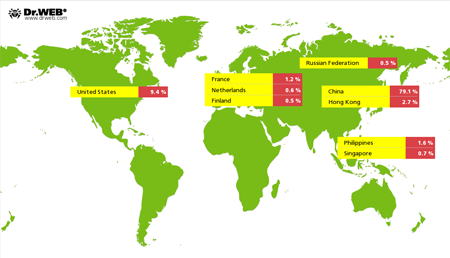
According to information received by Doctor Web's virus analysts monitoring infections from June 5 till August 13, the largest number of DDoS attacks involving Trojans of this family (especially Linux.BackDoor.Gates) were mounted on Chinese sites (28,093 attacks). Sites hosted in the United States ranked second. The geography of the attacks registered by Doctor Web is displayed in the illustration below.
The threat's signature has been added to the Dr.Web virus database, so Trojan.DnsAmp.1 poses no threat to systems protected with Dr.Web anti-viruses.